ReversingLabs Exposes TurkoRat: A Stealthy Infostealer Infiltrating the npm Platform
TurkoRat, a pernicious open-source infostealer, was found to have surreptitiously infiltrated the npm platform for two months before it was identified by researchers at ReversingLabs. With an intricate analysis of millions of suspicious packages through their Software Supply Chain Security platform, the team has revealed a number of malevolent behavioural combinations.
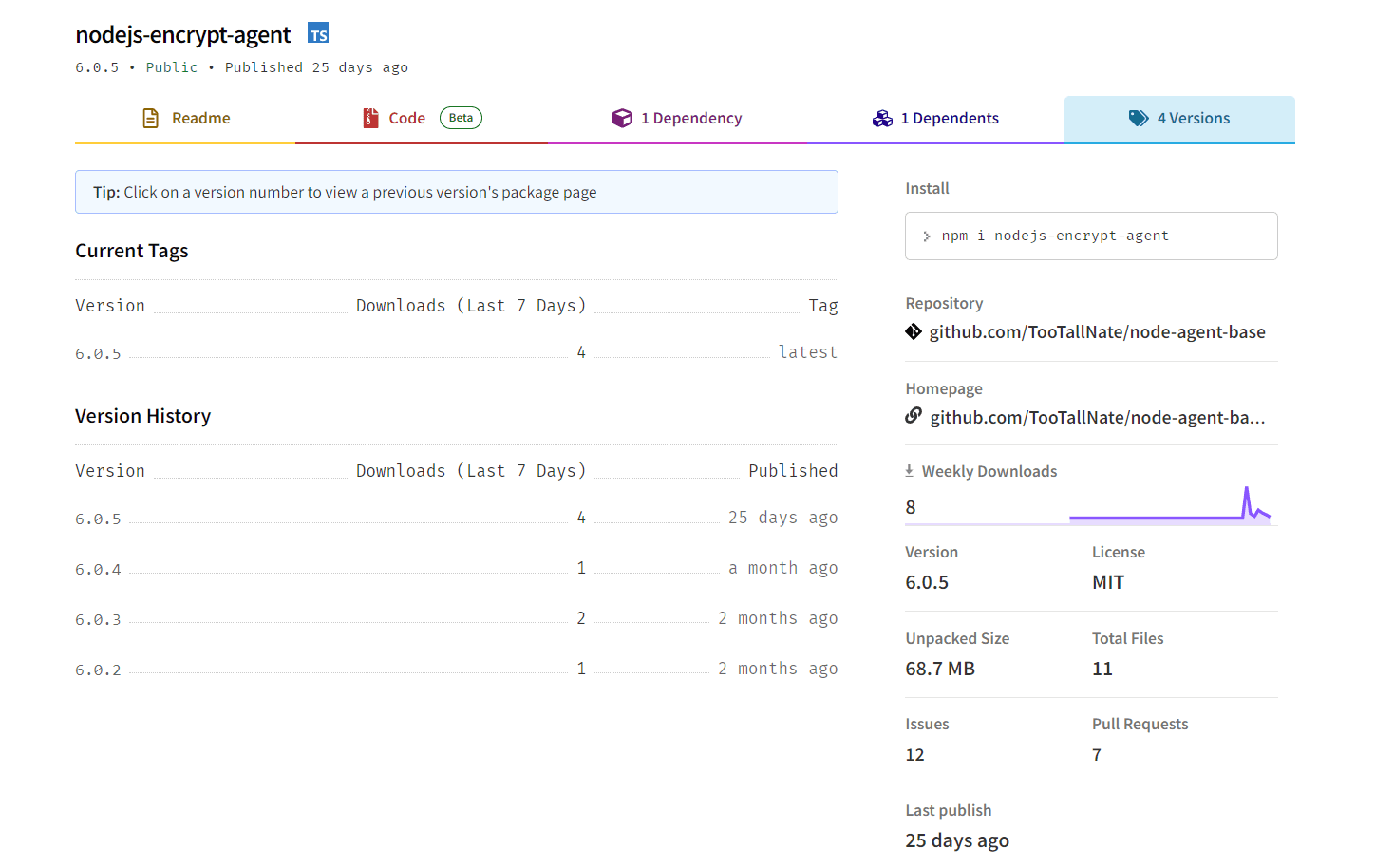
An ostensibly legitimate package, nodejs-encrypt-agent, was the first to arouse suspicion due to a series of anomalies. Despite its seemingly benign outward appearance, an in-depth analysis of the package using ReversingLabs’ Software Supply Chain Security revealed a darker reality.

Initial red flags were raised by the discordance between the package’s name on the npm page and in the readme.md file. Furthermore, the package bore an inordinately high version number for a package recently published – a crafty strategy employed by malevolent actors aiming to mislead hurried developers into downloading the latest iteration of the package.
However, the true nefarious nature of the nodejs-encrypt-agent package was exposed once the package’s internals were examined. Mirroring the functionality of the legitimate agent-base package it was squatting on, it harbored a hidden, malicious portable executable (PE) file. Executed shortly after the package is run, it enables the execution of commands, manipulation of Windows system directories, and tampering with DNS settings, amongst other sinister abilities.
The analysis conducted by ReversingLabs identified the PE as a malicious executable known as TurkoRat, an open-source malware family labeled a “stealer”, adept at pilfering everything from website cookies to crypto wallets. The open-source malware operates under the guise of being for ‘testing’ purposes, but can easily be manipulated for malicious intent.
The malevolent package encapsulates all the necessary files within a single executable, offering access to a virtual file system during runtime. All the files are embedded in this PE file, some of which were revealed to belong to dependencies, raising yet more alarm bells.
TurkoRat was also uncovered lurking in the initial versions of the npm package nodejs-cookie-proxy-agent, where it was disguised as a dependency imported into every file. This malicious package was promptly removed from npm after being discovered by ReversingLabs researchers.

These discoveries expose an unsettling reality where malevolent actors disguise their malicious codes within legitimate software packages. This sophisticated strategy, known as typosquatting, increases the probability of developers unwittingly downloading and using these harmful packages instead of the benign ones they intended. This investigation underscores the necessity for constant vigilance and robust security measures in an increasingly volatile digital landscape.





