Rocinante Banking Malware: Keylogging, Phishing, and Full Device Takeover
ThreatFabric, a prominent cybersecurity firm, has issued a warning about a new strain of banking malware dubbed “Rocinante,” currently targeting customers of Brazilian financial institutions. This sophisticated Trojan poses a substantial threat with its ability to conduct keylogging, execute phishing attacks, and establish remote access sessions on compromised devices.
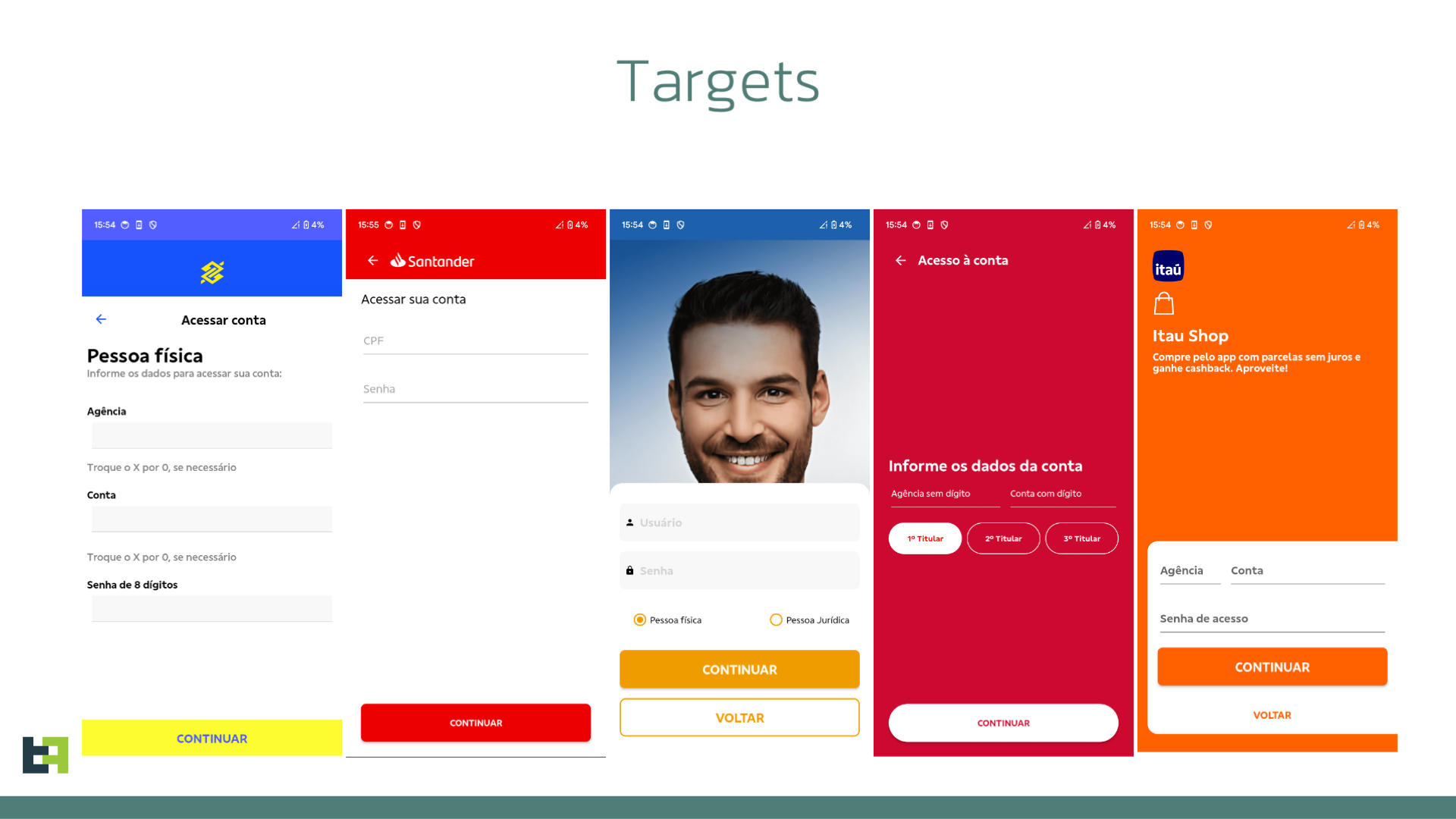
Rocinante primarily propagates through deceptive phishing websites masquerading as legitimate entities, such as security updates, courier applications, rewards programs, and even banking institutions themselves.
Rocinante distinguishes itself with a trifecta of capabilities designed to compromise its victims thoroughly. First, it employs keylogging via the Accessibility Service, capturing every keystroke and providing attackers with a wealth of sensitive information, from passwords to personal identification numbers (PINs).
Next, Rocinante utilizes phishing screens that mimic the interfaces of various Brazilian banks. These fake login pages are meticulously designed to trick victims into entering their personal and financial information, which is then exfiltrated to the attackers. The malware’s ability to disguise itself as legitimate banking apps or security updates only adds to its effectiveness, making it a formidable tool for cybercriminals.
Perhaps the most concerning aspect of Rocinante is its capacity for Device Takeover (DTO). By exploiting the same Accessibility Service privileges, the malware can establish full remote access to the infected device. This allows attackers to simulate touches, navigate through the device’s interface, and even initiate unauthorized transactions, all while maintaining persistent control over the device.
Rocinante’s sophistication is further evidenced by its use of multiple communication channels to relay stolen information and receive commands. The malware begins by registering the infected device with Firebase messaging, obtaining a unique token that is used in subsequent communications. It then establishes a connection with its Command and Control (C2) servers via HTTP and WebSocket protocols.
Interestingly, Rocinante also leverages the Telegram API to transmit exfiltrated personal identifiable information (PII) to the attackers. This use of Telegram not only facilitates communication but also underscores the evolving tactics of cybercriminals, who are increasingly adopting tools and platforms that are widely used and difficult to monitor.
Rocinante is not a static threat; it is under active development, with its authors continually refining and expanding its capabilities. In a notable development, parts of the malware’s codebase have been borrowed from the Ermac/Hook malware family, a notorious strain that originated outside of Latin America.
Rocinante’s ability to capture sensitive financial data, initiate unauthorized transactions, and maintain persistent control over infected devices makes it a significant threat to banking customers in Brazil.





