Russia-Linked Sandstorm Group Deploys New Kapeka Backdoor in Eastern Europe
A bespoke backdoor known as Kapeka (also dubbed KnuckleTouch) has been spotlighted for its sophisticated capabilities and implications in geopolitical cyber conflicts. First detected in mid-2022 and formally tracked by 2024, Kapeka’s emergence aligns closely with escalating tensions in Eastern Europe, especially targeting Ukraine’s critical infrastructure.
Background of Kapeka
Originally appearing in mid-2022, Kapeka was not widely recognized until two years later, largely due to its selective and limited-scope deployment, which rendered its activities relatively obscure. A report from Logpoint sheds light on this malicious tool, revealing its connections to the notorious Sandstorm Group, operated by Russia’s Military Unit 74455. Known under various monikers such as Telebots, Voodoo Bear, and Iron Viking, this group has a longstanding history of aggressive cyber operations dating back to its exploitation of zero-day vulnerabilities in 2014.
Operational Capabilities of Kapeka
Kapeka showcases an array of advanced functionalities crucial for deep infiltration and control. Its capabilities range from initialization and extensive system fingerprinting to intricate command and control (C2) communications and persistent task executions. This flexibility enables Kapeka to perform a variety of malicious activities stealthily and effectively. Furthermore, its high level of obfuscation complicates the efforts of cybersecurity professionals to analyze and counteract its deployment.
The Infection Chain and Persistence Techniques

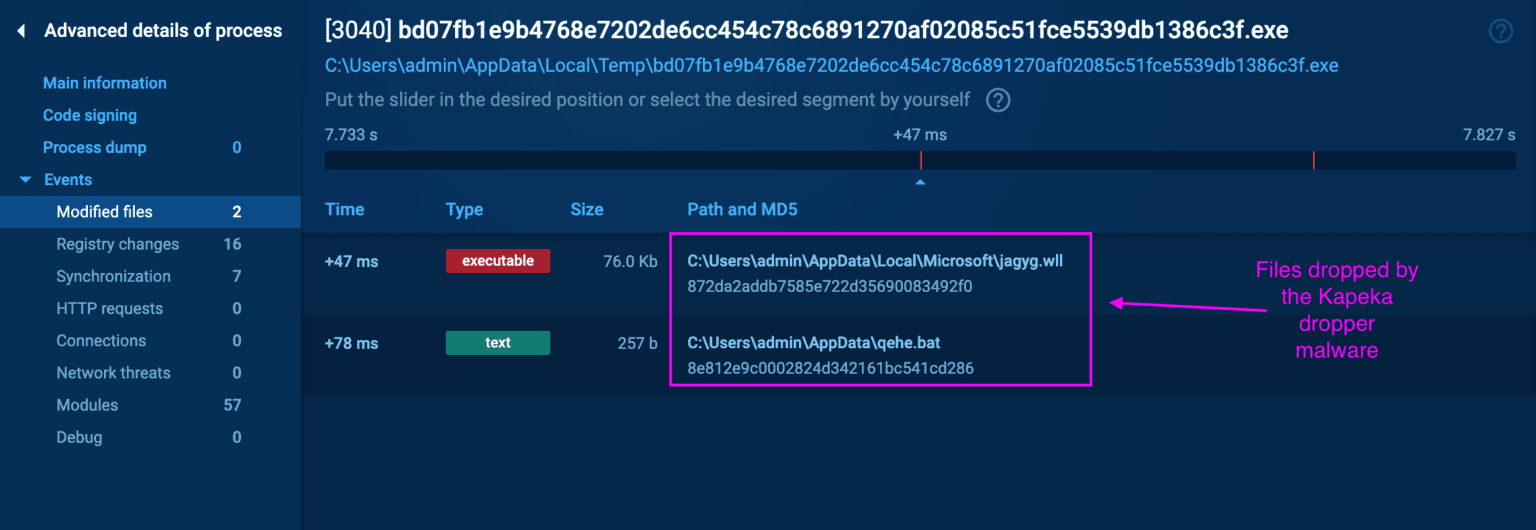
Image: Logpoint
The initial phase of a Kapeka attack involves a dropper malware that discreetly installs the backdoor into the system. This dropper, cleverly camouflaged as a harmless Windows Add-in file (.wll), is dropped into critical system directories, setting the stage for the malware’s persistent operations.
Once activated, Kapeka modifies system registries and sets up scheduled tasks to ensure it remains active across reboots and user logins, a technique that guarantees its long-term presence within infected systems.
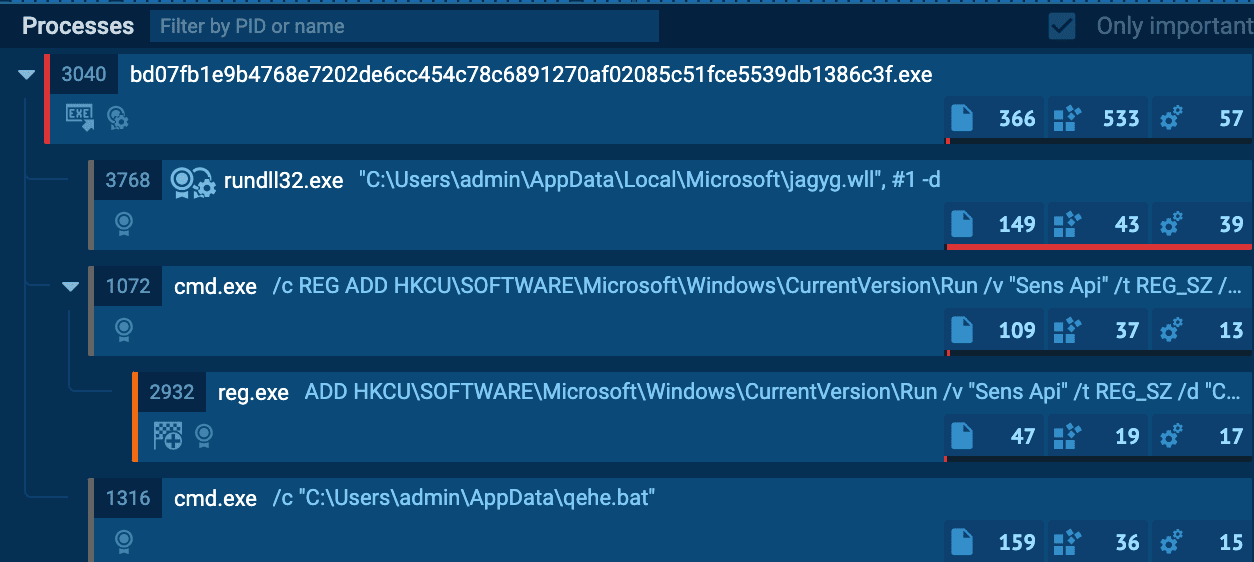
Dropper Process Tree | Image: Logpoint
Kapeka is not just a backdoor; it’s a comprehensive toolkit designed to infiltrate, spy, and exert control over compromised systems. It features advanced functionalities, including:
- C2 Communication: Utilizes JSON via the WinHttp 5.1 COM interface to maintain communication with its command and control servers.
- Task Execution: Capable of performing a variety of tasks as dictated by its operators, from file manipulation to executing arbitrary commands.
- Data Encryption: Employs AES-256 and RSA-2048 to secure its communications and protect its operations from detection and analysis.
Conclusion: Facing the Threat
The discovery and analysis of the Kapeka backdoor signify a pivotal moment in cybersecurity. As cyberattacks become increasingly complex, understanding and anticipating the moves of such sophisticated threats become paramount. Organizations are urged to leverage advanced cybersecurity tools to detect, analyze, and mitigate potential threats effectively. Regular security assessments and a proactive security stance are crucial in defending against the likes of Kapeka, ensuring that critical infrastructure and sensitive data remain safeguarded against the ever-evolving tactics of cyber adversaries.





