RustyAttr Trojan: Lazarus Group’s New macOS Malware Evades Antivirus with Ease
Researchers at Group-IB have discovered a new stealth technique employed by the North Korean APT group Lazarus, targeting macOS systems through a unique code-smuggling method. Known for its sophisticated cyber-espionage operations, Lazarus has now added custom extended attributes to its arsenal, allowing malware to evade detection by antivirus software.
Extended attributes (EAs) provide a way to attach additional metadata to files beyond standard attributes like size or timestamps. Leveraging EAs as a hiding spot, Lazarus’s malware avoids conventional detection methods. “The technique of hiding code in extended attributes effectively bypassed most antivirus scanners,” the report explains.
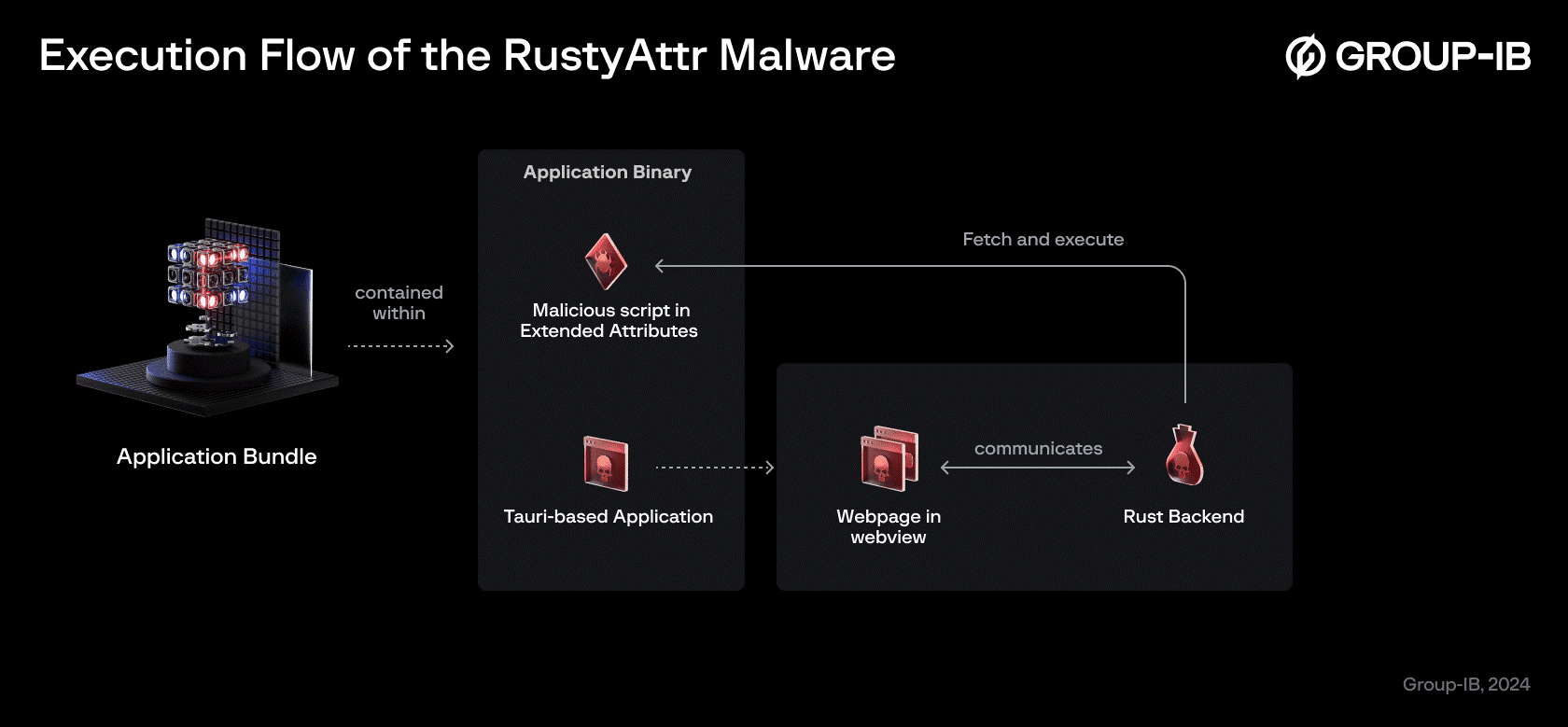
The researchers identified a new macOS Trojan, dubbed RustyAttr, which was developed using the Tauri framework. This framework enables desktop applications to have a web frontend while using Rust for backend tasks, a combination that Lazarus has exploited to embed malicious code into extended attributes. This method not only avoids detection but also requires minimal interaction from the user.
To execute the malware, Lazarus employs various decoys to distract victims while the malicious code operates in the background. For instance, one decoy displays a PDF titled Investment Decision-Making Questionnaire, with questions aimed at luring professionals in the finance and technology sectors. Another tactic involves a fake dialog box with a message stating, “This app does not support this version,” which appears benign but distracts the user while the malware operates.
When the Tauri application is launched, it attempts to render a webpage through a WebView, while executing hidden JavaScript that accesses the custom extended attributes. “If the attribute exists, no user interface will be shown; if the attribute is absent, the fake webpage will be shown,” the report details.
The Lazarus group’s use of extended attributes marks a novel approach that could pose challenges for future detection efforts. Although current samples of RustyAttr lack notarization, researchers warn that more robust versions could bypass macOS’s Gatekeeper protections if properly signed. “It is likely that some degree of interaction and social engineering will be necessary… however, this may not be the case for possibly other future samples,” researchers caution.





