The Stealthy Tech of Scheduled Task Tampering: A Deep Dive into the HAFNIUM Threat Actor’s Latest Tactic
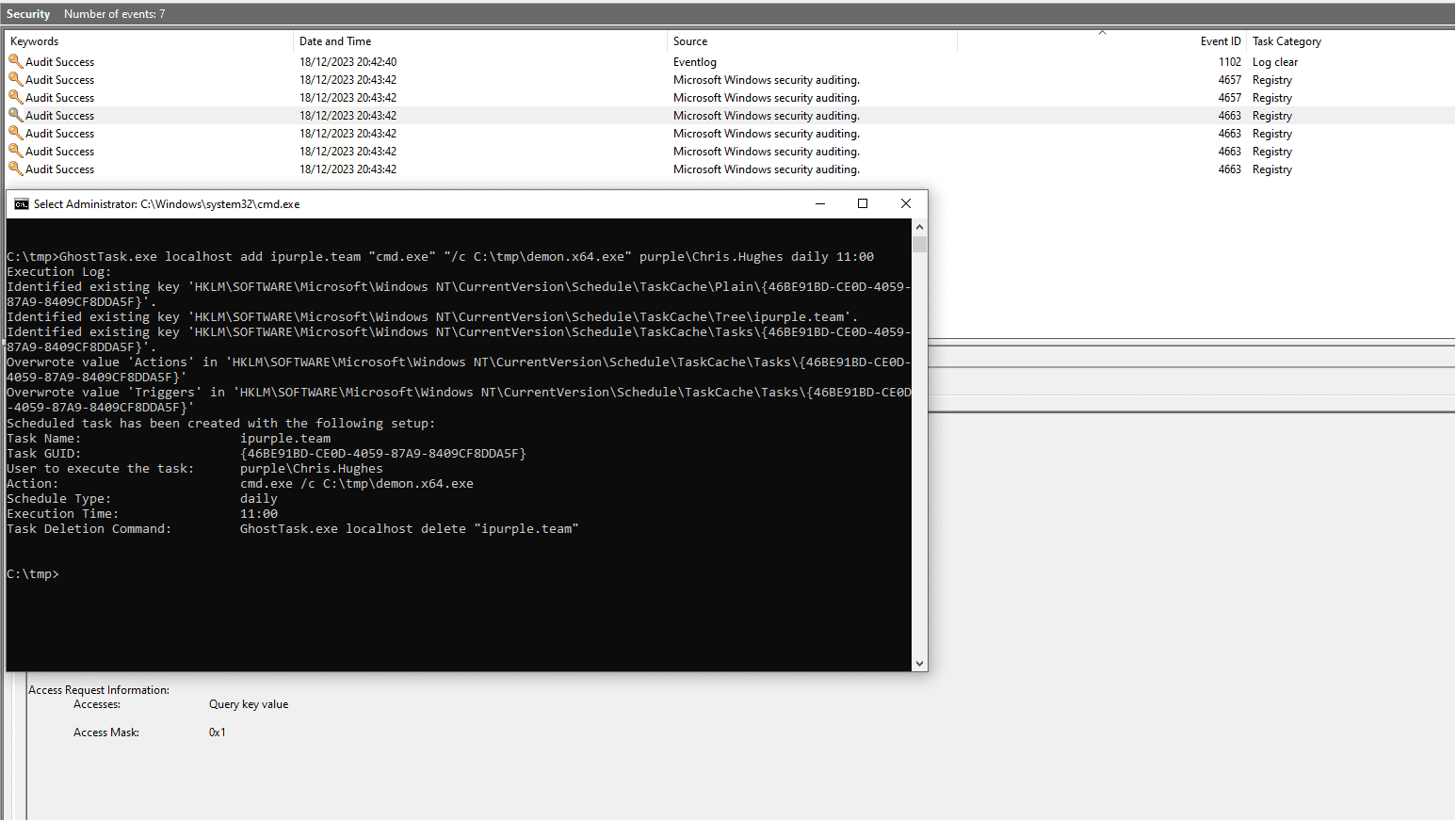
In the ever-evolving world of cybersecurity, the HAFNIUM threat actor has emerged with a novel and clandestine approach to manipulating scheduled tasks, a technique aimed at establishing persistence in compromised systems. This method centered around the manipulation of registry keys within their malware, Tarrask, marks a departure from traditional execution methods, creating a veil of stealth around their operations.
This technique, officially dubbed T1053.005, has been exploited by various threat actors. However, HAFNIUM’s unique approach has drawn the attention of Microsoft’s Detection and Response Team (DART) in collaboration with the Microsoft Threat Intelligence Center, shedding light on new ways to detect such covert operations.

Scheduled Task Tampering – GhostTask
The foundation of this technique lies in the modification of two specific registry keys: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks and HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree. These keys are crucial as they store information about scheduled tasks. A system restart or the execution of the schtasks utility is required for the changes to take effect, solidifying the tampered task’s presence in the system.
To combat this sophisticated form of attack, auditing of registry keys is essential. Microsoft recommends enabling registry audits from the Group Policy Management Editor to track any modifications to these critical keys. Events IDs 4657 and 4663 are particularly significant, as they log any changes made to the TaskCache key and provide visibility into the GUIDs of the modified tasks.
The Event ID 4657 discloses the GUID of the altered scheduled task, which, upon further investigation, can reveal the associated scheduled task. Interestingly, the Actions registry key, stored in binary blob format, contains information about the arbitrary command or beacon used by the attackers.
The sophistication of this tactic is further underscored by the fact that scheduled tasks created via registry key manipulation do not appear in the Task Scheduler. This covert operation requires elevated (SYSTEM) privileges, which HAFNIUM has been known to obtain through token theft techniques.
In addition to the standard Windows Event IDs, threat-hunting efforts can be aided by tools like ChainSaw, developed by WithSecure. This tool can run Sigma rules to identify events related to scheduled task tampering. However, it’s worth noting that a more advanced threat actor might evade detection by patching Event Tracing for Windows (ETW).
In conclusion, the advent of scheduled task tampering as a persistence mechanism underscores the need for continuous evolution in threat-hunting and detection strategies. By focusing on registry events and utilizing advanced detection tools and techniques, cybersecurity experts can stay one step ahead in this constant game of digital cat and mouse.
Via: Purple Team





