ScrubCrypt Deployed to Distribute VenomRAT and Powerful Array of Malware
In a recent analysis, FortiGuard Labs exposed a complex cyberattack campaign meticulously designed to infect victims with the potent VenomRAT trojan alongside a formidable collection of additional malware. Threat actors behind this operation are strategically leveraging the ScrubCrypt tool, notorious for its antivirus evasion capabilities.
How the Attack Unfolds

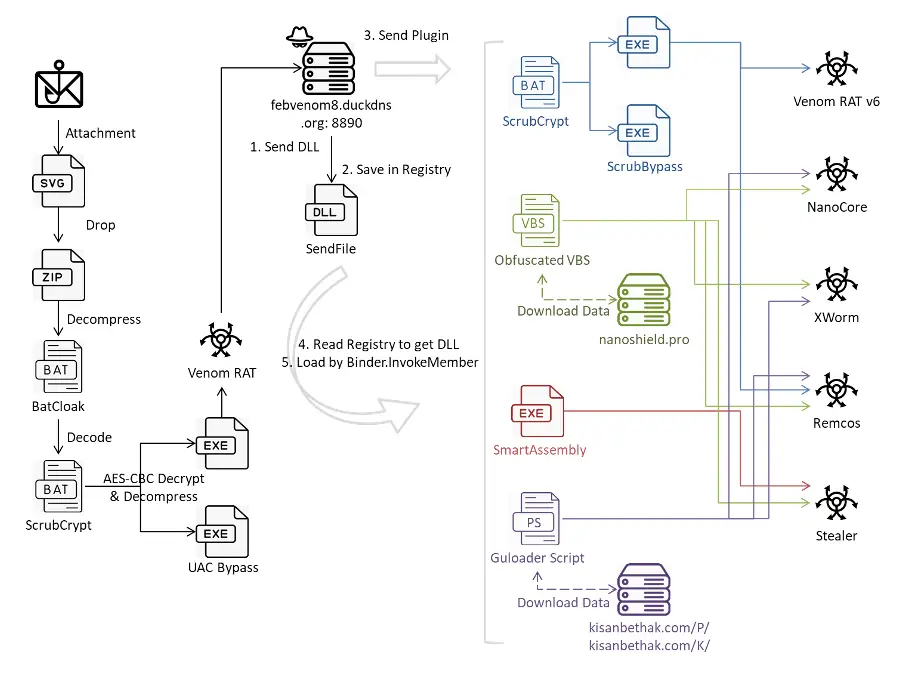
Attack chain | Image: FortiGuard Labs
The attack journey begins with an innocuous-looking phishing email, which baits the recipient with the promise of a delivered shipment, complete with an attached invoice. The attachment, however, is far from benign. Disguised as an SVG file, it encases base64-encoded data that, when opened, spawns a malicious ZIP file onto the victim’s system. This file is a testament to the cybercriminals’ ingenuity, obfuscated with the BatCloak tool to evade detection effortlessly.
As the baton passes to ScrubCrypt, the tool obscures its malicious payload with layers of junk strings, adding to the obfuscation. Employing AES-CBC decryption and GZIP compression, it decrypts and decompresses two payloads. The first establishes persistence and loads VenomRAT, ensuring the malware’s continued operation even in the face of potential discovery. The second payload is a masterclass in evasion, bypassing both AMSI and ETW—two of Windows’ foremost security measures.
VenomRAT, a derivative of the infamous Quasar RAT, emerges as the centerpiece of this cyber-attack. Beyond its primary function of granting attackers remote access to compromised systems, VenomRAT communicates with a command and control (C2) server to fetch additional plugins. These plugins, ranging from keyloggers to stealers specifically targeting crypto wallets, are custom-tailored to the attackers’ needs, further enhancing the malware’s lethality.
VenomRAT and its Plugins: What They Do
- VenomRAT: This remote access trojan grants attackers extensive control over infected systems. It can steal data, log keystrokes, and carry out other malicious activities.
- Remcos: Another powerful RAT used to take screenshots, record keystrokes, and steal sensitive information.
- XWorm: A worm designed to spread through removable drives, infecting other Windows machines.
- NanoCore: A well-known RAT providing attackers with remote access capabilities.
- Crypto Wallet Stealer: This specialized malware targets cryptocurrency wallets, aiming to steal valuable digital assets.
The Threat Continues to Evolve
This attack campaign serves as a harsh reminder of how relentless and sophisticated cybercriminals have become. To stay ahead, it’s vital to prioritize cybersecurity awareness, regularly update defenses, and remain informed about emerging threats.