Sharp Stealer: New Malware Targets Gamers’ Accounts and Online Identities
A new threat has emerged in the cybercrime world, specifically designed to prey on the lucrative gaming community. Security researchers from G DATA have analyzed “Sharp Stealer,” a malware family that steals login credentials, payment information, and even in-game items from unsuspecting players. This new malware family, including “Sharpil RAT.exe” and “Sharp Stealer,” has recently been reported by threat researcher Yogesh Londhe, sparking concerns about its capabilities and target demographics.
The initial discovery of “Sharpil RAT.exe” revealed a C#-written application that functions stealthily in the background, attempting to connect to a Telegram bot. This bot acts as a conduit for attackers to command the malware remotely, extracting vital information from systems. It specifically targets data from popular browsers and even gaming servers, like Minecraft’s “Vime World.”

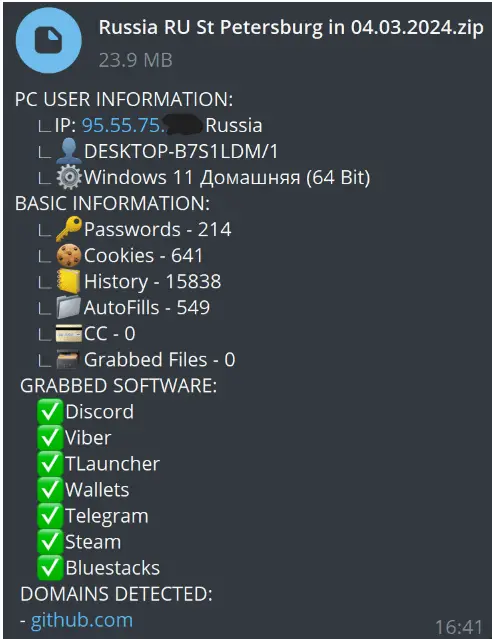
Zip archive with the stolen data transmitted to the Telegram channel | Image: G DATA
The RAT’s primary method, “ParseLastMessage,” processes commands received via JSON from the Telegram API, triggering data theft based on received instructions. Despite being labeled by its developers as a remote access trojan (RAT), its functionalities align more with those of a data stealer, focusing on extracting rather than controlling infected systems.
Further investigation into the malware family led to the discovery of “Sharp Stealer,” which shares coding similarities with Sharpil RAT, indicating a common origin. Sharp Stealer is crafted using the Ionic Framework and features cryptographic functions from the BCrypt library, showcasing an advanced approach to data security evasion.
The malware is designed to target a wide array of data points:
- System Information: Hardware specs, IP address, and screenshots are collected, potentially aiding in tailoring attacks.
- Browsers: Credentials and cookies from common browsers pose a serious risk of account takeovers.
- Gaming Platforms: Epic Games, Steam, Roblox, Minecraft among others – account details and in-game items are valuable commodities on the black market.
- Messengers & Discord: Stealing active Discord sessions and payment information enables social engineering attacks and fraudulent money transfers.
- Crypto Wallets: A growing target for cybercriminals looking to drain victims’ digital currency holdings.
The choice to target gaming platforms and associated software is particularly noteworthy. Gaming accounts often hold significant value, both in the form of in-game items and the personal data associated with them. The sale of compromised gaming accounts is a lucrative market in cybercrime circles, making them a prime target for new infostealers like Sharp Stealer.
Evidence points to a Russian-speaking developer selling Sharp Stealer for as little as $10. The project’s Telegram channel suggests it’s a relatively new development, yet the stealer’s specific focus on gamers makes it a threat to be taken seriously.
The motivation behind Sharp Stealer is likely financial profit. In-game items, rare skins, and even compromised accounts fetch significant prices on underground marketplaces. This lucrative market drives continued innovation among cybercriminals targeting the gaming sector.





