Simple script to check if your Linux machine is vulnerable to #Meltdown
Am I affected by Meltdown?! Meltdown (CVE-2017-5754) checker
What am I?
Proof-of-concept /
Exploit /
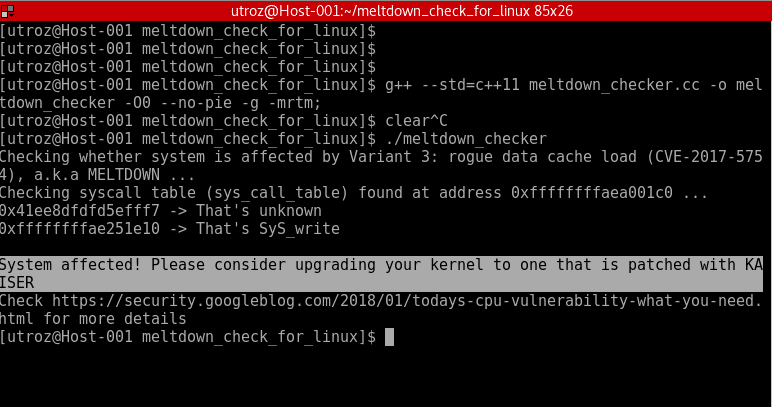
Checks whether the system is affected by Variant 3: rogue data cache load (CVE-2017-5754), a.k.a MELTDOWN.
*** Only works on Linux for now ***
How does it work?
It works by using /proc/kallsyms to find system call table and checking whether the address of a system call found by exploiting MELTDOWN match the respective one in /proc/kallsyms.
What to do when you face this error “Unable to read /proc/kallsyms…”
That’s because your system may be preventing the program from reading kernel symbols in /proc/kallsyms due to /proc/sys/kernel/kptr_restrict set to 1. The following command will do the trick:
sudo sh -c “echo 0 > /proc/sys/kernel/kptr_restrict”
Please open an issue if you have an idea on how to fall back to another approach in this scenario.
Getting started
git clone https://github.com/raphaelsc/Am-I-affected-by-Meltdown.git
cd Am-I-affected-by-Meltdown
make

Copyright (c) 2018 Raphael S. Carvalho <raphaelsc@scylladb.com>
Source: https://github.com/raphaelsc/





