SLOW#TEMPEST Campaign: Securonix Uncovers Sophisticated Cobalt Strike Attack Targeting Chinese Users

The Securonix Threat Research team has revealed a recently uncovered cyber espionage campaign, dubbed SLOW#TEMPEST that is specifically targeting Chinese-speaking users intending to deploy Cobalt Strike implants – a notorious tool used for remote access and control of compromised systems.
The SLOW#TEMPEST campaign is characterized by its use of malicious ZIP files, which are distributed through phishing emails designed to lure victims with seemingly legitimate content. These ZIP files, often password-protected to evade antivirus detection, contain shortcut (.lnk) files masquerading as document files. Once the user opens the ZIP file and executes the LNK file, the malicious code begins its execution, setting the stage for a full-blown attack.
Analysis of 违规远程控制软件人员名单.docx.lnk | Image: Securonix
The phishing emails used in this campaign were specifically crafted to target individuals within China, as evidenced by the Chinese language used in the file names and the nature of the lures. The command and control (C2) infrastructure was hosted by Shenzhen Tencent Computer Systems Company Limited, a major Chinese-owned company, further indicating that the primary target of this campaign is indeed within China.
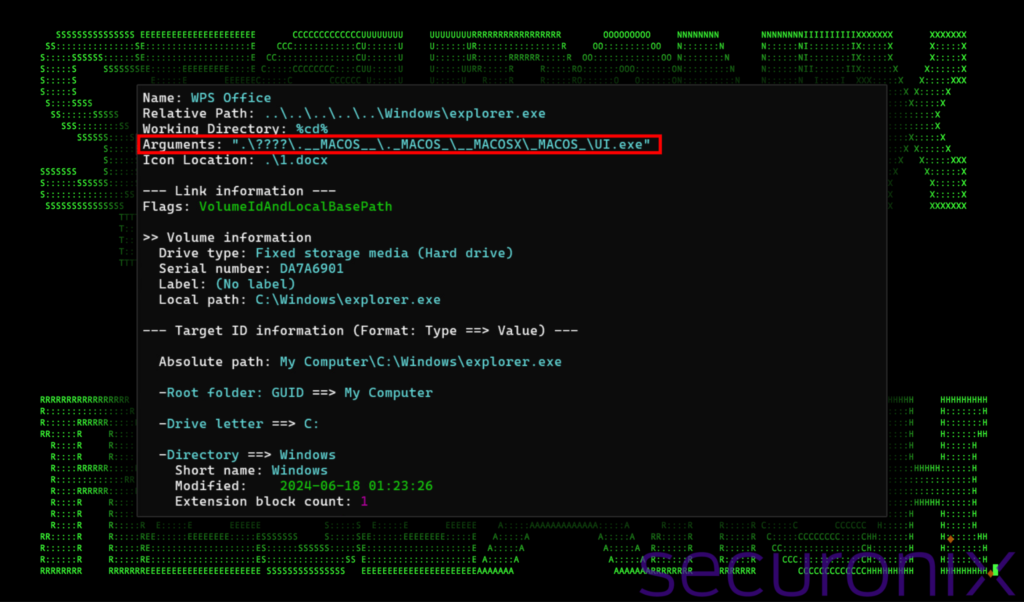
The attack chain begins with the execution of the LNK file, which triggers the launch of a legitimate Microsoft-signed executable named “LicensingUI.exe” that has been renamed to “UI.exe.” This file, normally responsible for software licensing user interfaces, becomes the vehicle for a DLL hijacking technique. The attackers replace a legitimate DLL, “dui70.dll,” with their own malicious version, effectively injecting Cobalt Strike into the system.
This method of DLL hijacking using LicensingUI.exe appears to be previously undocumented, highlighting the advanced nature of the attackers behind SLOW#TEMPEST. Once the Cobalt Strike implant is executed, it establishes a beacon to the C2 server, allowing the attackers to maintain persistent and stealthy access to the compromised system.
With the initial compromise successful, the attackers wasted no time in expanding their control over the network. They created a staging directory in the Windows Temp folder, where they downloaded a suite of tools designed for further reconnaissance and exploitation. These tools included:
- fscan.exe: A red-teaming scanner used to identify live hosts and open ports.
- netspy.exe: A network reconnaissance tool for capturing network traffic and scanning for vulnerabilities.
- sharpdecryptpwd.exe: A utility for dumping cached credentials from applications.
- BloodHound: A powerful tool for mapping out Active Directory relationships, used to identify and exploit potential pathways for privilege escalation.
The attackers also set up a scheduled task named “windowsinspectionupdate” to execute their malicious code at regular intervals, ensuring their foothold in the system even after reboots. Additionally, they elevated the privileges of the built-in Guest user account, transforming it into a powerful backdoor with administrative capabilities—a tactic that allows them to remain hidden while maintaining control over the system.
After gaining a stronghold within the network, the attackers began moving laterally, using RDP (Remote Desktop Protocol) and credential theft tools to access other systems. They deployed tools like Mimikatz to harvest credentials, which were then used to authenticate and pivot across the network. The attackers also disabled Windows’ “Restricted Admin Mode” to reduce their visibility and increase the effectiveness of their RDP connections.
The final stages of the attack involved deploying BloodHound to conduct a thorough reconnaissance of the Active Directory environment. The data collected was compiled into .json files and exfiltrated for offline analysis, providing the attackers with detailed insights into the network’s structure and potential vulnerabilities.
While the attackers behind SLOW#TEMPEST demonstrated a high level of sophistication, they were not without flaws. Securonix researchers noted several OPSEC (Operational Security) failures, including captured Cobalt Strike commands that revealed usernames and system information related to the attacker’s infrastructure. These failures provided valuable clues that helped trace the attack back to infrastructure hosted in China, including resources provided by Tencent Cloud.





