In a recent campaign targeting First Ukrainian International Bank (pumb[.]ua), G DATA security researchers uncovered a deeply layered and technically advanced malware chain. At the center of this operation is SmokeLoader, a well-known and powerful modular loader that’s been enhanced with stealthy execution tactics and a lesser-known but increasingly popular intermediary—Emmenhtal Loader (aka EmmenHTAl or Peaklight).
This analysis exposes a refined infection strategy—one that combines social engineering, Living off the Land Binaries and Scripts (LOLBAS), and anti-analysis tactics to quietly deploy multiple malware stages without raising alarms.
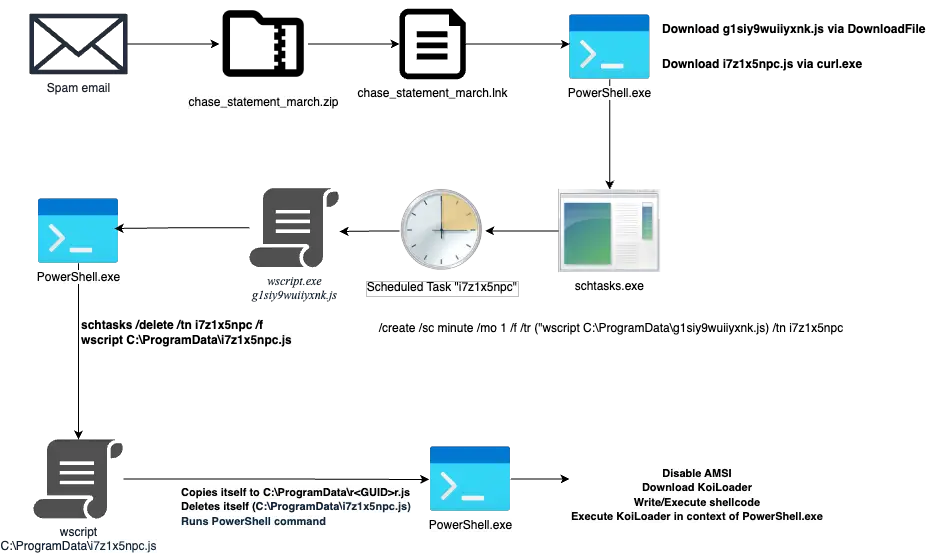
The attack begins with a phishing email masquerading as a payment confirmation, containing an attachment named Платiжна_iнструкция.7z (translated: “Payment_instruction”). Inside the archive:
- A bait PDF mimicking financial documents
- A PDF shortcut (.lnk) designed to download additional payloads from a remote server
The report highlights the attackers’ continued use of archive-based evasion techniques, noting that “In previous SmokeLoader campaigns, the threat actors exploited a 7-Zip zero-day vulnerability to bypass security checks using double-archived files, allowing malware execution.” Although this campaign does not use the same exploit, it demonstrates the attackers’ persistence in using archive-based evasion.
The .lnk file activates a PowerShell script that leverages Mshta, a legitimate Windows binary for executing HTML Applications. It downloads a malicious .hta file, blending into native system behavior to remain undetected.
“This is a common LOLBAS technique… allowing fileless execution and minimal visibility,” the researchers note.
To further conceal the operation, the attackers use a modified DCCW.exe (Windows Display Color Calibration Wizard) as a loader, embedding JavaScript within the binary to execute malicious payloads with minimal footprint.
Emmenhtal, the loader stage, is cloaked in a crafted HTA file with a minimized window state and no taskbar presence. JavaScript embedded within the loader uses eval(erc) to execute additional obfuscated code.
“The executed variable contains another charCode-encoded script… which will be executed via wscript shell.”
The script decodes and launches a PowerShell downloader, which checks for two files—invoice1202.pdf and putty1202.exe—and either executes them or retrieves fresh copies if missing.
The final stage drops SmokeLoader, a versatile malware platform known for:
- Delivering secondary payloads
- Stealing browser and system credentials
- Injecting into legitimate processes
- Executing commands from remote C2 servers
- Employing anti-debugging and anti-analysis defenses
“This file is a SmokeLoader malware… using .NET Reactor for obfuscation and packing,” G DATA confirms.
The use of .NET Reactor—more common in modern stealers—reflects a shift in malware tooling preferences, as attackers seek stronger evasion through commercial protectors.
G DATA also noted overlap in infrastructure and TTPs with other malware families, including Blustealer and Lumma, suggesting potential collaboration or shared platforms among cybercriminal operators.
A Wireshark packet capture confirms outbound connection attempts to 88[.]151[.]192[.]165, further indicating command-and-control activity tied to SmokeLoader’s deployment.
“The availability of these feature-rich new loaders that are offered through Malware-as-a-Service (MaaS) enables threat actors to be more creative in customizing their attack chain,” the researchers conclude.
Related Posts:
- Malicious Go Packages Target Developers with Hidden Loader Malware on Linux and macOS
- C&C in the Clouds: OilRig Group Hijacks Microsoft Services for Espionage
- SocGholish Malware Facilitates RansomHub Distribution
- Rust Beacon Deploys Cobalt Strike in South Korean Cyber Intrusion Campaign
- Squid Werewolf APT Masquerades as Recruiters in Espionage Campaign Targeting Key Employees