Software Supply Chains Threatened: Nexus Repository CVE-2024-4956 Flaw Exposed
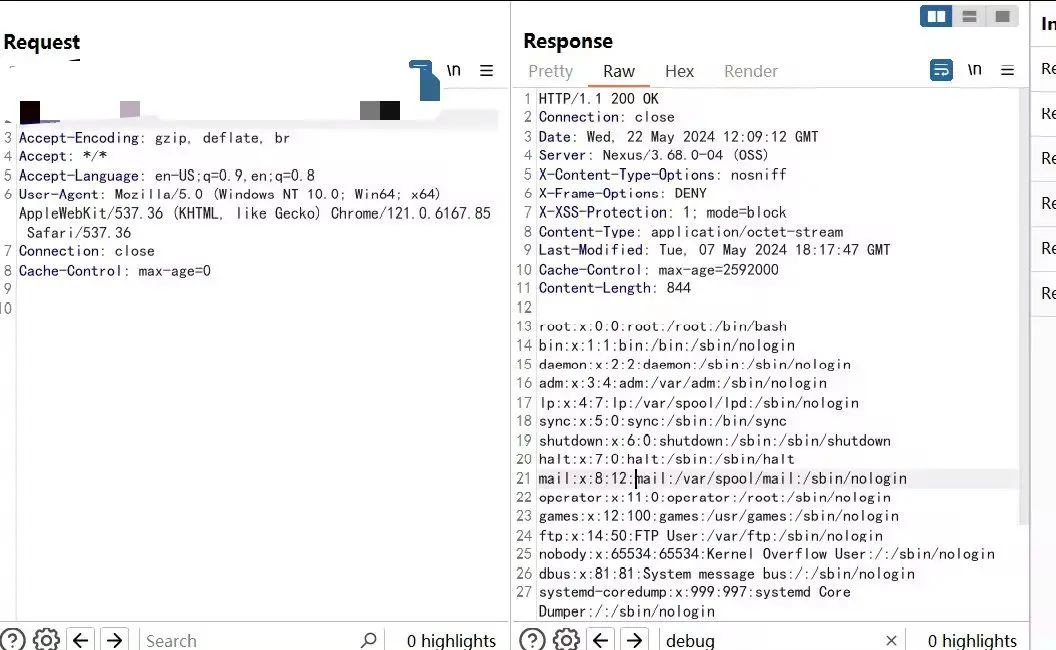
Sonatype, a leading provider of software supply chain management solutions, has issued a security advisory regarding a critical vulnerability (CVE-2024-4956) in Nexus Repository, its widely used artifact repository manager. The vulnerability, classified as a path traversal flaw, could allow attackers to access and download sensitive system files without authentication, potentially exposing confidential data and compromising the security of software development pipelines.

The vulnerability has been assigned a CVSS score of 7.5, indicating a high severity level. Successful exploitation could enable attackers to gain unauthorized access to sensitive system files, including configuration data, credentials, and other proprietary information. This could have far-reaching consequences for organizations that rely on Nexus Repository to manage their software artifacts.
All previous versions of Sonatype Nexus Repository 3.x OSS/Pro up to and including 3.68.0 are affected by this vulnerability.
The vulnerability was discovered and responsibly reported by Erick Fernando Xavier de Oliveira through Sonatype’s Bug Bounty Program. Security researcher @chybeta independently reproduced the CVE-2024-4956 vulnerability.

Sonatype strongly urges all users to upgrade to Nexus Repository OSS/Pro version 3.68.1 immediately. This version contains a patch that addresses the path traversal vulnerability and mitigates the associated risks.
For organizations that cannot immediately upgrade, Sonatype has provided two alternative mitigation options:
- Edit jetty.xml: This involves removing a specific line from the jetty.xml configuration file, preventing the exploitation of the vulnerability. However, this also disables the loading of files from the (installdir)/public directory.
- AWS WAF Core Rule Set: If Nexus Repository is protected by AWS WAF rules, enabling the GenericLFI_URIPATH rule can mitigate the risk of exploitation.





