Sophisticated Cyber Espionage: Earth Baxia Uses CVE-2024-36401 and Cobalt Strike to Infiltrate APAC
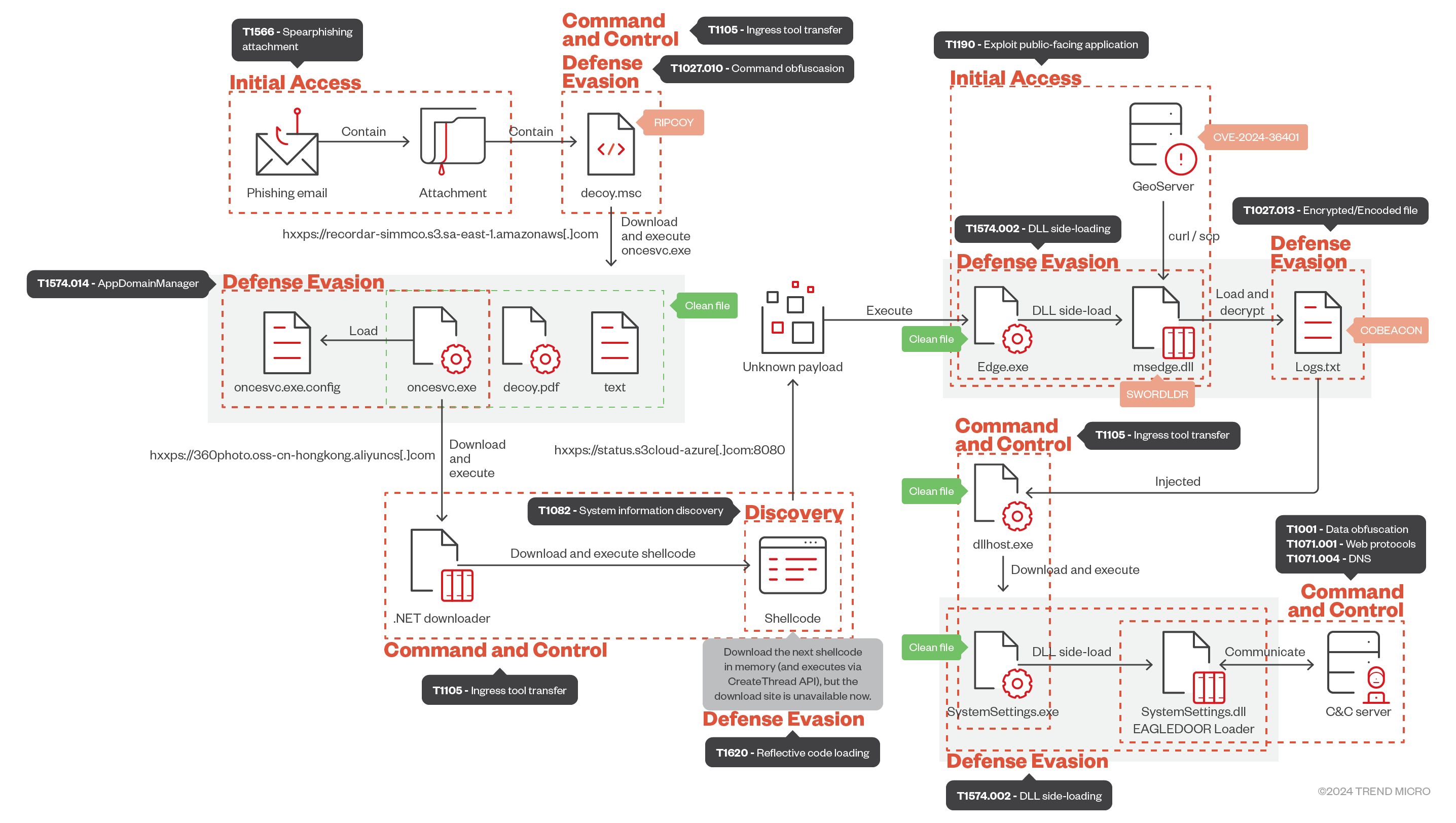
In a recent report from Trend Micro, the cyber espionage group Earth Baxia has been identified targeting government organizations in Taiwan and potentially other countries in the Asia-Pacific (APAC) region through a sophisticated spear-phishing campaign and exploitation of a critical GeoServer vulnerability, CVE-2024-36401. This campaign is part of an ongoing effort to infiltrate key sectors, including telecommunications, energy, and government agencies.
Earth Baxia’s attack begins with CVE-2024-36401, a remote code execution (RCE) vulnerability within GeoServer, an open-source platform for sharing geospatial data. Exploiting this flaw, Earth Baxia was able to download malicious components directly into victim environments, using tools such as “curl” and “scp” to plant harmful files, including customized Cobalt Strike beacons and other payloads. The deployment of these payloads allowed the attackers to execute arbitrary commands and establish footholds within compromised systems.
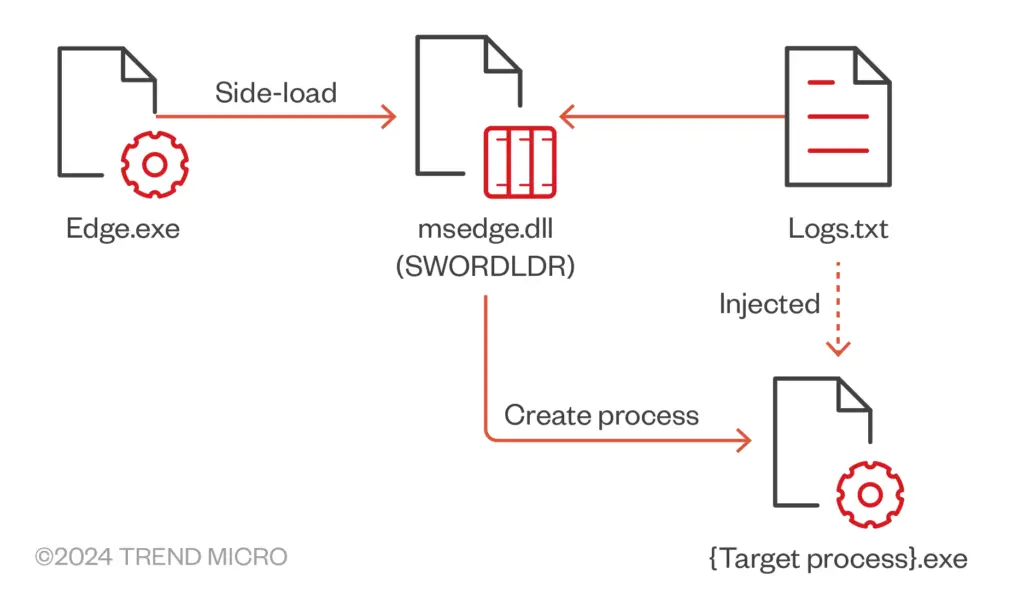
Execution flow of Cobalt Strike components | Image: Trend Micro
In addition to exploiting vulnerabilities, Earth Baxia employed spear-phishing emails to deliver their malicious payloads. These emails were meticulously crafted, often containing decoy documents and malicious attachments designed to appear legitimate. One organization in Taiwan reported receiving over 70 phishing emails within two weeks. The phishing attachments would typically download and execute a malicious .NET application, enabling the attackers to inject further payloads into the system using sophisticated techniques such as AppDomainManager injection.
Once inside the targeted systems, Earth Baxia deployed a customized version of the well-known penetration testing tool Cobalt Strike. By modifying the internal signatures and configuration structure of Cobalt Strike, the attackers were able to evade traditional detection methods. The altered version was loaded via DLL side-loading, making it even more difficult for security systems to recognize the malicious activity.
In addition to Cobalt Strike, Earth Baxia also introduced a new backdoor named EAGLEDOOR. This backdoor supported multiple communication protocols, including DNS, HTTP, TCP, and even Telegram. By utilizing these diverse protocols, EAGLEDOOR enabled Earth Baxia to gather information from compromised machines, exfiltrate data, and deliver further payloads without raising suspicion.
Once inside the compromised systems, Earth Baxia collected sensitive data and exfiltrated it using the “curl” command, sending it to their remote servers. The phishing emails also contained ZIP files that downloaded additional toolsets, such as Edge.exe and msedge.dll, allowing Earth Baxia to maintain long-term access to the systems.
Upon further investigation, Trend Micro researchers found that most of the command-and-control (C2) servers used by Earth Baxia were hosted on Alibaba Cloud and located in Hong Kong, with related samples submitted to VirusTotal from China. Based on these findings, the report suggests that Earth Baxia is likely a China-based advanced persistent threat (APT) group. The targets of this campaign include government agencies and businesses across Taiwan, Vietnam, South Korea, and the Philippines. Additionally, a decoy document written in simplified Chinese indicates that some sectors within China itself may have been impacted.
Related Posts:
- Government Agencies in APAC Targeted by Fake PDF Login Phishing Emails
- Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments
- Critical GeoServer RCE Flaw CVE-2024-36401 Actively Exploited, 6,284 Instances Vulnerable
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions
- CVE-2024-36401 (CVSS 9.8): Urgent Patch Needed for GeoServer RCE Vulnerability





