SpecuCheck v1.1 releases: Windows utility for checking Meltdown and Spectre
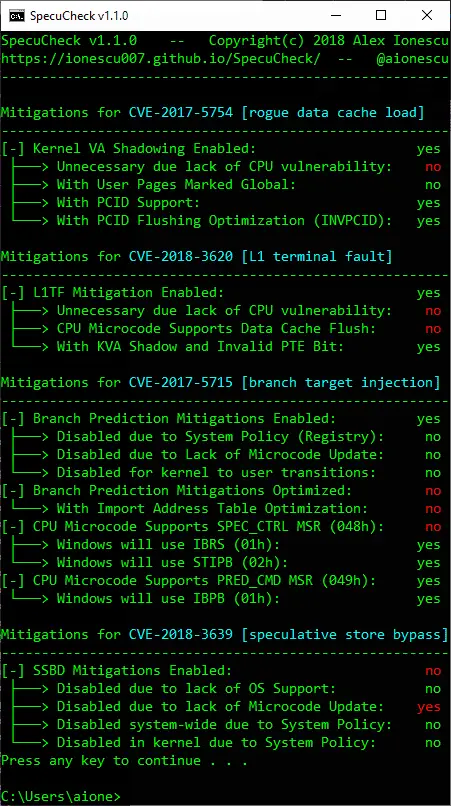
SpecuCheck is a Windows utility for checking the state of the software and hardware mitigations against CVE-2017-5754 (Meltdown), CVE-2017-5715 (Spectre v2), CVE-2018-3260 (Foreshadow), and CVE-2018-3639 (Spectre v4). It uses two new information classes that were added to the NtQuerySystemInformation API call as part of the recent patches introduced in January 2018 and reports the data as seen by the Windows Kernel.
An official Microsoft Powershell Cmdlet Module now exists as well, which is the recommended and supported a way to get this information.

Introduction
On January 3rd 2018, Intel, AMD and ARM Holdings, as well as a number of OS Vendors reported a series of vulnerabilities that were discovered by Google Project Zero:
- Variant 1: bounds check bypass (CVE-2017-5753)
- Variant 2: branch target injection (CVE-2017-5715)
- Variant 3: rogue data cache load (CVE-2017-5754)
Microsoft released patches for Windows 7 SP1 and higher later that same day. These patches, depending on architecture, OS version, boot settings and a number of hardware-related properties, apply a number of software and hardware mitigations against these issues. The enablement state of these mitigations, their availability, and configuration is stored by the Windows kernel in a number of global variables, and exposed to user-mode callers through an undocumented system call.
Additionally, new side channel attacks were reported, such as Spectre Variant 4: speculative store bypass (CVE-2018-3639) and Foreshadow: L1 terminal fault (CVE-2018-3620) which were fixed in Windows 7 SP1 and higher with patches in August’s Patch Tuesday.
SpecuCheck takes advantage of this system call in order to confirm if a system has indeed been patched (non-patched systems will fail the call) and what the status of the mitigations are, which can be used to determine potential performance pitfalls.
Installation on Windows
SpecuCheck is currently x64 only and has only been tested on Windows 10. Future released versions will support Windows 7 and x86 systems as well. To run SpecuCheck, simply execute it on the command-line:
c:\SpecuCheck.exe
Which will result in an informational screen indicating which features/mitigations are enabled?
Changelog v1.1
- * Add detection of L1TF software and hardware mitigation support
- * Add detection of SSBD software and hardware mitigation support
- * Add detection of meltdown-hardened Intel processors and existing AMD processors
- * Clarify that PCID support is now a separate optimization from INVPCID usage
Copyright 2018 Alex Ionescu. All rights reserved.
Source: https://github.com/ionescu007/





