spiderfoot v4.0 releases: the open source footprinting & intelligence-gathering tool
SpiderFoot is an open-source intelligence automation tool. Its goal is to automate the process of gathering intelligence about a given target, which may be an IP address, domain name, hostname, or network subnet.
SpiderFoot can be used offensively, i.e. as part of a black-box penetration test to gather information about the target or defensively to identify what information your organization is freely providing for attackers to use against you.
Read more at the project website.
Features
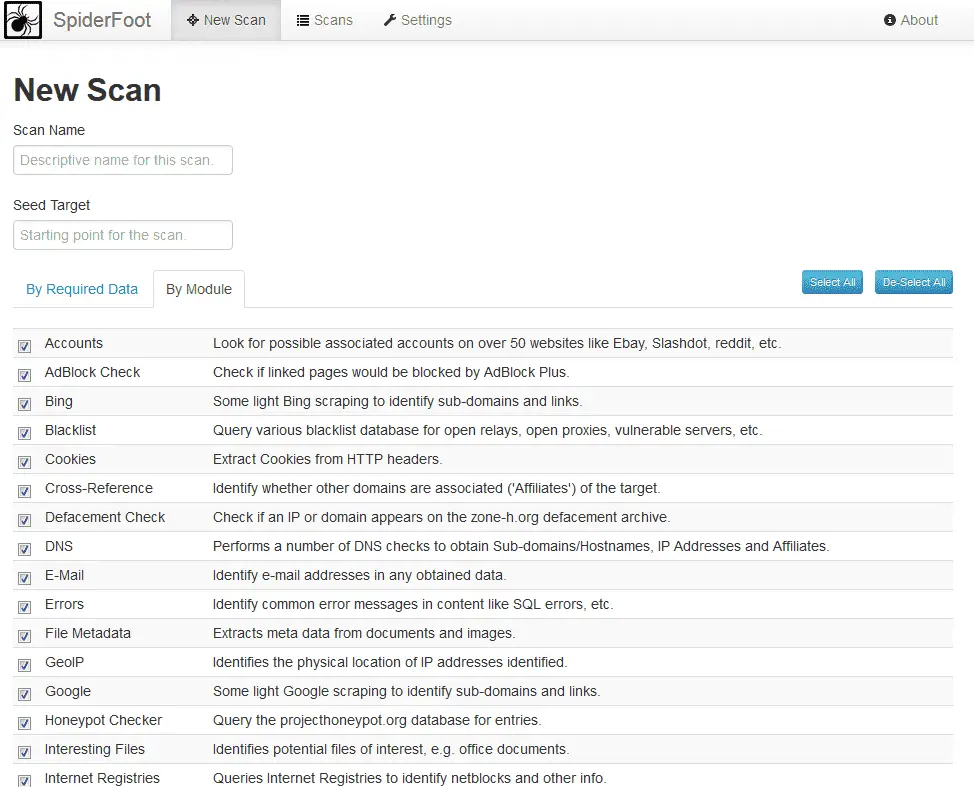
- Utilises a shedload of data sources; over 50 so far and counting, including SHODAN, RIPE, Whois, PasteBin, Google, SANS, and more.
- Designed for maximum data extraction; every piece of data is passed on to modules that may be interested so that they can extract valuable information. No piece of discovered data is saved from the analysis.
- Runs on Linux and Windows. And fully open-source so you can fork it on GitHub and do whatever you want with it.
- Visualisations. Built-in JavaScript-based visualizations or export to GEXF/CSV for use in other tools, like Gephi for instance.
- Web-based UI and CLI. Choose between a GUI that is easy to use and a powerful command-line interface. Take a look through the gallery for screenshots of the GUI and the collection of CLI videos on asiinema.org.
- Highly configurable. Almost every module is configurable so you can define the level of intrusiveness and functionality.
- Modular. Each major piece of functionality is a module, written in Python. Feel free to write your own and submit them to be incorporated!
- SQLite backend. All scan results are stored in a local SQLite database, so you can play with your data to your heart’s content.
- Simultaneous scans. Each footprint scan runs as its own thread, so you can perform footprinting of many different targets simultaneously.
- So much more.. check out the documentation for more information.
Changelog v4.0
SpiderFoot 4.0 introduces the concept of writing your own correlation rules in YAML, plus integration with a number of open source security tools. SpiderFoot has integrated with a few popular open source tools such as DNSTwist, CMSeek, Whatweb, WAFW00F and Nmap for some time
- nbtscan: Scans for open NETBIOS nameservers on your target’s network.
- Nuclei: Fast and customizable vulnerability scanner with a powerful templating framework for custom detections.
- onesixtyone: Fast scanner to find publicly exposed SNMP services.
- Retire.js: Scanner detecting the use of JavaScript libraries with known vulnerabilities.
- snallygaster: Finds file leaks and other security problems on HTTP servers.
- testssl.sh: Identify various TLS/SSL weaknesses, including Heartbleed, CRIME and ROBOT.
- TruffleHog: Searches through git repositories for high entropy strings and secrets, digging deep into commit history.
- Wappalyzer: Wappalyzer indentifies technologies on websites.
Download & Tutorial
Demo
Copyright (C) smicallef