SPIKEDWINE’s Espionage Campaign with WINELOADER Backdoor Revealed
The recent discovery of the Spiked Wine threat actor by Zscaler’s ThreatLabz highlights the ever-evolving landscape of advanced persistent threats (APTs) and the lengths to which state-sponsored actors will go to achieve espionage goals. This campaign demonstrates meticulous operational security practices and a novel modular backdoor designed to evade detection.
The Masquerade of Legitimacy
The unraveling of SPIKEDWINE began with the detection of a seemingly benign PDF file uploaded to VirusTotal from Latvia in late January 2024. Disguised as an invitation from the Indian Ambassador for a wine-tasting event, the document harbored a link to a deceptive questionnaire leading to a malicious ZIP archive. This invitation was not just a call to a cultural gathering but a sophisticated lure into a cyber trap designed to compromise the security of European diplomats engaged with India.
The meticulous crafting of the PDF, complete with details mimicking an official invitation, reveals the threat actor’s intent to exploit the trust and curiosity of its targets. The discovery of a similar PDF uploaded months earlier indicates that this campaign was not an isolated incident but part of a broader, low-volume targeted attack strategy.
WINELOADER: The Malware with a Taste for Secrecy

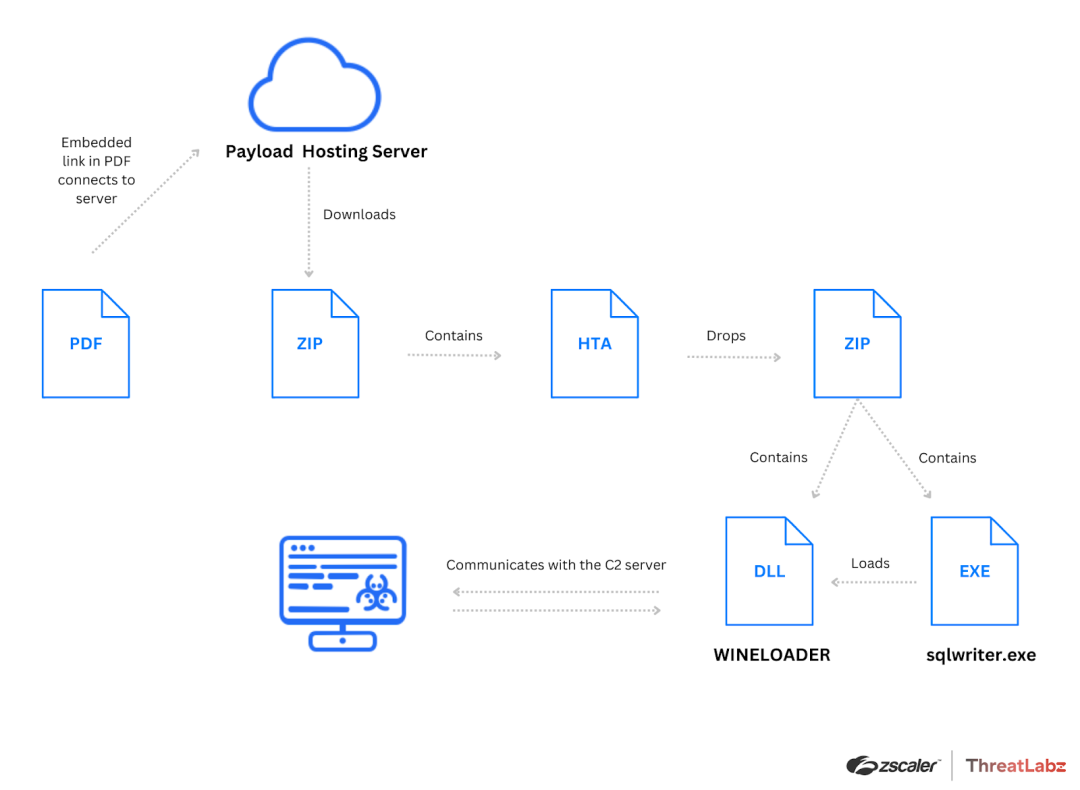
Multi-stage attack chain of WINELOADER backdoor
Central to the SPIKEDWINE campaign is WINELOADER, a modular backdoor engineered with evasion and stealth in mind. Through an intricate infection chain initiated by the malicious HTA file, WINELOADER secures its foothold within compromised systems. The utilization of a legitimate Microsoft binary for DLL side-loading illustrates the attacker’s sophisticated approach to maintaining stealth and bypassing traditional detection mechanisms.
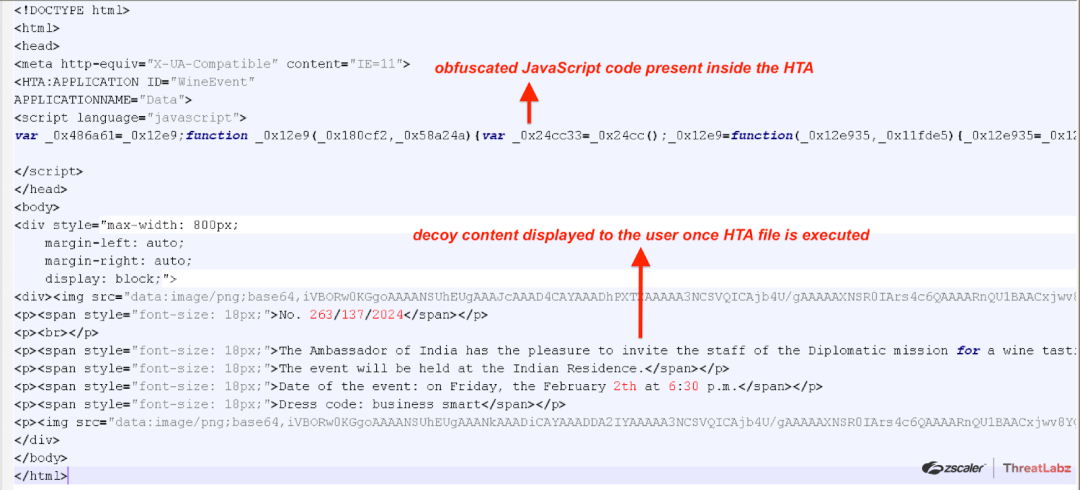
Obfuscated JavaScript code inside the HTA file
WINELOADER’s design allows for encrypted modules to be dynamically fetched from the command and control (C2) server, adapting its functionality on the fly and complicating efforts to analyze and counteract its presence. This modularity, coupled with techniques to obscure sensitive data in memory, underscores the advanced capabilities of SPIKEDWINE’s operators.
Hijacking the Web: A Network of Deception
SPIKEDWINE distinguishes itself through its use of advanced evasion techniques. By employing methods such as re-encryption of sensitive data and zeroing out memory buffers, the threat actor demonstrates a deep understanding of how to navigate the environment undetected. The choice of compromised websites for hosting payloads and C2 communication further complicates tracking the actor’s movements, showcasing a layered approach to concealment.
Espionage Motives: The Geopolitical Angle
Spiked Wine’s focus on diplomatic targets, particularly those linked to India and European nations, suggests a nation-state threat actor with a vested interest in geopolitical affairs. Their meticulous approach indicates they seek sensitive information that can be leveraged for strategic or political gain.
The Rise of Sophisticated Espionage
The Spiked Wine case underscores a worrying trend of increasingly advanced cyber espionage. Nation-state actors are investing heavily in offensive cyber capabilities, developing tools and techniques that can easily bypass traditional defenses. This raises the stakes for organizations and individuals, particularly those handling sensitive data.





