SpyAgent Malware Targets Crypto Wallets via Image Scanning
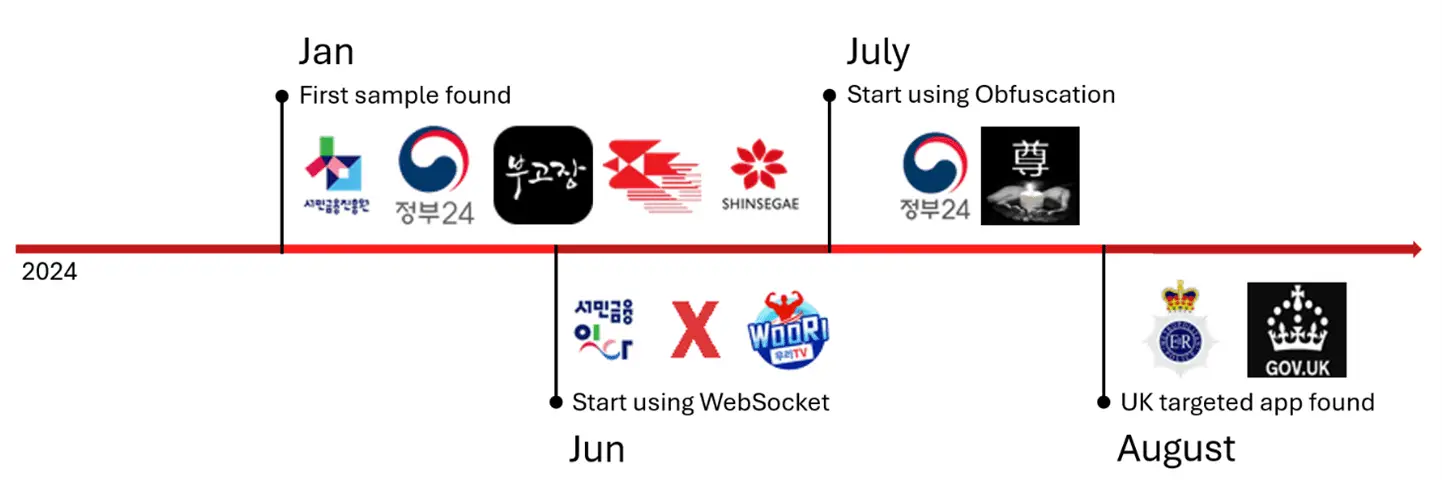
McAfee’s Mobile Research Team has issued a warning about a new, sophisticated Android malware campaign dubbed SpyAgent. This insidious malware targets users’ cryptocurrency wallets by scanning images on their devices for mnemonic keys, the 12-word phrases often used to recover access to these wallets.
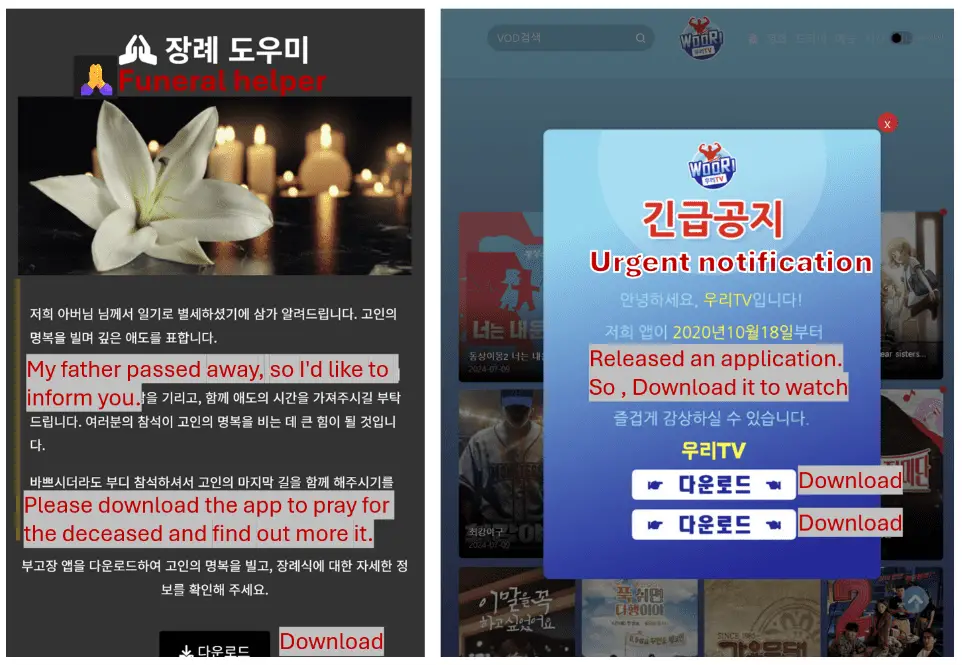
SpyAgent employs a range of deceptive tactics to lure victims. It disguises itself as various trustworthy apps, such as banking, government services, TV streaming, and utility apps, tricking users into downloading and installing them. Once installed, these malicious apps secretly collect and transmit sensitive data, including text messages, contacts, and stored images, to remote servers. To mask its activities, the malware often employs distracting tactics like endless loading screens and unexpected redirects.
Fake Websites | Image: McAfee
Primarily distributed through phishing campaigns in Korea, the malware has recently been observed expanding its reach to the UK. Victims are often tricked into clicking on malicious links sent via text messages or social media, leading them to download and install the malware disguised as legitimate apps.
SpyAgent has an array of capabilities, including stealing contacts, SMS messages, photos, and device information. It can also receive commands from remote servers, allowing it to modify device settings and send SMS messages, potentially spreading phishing attacks further.
The malware’s developers have continuously refined its tactics to evade detection. It has transitioned from simple HTTP requests to WebSocket connections for its command and control (C2) communications, making it more difficult to track. It also employs advanced obfuscation techniques to conceal its malicious code.
Analysis of the C2 server infrastructure reveals that SpyAgent’s primary objective is to obtain mnemonic recovery phrases for cryptocurrency wallets, highlighting the financial motivations behind this campaign.
While currently focused on Android, the discovery of an “iPhone” label in the admin panel suggests that the attackers might be developing an iOS variant of the malware. This underscores the importance of remaining vigilant across all mobile platforms.
McAfee urges users to be wary of installing apps from unknown sources, granting excessive permissions, and clicking on suspicious links. It is also strongly recommended to use robust security software and keep sensitive information securely stored.





