Sri Lanka: New Target for T-APT-04 APT Group
In a recent report by cybersecurity expert Nimantha Deshappriya, details have emerged about a sustained cyber-espionage campaign orchestrated by the advanced persistent threat (APT) group known as SideWinder, also referred to as T-APT-04. Traditionally, Sri Lanka, with its “small, friendly nation” profile and limited global influence, has been a relatively low-priority target for APTs and financially motivated cybercrime. However, recent political shifts have made it a notable point of interest for regional threat actors, marking a significant change in its threat landscape.
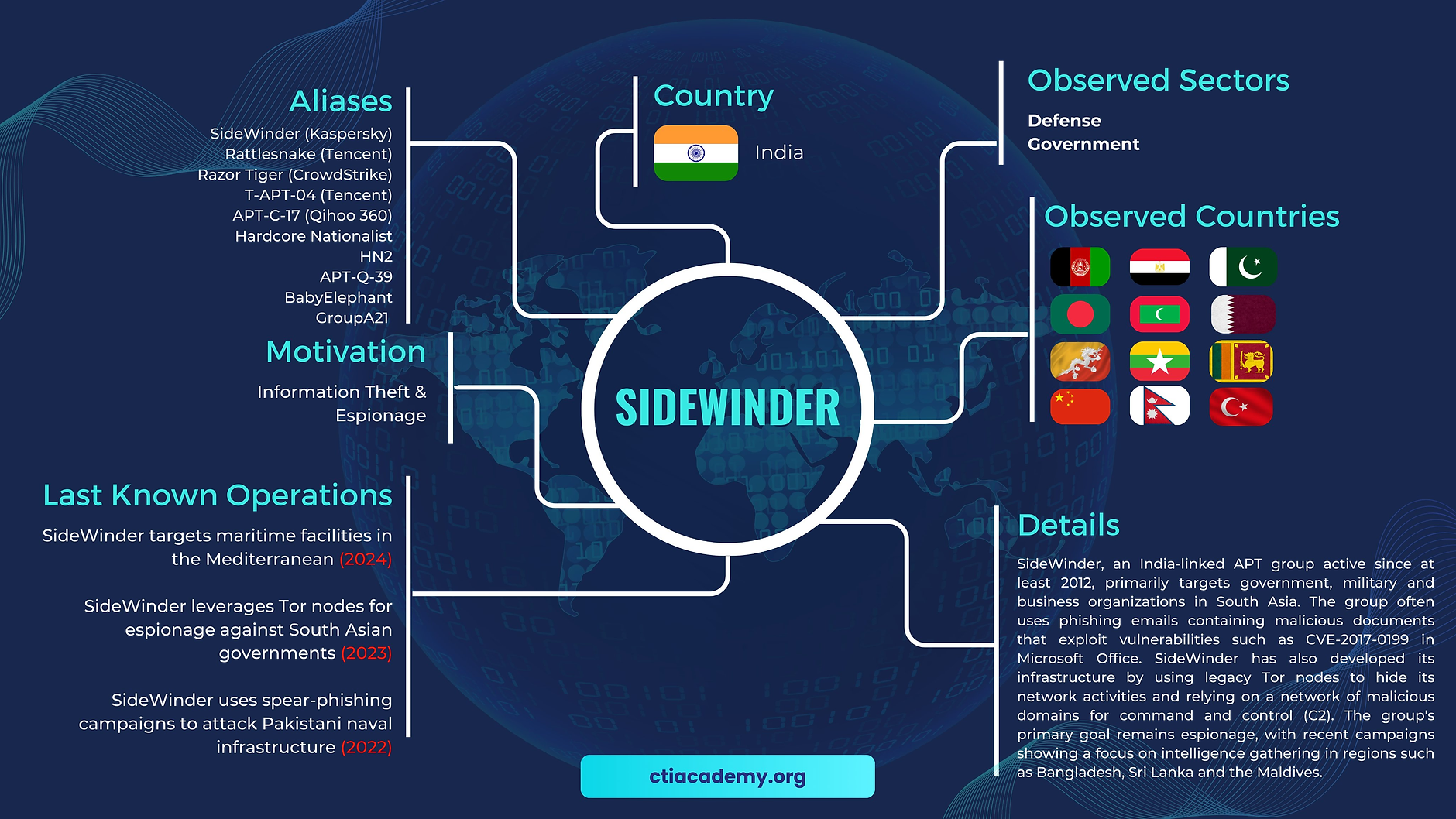
SideWinder, or “Rattlesnake,” is a nation-state APT group originating from India, with a history of targeting regional adversaries such as Pakistan, Nepal, and China. Deshappriya’s report highlights that “the primary objective appears to be espionage, aimed at stealing intelligence or other sensitive information from government organizations,” suggesting that SideWinder’s recent operations in Sri Lanka stem from its growing geopolitical relevance.
The origins of this interest can be traced back to the strong economic ties between Sri Lanka and China. Projects like the $2.19 billion Hambantota Port, funded by Chinese investment, have raised regional concerns, especially in India, regarding possible military implications. According to Deshappriya, these developments have “sparked fears that China could establish a strong foothold in Hambantota,” a move that has likely spurred SideWinder’s cyber espionage activities targeting Sri Lankan institutions.
T-APT-04 has displayed a mix of low-skill tactics and sophisticated evasion techniques, initially perceived as a low-skill actor due to its use of publicly available exploits, such as malicious LNK files and Remote Access Trojans (RATs). However, Deshappriya underscores that “a deeper analysis of its operations reveals that its true capabilities are much more advanced,” with a distinct emphasis on maintaining persistence and evading detection.
The campaign often begins with spear-phishing emails containing malicious attachments. Deshappriya’s report details several of these tactics:
- LNK files that retrieve an RTF file delivering a JavaScript file.
- ZIP archives containing LNK files that download HTA files with embedded JavaScript.
- DOCX files linked to OLE objects that deliver JavaScript files for further compromise.
The targeted use of these phishing techniques leverages “the outdated Microsoft software commonly used by Sri Lankan government agencies,” increasing the effectiveness of SideWinder’s attacks.
SideWinder’s C2 (Command and Control) infrastructure also demonstrates high adaptability. For example, Dynamic DNS domains such as “navy-lk.direct888.net” mimic legitimate Sri Lankan government domains to facilitate unauthorized access. SideWinder uses IP filtering and user-agent strings to control access to payloads, ensuring that only targeted entities download the malicious content. As Deshappriya notes, “If a non-targeted user attempts to access the payload, they are instead served a decoy 8-byte RTF file,” exemplifying server-based polymorphism.
The report warns of the need for Sri Lanka to strengthen its cybersecurity posture. SideWinder’s attacks illustrate the vulnerabilities associated with outdated software, limited security awareness, and the increasing geopolitical complexities Sri Lanka faces.
Related Posts:
- SideWinder APT Group Sets Sights on Ports and Maritime Facilities in Espionage Campaign
- SideWinder APT: A Decade of Evolution and Global Expansion
- Cyber-Espionage Campaign Unveiled: Operation Cobalt Whisper Hits Sensitive Industries
- Advanced Cyberattacks: Patchwork APT’s Nexe Backdoor Campaign Exposed
- KLogEXE & FPSpy Backdoor: Kimsuky’s Evolving Cyber Espionage Arsenal