Stealthy Malware Campaign Switches Tactics, Targets WordPress Sites
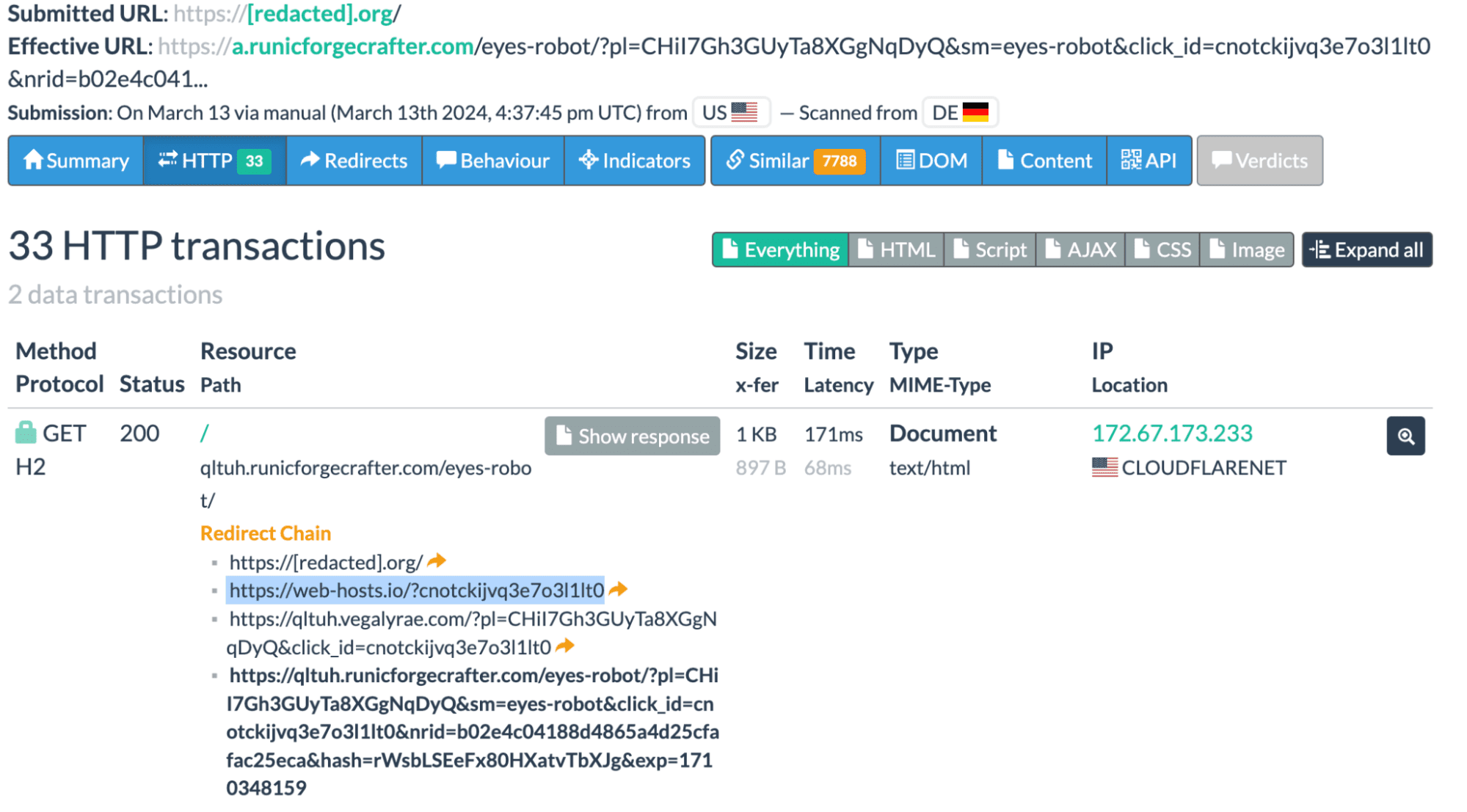
A detailed analysis by Sucuri, a leading website security firm, has uncovered a sophisticated malware campaign that has shifted strategies to become more elusive and harder to detect. The hackers behind this campaign are targeting WordPress sites, employing a combination of deceptive server-side redirects and DNS manipulation to infect websites and redirect visitors to malicious destinations.
Shifting Tactics: From Client-Side to Server-Side

Image: Sucuri
Initially, the malware used client-side JavaScript to redirect users. However, since March 2024, the campaign has switched to a stealthier approach using server-side redirects within the WordPress environment. This makes detection significantly more challenging for web scanners. Over 46,000 websites have been detected as infected, with February 2024 experiencing the highest activity.
The DNS Twist
A key component of this campaign is the misuse of DNS TXT records. The attackers are using a technique called a “Traffic Direction System” (TDS) where they hide redirect instructions within seemingly harmless DNS records. These infected sites unknowingly become part of the redirection network.
The domain names involved in this TDS include:
- cloud-stats[.]com
- host-stats[.]io
- logsmetrics[.]com
- ads-promo[.]com
- tracker-cloud[.]com
These domains serve as the backbone of the malware‘s redirect mechanism, with the DNS responses directing victims to further malicious sites.
Shift to Server-Side Redirects
The shift to server-side redirects involved the use of PHP snippets instead of the previous JavaScript injections. These snippets were added to the WordPress sites using the WPCode plugin, which is popularly used to inject custom code into websites. By moving to PHP, the attackers managed to evade detection from external scanners, which typically scan for JavaScript-based anomalies.
Malicious PHP Snippets and Indicators of Compromise
Sucuri researchers have identified that these PHP snippets can often be found disguised as “Untitled Snippet” in the WordPress admin interface. Commonly, these snippets utilize extensive use of the base64_decode function to decode strings, a common tactic to obscure the true nature of the code.
Some of the code snippets found involve:
-
add_action(base64_decode(‘aW5pdA==’),base64_decode(‘X3JlZA==’)); which decodes to add_action(‘init’,’_red’);
- Checks for the first site visit in the last 24 hours before executing the redirect.
These snippets are primarily used to check visitor details and redirect them without alerting the website administrators or the actual users.
Mitigation and Protection Strategies
Given the sophistication and stealthiness of this malware campaign, Sucuri has outlined several mitigation steps for website owners and web hosts:
- Regularly update and patch all components of the website, including plugins and themes.
- Review and monitor all installed plugins, especially checking for unrecognized or hidden installations.
- Change admin passwords and ensure no unauthorized WordPress users are present.
- Utilize web application firewalls to add a layer of security and potentially block known malicious IPs and domains.
- Sinkhole known malicious domain names used in the DNS TDS to prevent further spread of the malware.





