Stealthy New Android Trojan Disguised as Popular Apps Steals Your Data

A sophisticated new Android malware threat is making the rounds, and its methods are alarmingly effective. The SonicWall Capture Labs threat research team has identified a sophisticated new Remote Access Trojan (RAT) targeting Android devices. This malware cunningly disguises itself using icons of widely recognized Android apps, misleading users into installing it. Once installed, it performs a series of unauthorized activities, primarily focused on stealing user credentials.
Disguise and Deception: The Trojan’s Entry
The app icon used by the malware
The Remote Access Trojan takes advantage of familiar Android app icons, a method known as “icon spoofing,” to trick users into believing they are downloading legitimate software. This tactic significantly lowers the guard of potential victims, making the malware more effective in its deceitful objectives.
Once installed, the true danger begins. It immediately asks for two critical permissions that most users don’t fully understand:
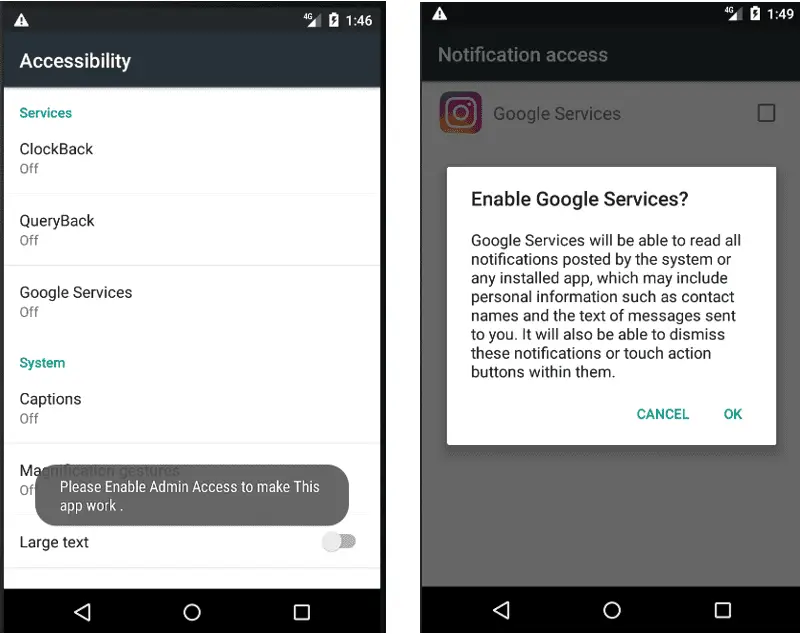
Prompt for accessibility permission
- Accessibility Service: This is the master key. It lets the malware interact with apps and your screen, giving it immense power to perform actions without your consent.
- Device Admin Permissions: Think of this as insurance for the malware. It becomes very difficult to uninstall, ensuring it can do its dirty work for a long time.
Under Remote Control
The RAT establishes a connection with a Command-and-Control (C&C) server, from which it receives specific instructions. These commands include but are not limited to:
- Reading text messages and call logs
- Accessing the device contact list
- Collecting names of installed apps
- Changing the device wallpaper
- Sending text messages
- Manipulating web browser sessions to facilitate phishing attacks
This level of control allows the attacker to carry out a variety of malicious activities without the user’s knowledge.
The Ultimate Goal: Credential Theft

Instances of fraudulent HTML
One of the most alarming capabilities of this malware is its focus on credential harvesting. The malware directs the victim to enter login credentials into fake login pages that mimic legitimate applications. These pages, stored locally within the malware’s asset folder, capture the entered user IDs and passwords using JavaScript, which then transmits this sensitive information to the attackers.
Other Malicious Activities
The RAT can also:
- Retrieve all phone numbers stored on the device
- Toggle the device’s camera flashlight on and off
- Send SMS messages based on commands from the C&C server
Protect Yourself: Fight Back
- The Official Line: Stick to the Google Play Store as your primary app source. It’s not perfect, but it has more safeguards than third-party sites.
- Scrutinize Permissions: Be highly critical of apps asking for extensive control. Do they need those permissions to work?
- Update Often: Android updates and app updates often patch security holes – keep your software current.
- A Mobile Shield: A good mobile antivirus can act as a safety net, detecting threats like this RAT.
- Educate Yourself: Stay aware of the latest mobile threats. Read cybersecurity news and blogs to keep your knowledge sharp.





