Storm-0501 Targets Hybrid Clouds with Evolving Ransomware Tactics
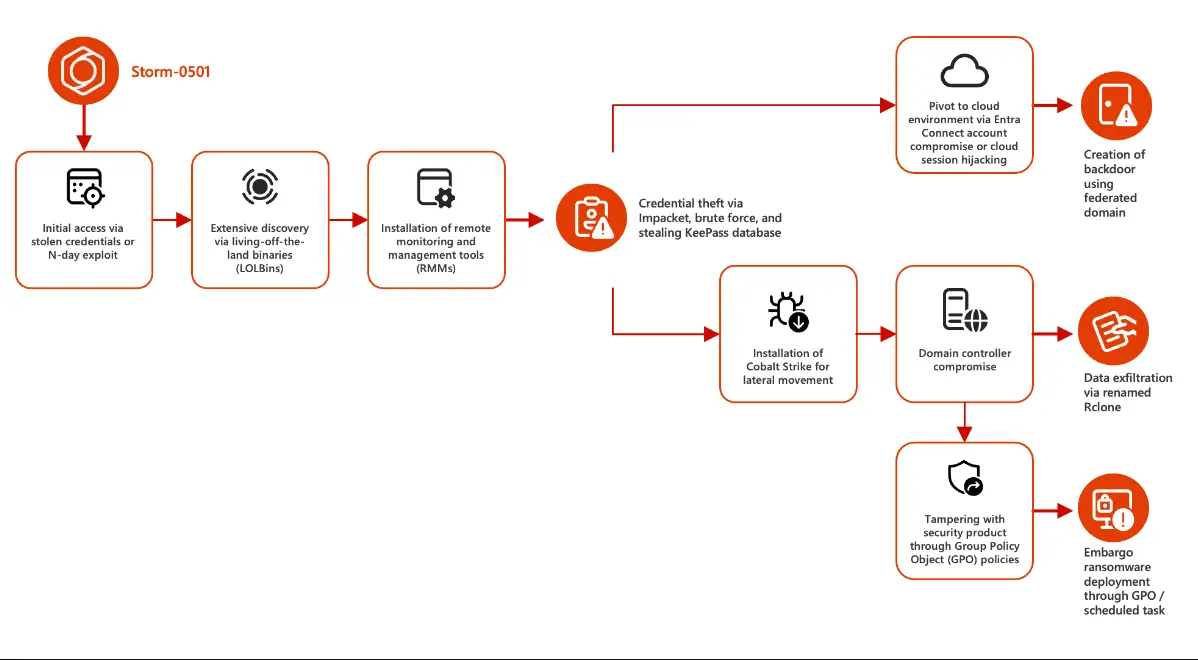
In a recent report from Microsoft Threat Intelligence, the cybercriminal group Storm-0501 has been identified as a rising threat, targeting hybrid cloud environments through a series of sophisticated ransomware attacks. Known for its opportunistic and financially driven operations, Storm-0501 has ramped up its efforts since 2021, initially making waves with the deployment of Sabbath ransomware against U.S. school districts. The group has since evolved, employing a variety of ransomware strains including Hive, BlackCat (ALPHV), and most recently, Embargo ransomware.
Storm-0501’s latest campaign showcases a shift in attack strategy, specifically targeting organizations that operate both on-premises and cloud environments. By exploiting vulnerabilities in on-premises servers, such as Zoho ManageEngine (CVE-2022-47966), Citrix NetScaler (CVE-2023-4966), and ColdFusion 2016 application (possibly CVE-2023-29300 or CVE-2023-38203), the group has been able to perform lateral movements from on-premises infrastructure to cloud environments, facilitating data exfiltration, credential theft, and ultimately, ransomware deployment.
The group has targeted a broad range of sectors, including government, manufacturing, transportation, and law enforcement, primarily within the United States. Storm-0501’s attacks are particularly concerning due to their ability to exploit weak credentials and over-privileged accounts, allowing them to seamlessly transition between on-premises and cloud networks. Once inside, they establish persistent backdoors, enabling further exploitation and ransomware deployment.
The ransomware attacks orchestrated by Storm-0501 employ a combination of commodity and open-source tools, showcasing a high level of adaptability. Common tools used by the group include Impacket for credential extraction, Cobalt Strike for lateral movement, and Rclone for data exfiltration. Their methods are often combined with obfuscated scripts and remote monitoring tools to ensure persistence within compromised systems.
In a concerning development, Storm-0501 has been observed exploiting Microsoft’s Entra ID (formerly Azure AD) through cloud session hijacking and the compromise of synchronization accounts. This allows the group to gain administrative control over both on-premises and cloud systems, enabling them to set or reset passwords and escalate their privileges.
Operating as a Ransomware-as-a-Service (RaaS) affiliate, Storm-0501 has made ransomware attacks more accessible to a broader range of threat actors. By collaborating with other cybercriminal organizations, they have been able to launch large-scale attacks using ransomware strains maintained by other groups. This has allowed them to increase the frequency and scope of their operations, often employing double extortion tactics—encrypting victim data and threatening to publicly leak it unless a ransom is paid.
Storm-0501’s most recent use of the Embargo ransomware, a new strain written in Rust, exemplifies the group’s ability to adopt cutting-edge tools. Embargo’s advanced encryption methods and RaaS model have made it a powerful tool in the hands of Storm-0501 affiliates, further solidifying their place as a significant player in the ransomware ecosystem.
The ramifications of these attacks have been severe, with numerous organizations facing operational disruptions, data breaches, and financial losses. Storm-0501 has specifically targeted high-value assets, including domain administrators and critical infrastructure, amplifying the potential damage of each attack.
In response to the growing threat, Microsoft has issued a series of mitigation strategies designed to help organizations defend against Storm-0501’s tactics. These include implementing multi-factor authentication (MFA), ensuring credential hygiene, and enabling Conditional Access policies to limit unauthorized access. Additionally, Microsoft emphasizes the importance of securing hybrid cloud environments, as these attacks highlight the vulnerabilities inherent in organizations that rely on both on-premises and cloud-based infrastructure.





