Sysrv Botnet Returns: Google Subdomain Used to Spread Cryptomining Malware
Security experts at Imperva Threat Research have exposed a new evolution of the notorious Sysrv botnet. This latest variant exhibits sophisticated tactics, including the abuse of a Google subdomain to spread its payload – a potent XMRig cryptocurrency miner.
From Compromised Sites to Your System
The campaign initially targets vulnerable web servers running Apache Struts (CVE-2017-9805) or Atlassian Confluence (CVE-2023-22527 and CVE-2021-26084), aiming to exploit known security flaws. Of particular interest is the attackers’ use of a legitimate domain belonging to a Malaysian academic institution, compromised to host the malicious files.
The Evolving Attack Chain

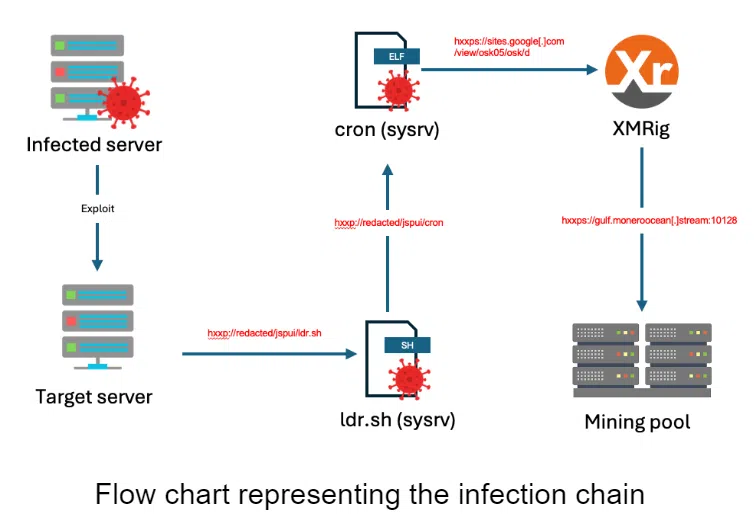
Image: Imperva Threat Research
The botnet’s infection process begins with a dropper script, ldr.sh, strikingly similar to its predecessors but with critical updates. The script, which prepares the ground for the second-stage binary, showcases enhanced capabilities to terminate competing malware and disable endpoint protection, illustrating the attackers’ intent to secure their foothold within infected systems.
Following this preparatory phase, the script embarks on a propagation spree, leveraging SSH to spread across other hosts. This method reflects the botnet’s persistent endeavor to expand its reach and maximize its impact.
The core of the Sysrv botnet‘s latest iteration lies in its upgraded binary. This Golang-based binary, despite being obfuscated and packed with UPX to thwart analysis, was dynamically analyzed by Imperva researchers. The analysis revealed an unprecedented use of a Google subdomain for downloading the second-stage binary, a maneuver that camouflages the botnet’s malicious activities under the guise of legitimacy.
The payload, once decoded and unpacked, was identified as an XMRig miner, aligning with the botnet’s known objective of cryptomining. By connecting to specific endpoints and operating on behalf of a Monero wallet, the botnet demonstrates its capacity to generate substantial revenue, with estimates suggesting an annual yield of approximately 57 XMR (~ $6,800).
The Bottom Line
The latest variant of the Sysrv botnet is a testament to the sophistication and adaptability of modern cyber threats. By masquerading its malicious activities through the use of legitimate domains and a Google subdomain, the botnet not only evades detection but also raises significant concerns regarding the safety of seemingly trusted internet spaces.