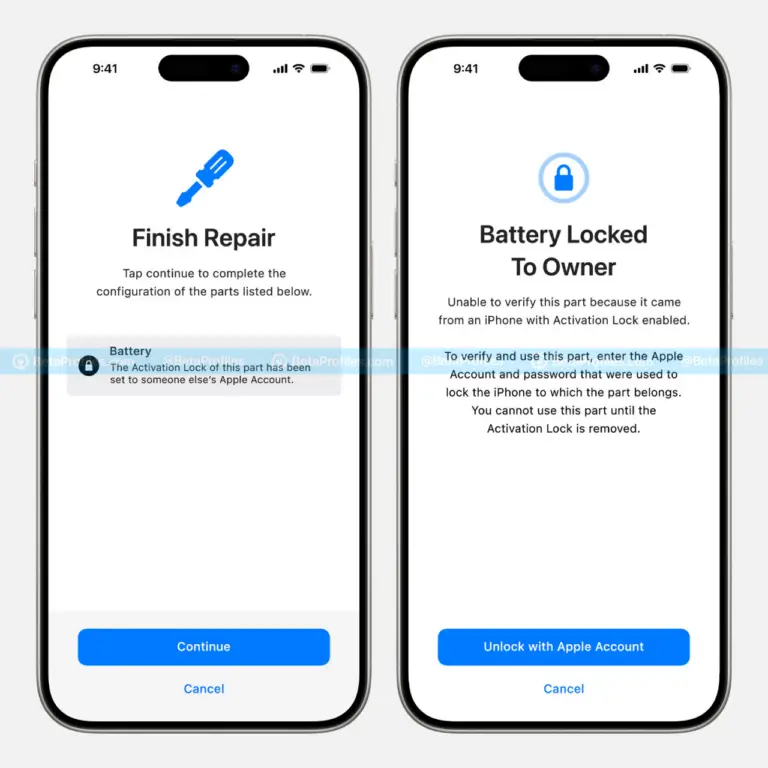
A detailed technical and a proof-of-concept (PoC) exploit code from security researcher Mickey Jin has unveiled a...
Apple
After unveiling its most powerful AI model to date, Gemini 2.0, alongside the “thinking” AI model Gemini...
Jamf Threat Labs has identified a vulnerability in Apple’s Transparency, Consent, and Control (TCC) security framework. Designated...
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning about three actively exploited vulnerabilities...
Security researcher Snoolie K has published an in-depth analysis of a significant security flaw in WorkflowKit, which...
Apple users are urged to update their devices immediately following the discovery of two critical zero-day vulnerabilities...
In a recent analysis, cybersecurity researchers Hichem Maloufi and Christian Mina detailed CVE-2024-44258, a symlink vulnerability affecting...
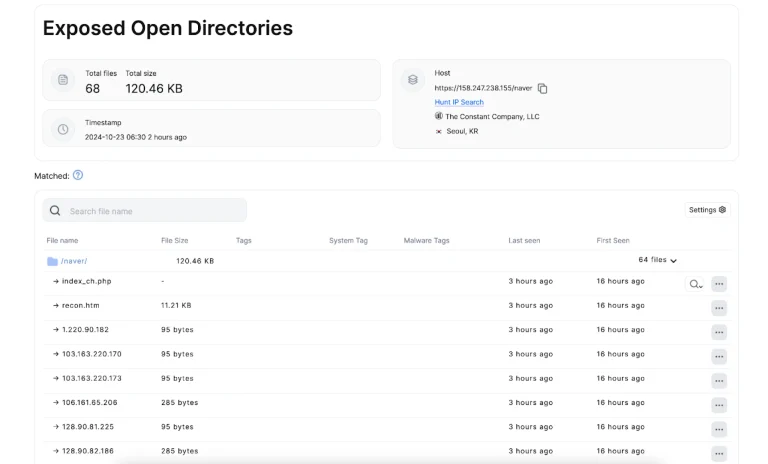
In a recent report, Hunt researchers uncovered a sophisticated phishing campaign suspected to be linked to North...
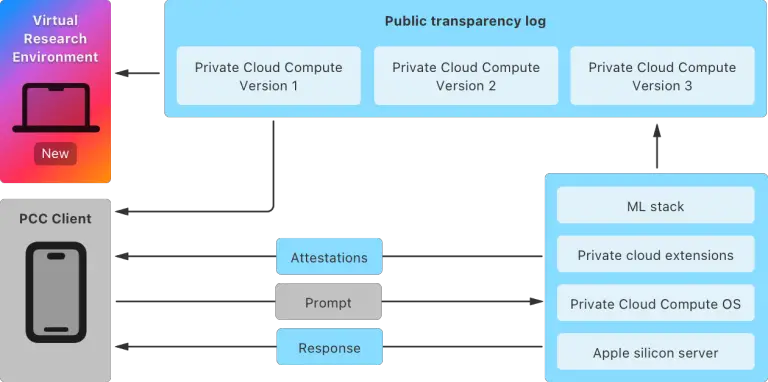
Apple has introduced a Virtual Research Environment (VRE) to provide public access for testing the security of...
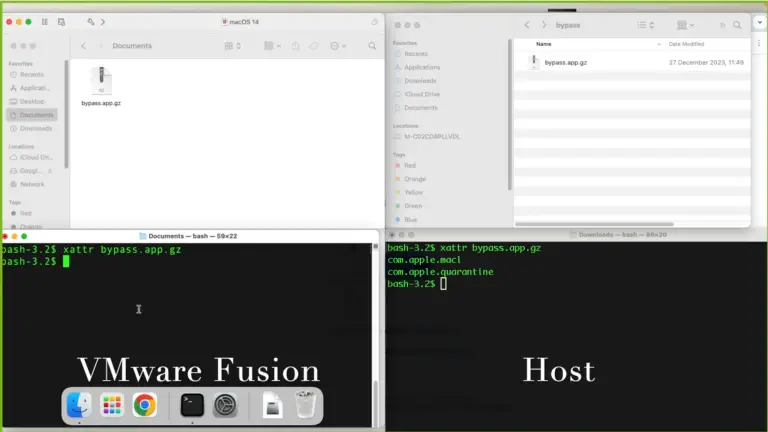
A new report from Unit 42 researchers has uncovered significant weaknesses in macOS’s Gatekeeper security mechanism, which...
In an unexpected turn of events, Apple has pulled the plug on the iPadOS 18 update for...
Once Lost Mode is activated on an Apple device, it is incredibly difficult to disable unless done...
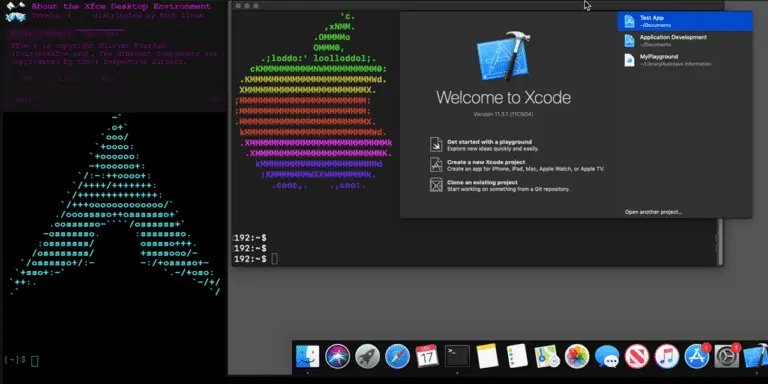
An open-source project on GitHub called Docker-OSX allows users to effortlessly run Apple’s OSX and macOS systems...
The U.S. regulatory body’s antitrust case against Google has recently seen significant developments. A U.S. federal judge...