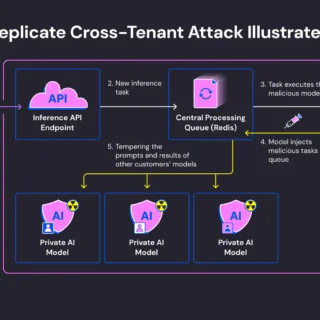
Vulnerability in lighttpd Web Server Exposes Sensitive Data: Urgent Patch Required
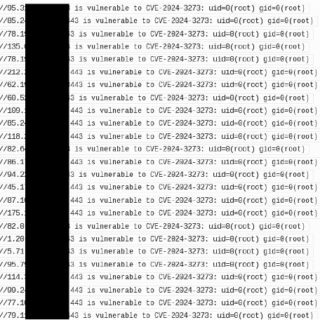
The Carnegie Mellon CERT Coordination Center (CERT/CC) has issued a critical vulnerability note regarding a use-after-free vulnerability in lighttpd versions 1.4.50 and earlier. This vulnerability allows remote, unauthenticated attackers to exploit crafted HTTP requests,...