TargetCompany Ransomware Group Escalates Attacks: New Tools and Persistent Targeting of MS-SQL Servers
The world of cybersecurity is witnessing an alarming trend as ransomware groups intensify their attacks on Microsoft SQL (MS-SQL) servers, exploiting weak management practices to deploy devastating malware. The AhnLab Security Intelligence Center (ASEC) has recently shone a spotlight on these cyber threats, specifically the operations conducted by the notorious TargetCompany ransomware group. This group is actively deploying Mallox ransomware alongside other malicious tools to exploit vulnerable database servers.
The Evolving Attack Chain

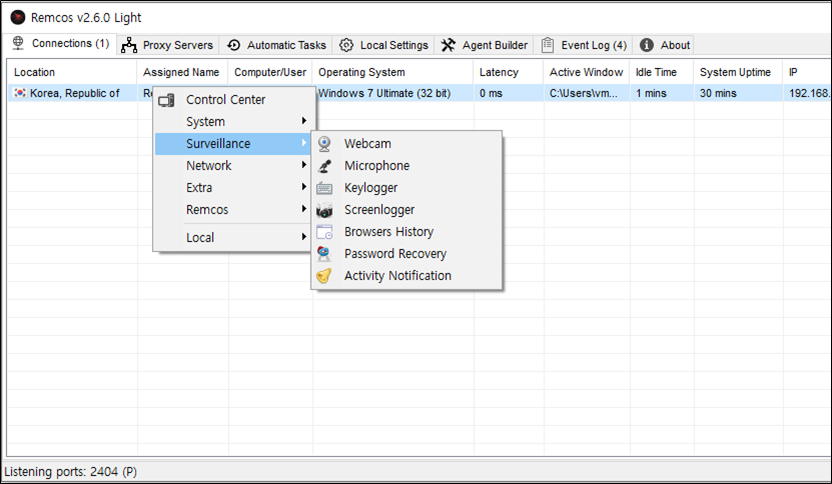
Remcos RAT
The TargetCompany’s method involves a two-pronged attack on MS-SQL servers. Initially, attackers employ brute force or dictionary attacks to compromise the ‘SA’ (System Administrator) account, a common target due to its extensive permissions. Following the breach, they deploy the Remcos Remote Access Trojan (RAT)—a tool marketed for legitimate remote management but often repurposed for malicious intent. Remcos enables attackers to perform a variety of intrusive actions, such as controlling webcams, capturing screenshots, and extracting sensitive data like passwords.
The Mallox Ransomware
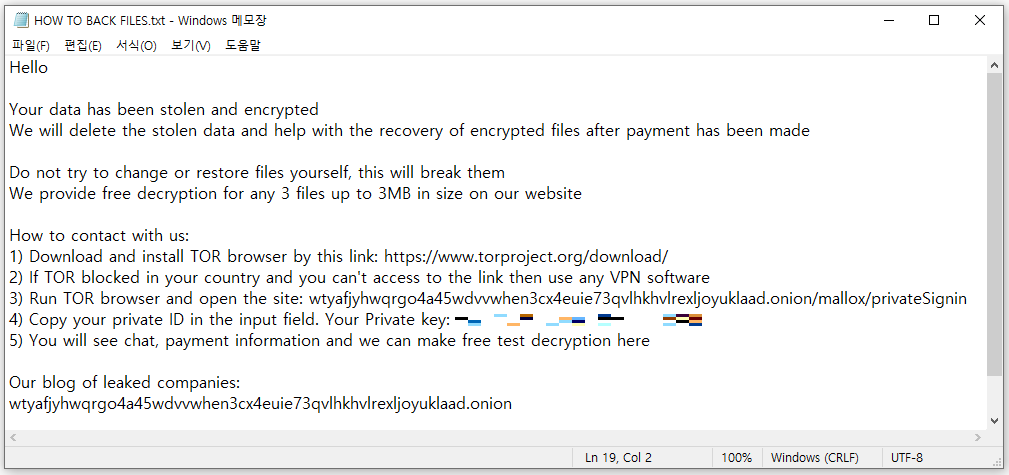
Mallox’s ransom note
About 29 hours after gaining initial access, the attackers escalate their intrusion by installing Mallox ransomware. Mallox is particularly aggressive; it disables Windows recovery options and deletes shadow copies to prevent data restoration, ensuring that the encryption of files causes maximum disruption. The ransomware then displays a ransom note, coercing victims to pay for decryption keys. This method has become a hallmark of the TargetCompany ransomware group’s operations, with similar tactics seen in previous attacks involving BlueSky ransomware and Tor2Mine CoinMiner.
Malware Deployment Techniques
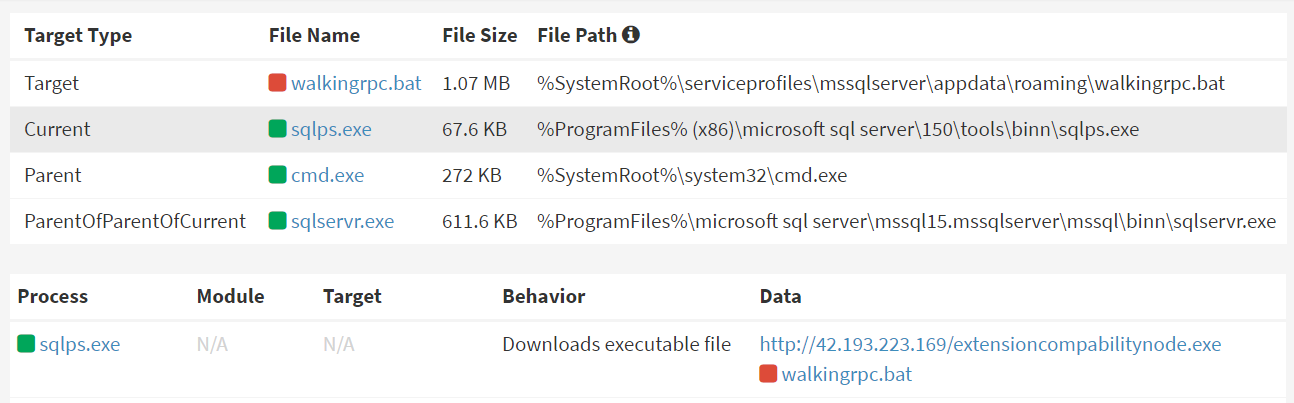
Remcos RAT being installed through SQLPS
Interestingly, the latest findings reveal that instead of using traditional PowerShell scripts, the attackers have now switched to SQLPS, a specialized PowerShell utility for SQL Server, to deploy malware. This shift is likely an attempt to evade detection by conventional security products that monitor PowerShell-based malicious activities. Additionally, the attackers use a custom remote screen control malware, enabling them to manipulate infected systems remotely and perform further malicious activities discreetly.
Historical Patterns and Current Threat Landscape
This pattern of attack is not new. ASEC has traced similar tactics back to previous incidents involving other malware like BlueSky ransomware, suggesting a persistent threat actor or group behind these campaigns. The utilization of MS-SQL vulnerabilities has been consistent, indicating that these database servers remain high-value targets for cybercriminals.
Critical Takeaways for Cybersecurity
This ongoing series of attacks underscores the critical need for stringent security measures around MS-SQL servers. System administrators are advised to:
- Implement robust password policies and change them periodically.
- Ensure that database servers are not directly accessible from the internet unless absolutely necessary.
- Deploy advanced security solutions capable of detecting and mitigating sophisticated threats like RATs and ransomware.
Further Reading
For in-depth technical analysis and additional security recommendations, visit the AhnLab Security Intelligence Center (ASEC) website.





