Although this teen monitoring application is controversial and invasive of privacy, the company stated that it does not require parents to obtain the consent of their children. But this company, based in California, has its servers hosted on Amazon’s cloud, protected from anyone and accessible without a password.
British security researcher Robert Wiggins discovered two leaked servers. After ZDNet alerted the company, two servers went offline, and the other server appeared to contain only test data. “We have taken action to close one of our servers to the public and begun alerting customers that could potentially be impacted”. A TeenSafe spokesman told ZDNet on Sunday.
The data store has TeenSafe’s associated parent’s email address and their child’s Apple ID email address. It also includes the child’s device name – usually just their name – and the device’s unique identifier. The data contains the clear text password of the child’s AppleID. Because the app requires the closure of two-factor authentication, a malicious actor viewing this data can simply use credentials to access the child’s account to access their personal content data.
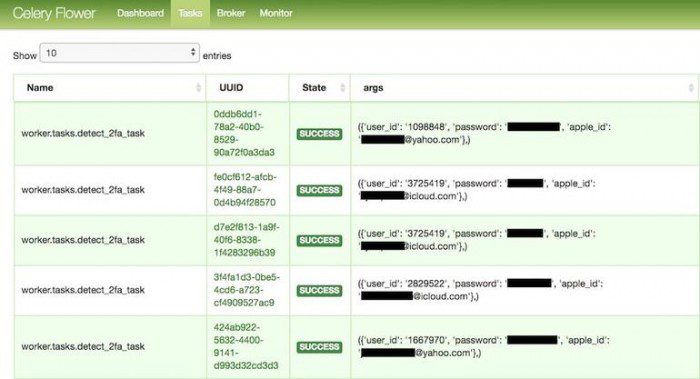
None of these records contain content data, such as photos or information, or the location of parents or children. The data also contains error messages related to failed account operations, for example, if the parent finds the child’s real-time location is not completed.
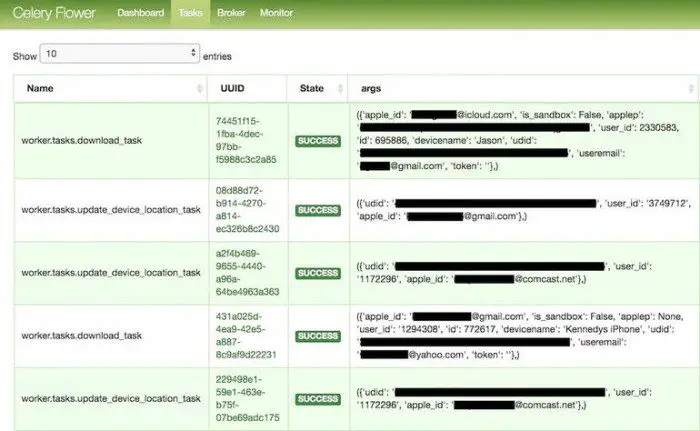
Before the server went offline, at least 10,200 records contained customer data in the past three months – but some records were duplicated. One of the servers seems to store test data, but it is not known if there are other exposed servers that have additional data. TeenSafe claims that more than one million parents use the service.
TeenSafe claims on its website that it is “secure” and uses encryption technology to encrypt data, such as data leakage. TeenSafe said it will continue to assess this situation and provide more information when available.
Source, Image: ZDNet





