The Doppelgänger Playbook: Russian Information Operations Unveiled (June-July 2024)
From early June to late July 2024, Russian actors conducted a series of information operations under the code name “Doppelgänger.” These campaigns were particularly active during the unexpected snap elections in France, prompting an investigation by HarfangLab specialists.
The “Doppelgänger” operations were first publicly revealed in 2022, characterized by manipulative actions in the information sphere where operators exploit social media and media outlets to disseminate disinformation. The primary method involves mimicking popular news websites to spread fake news.
Fake sites are created to publish disinformation aimed at undermining trust in official Western media, manipulating public opinion, and destabilizing the political situation in target countries.
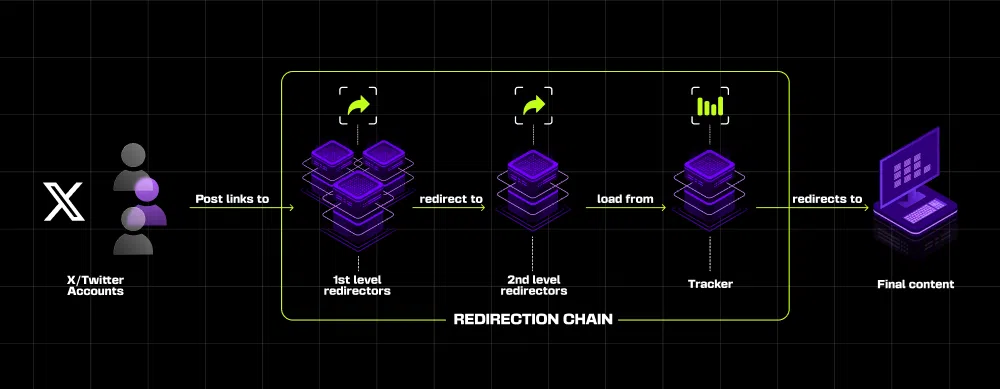
A complex chain of redirects, comprising several levels, is employed to distribute content. Social media accounts serve as the initial point, posting links to so-called “1st level redirector” — URLs leading to custom redirect pages. These pages contain metadata to generate link previews on platforms like X and instantly redirect to the next level, concealing the final disinformation site.
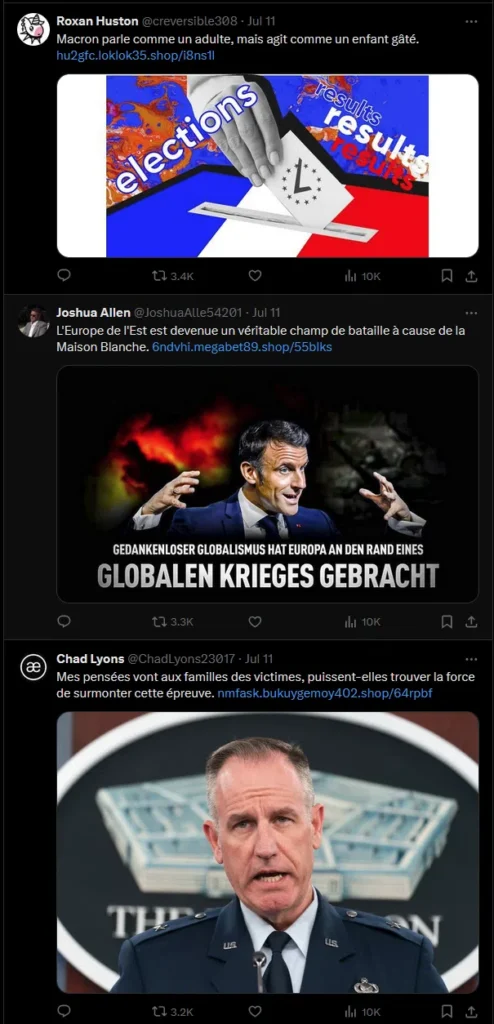
Twitter accounts sharing links to Doppelgänger’s infrastructure | Image: HarfangLab
Social networks, particularly X, are the main channels for disseminating disinformation. The investigation identified approximately 800 accounts posting links to redirect pages. These accounts often pose as cryptocurrency or Web3 influencers and do not belong to real individuals. The posts are likely AI-generated and written in multiple languages — English, French, German, Polish, and Ukrainian.
Post characteristics include unique content, high engagement levels artificially boosted, and the absence of repetitive comments, indicating the use of bots and networks to inflate interaction metrics.
The investigation uncovered several types of final sites linked by “Doppelgänger”:
- Fabricated news sites: primary sources of fake news. Examples include rrn[.]media, franceeteu[.]today, and derbayerischelowe[.]info.
- Doppelgänger sites of legitimate publications: mimic existing news outlets such as www.leparisien[.]wf and www.spiegel[.]ltd to lend credibility to the disinformation.
- Sites with a pronounced stance: legitimate sites publishing provocative materials. Examples include stratpol[.]com and liberationnews[.]org.
The content aims to discredit Western countries and support conservative views. The primary target countries are France, Germany, the USA, and Ukraine. The articles criticize Western politicians and actions, focusing on corruption, governance issues, and economic challenges in the target countries.
The disinformation strategy also attempts to appeal to different demographic groups. The ongoing “Doppelgänger” operations underscore the need for decisive measures and international cooperation to protect democratic processes.
In May, the European Union launched an investigation into Meta’s actions for potential violations of new rules ensuring electoral integrity before the European Parliament elections in June. One reason for the investigation was the “Doppelgänger” operation, which Meta disclosed in 2022. The covert influence campaign involved publishing fake articles disguised as genuine pieces from The Washington Post and Fox News, aimed at undermining Western influence on the global political situation.
Related Posts:
- Doppelgänger: Russia-Linked Influence Network Targets Germany with Disinformation
- Unmasking Meltdown: Alarming CPU Flaws Revealed
- APT29 Strikes German Politics with WINELOADER Malware Assault
- Operation ShadowCat Targets Indian Political Observers
- Espionage Campaign Returns: LightSpy Targets Southern Asia





