The Rise of Fake Online Meeting Websites Spreading Android and Windows RATs
The world runs on virtual meetings now. Skype, Zoom, and Google Meet have woven themselves into the fabric of business and personal communication. But, as with any popular technology, there’s a dark underbelly where cybercriminals lurk, ready to pounce on those who aren’t paying attention.
A new campaign has emerged, targeting users of popular online meeting platforms like Skype, Google Meet, and Zoom. Uncovered by Zscaler’s ThreatLabz in December 2023, this campaign marks a sophisticated attempt by threat actors to compromise both Android and Windows systems through the distribution of Remote Access Trojans (RATs).
What’s a RAT, and Why Should You Care?
A RAT is a type of malware. Once installed on your Android phone or Windows computer, it gives the attacker control over your device:
- Spying: They can tap into your webcam and microphone, recording everything you do and say
- Keylogging: Every password, credit card number, and sensitive message you type is theirs.
- Data Theft: Your files, photos, and anything else stored on your device are fair game.
The Scheme: How They Trick You

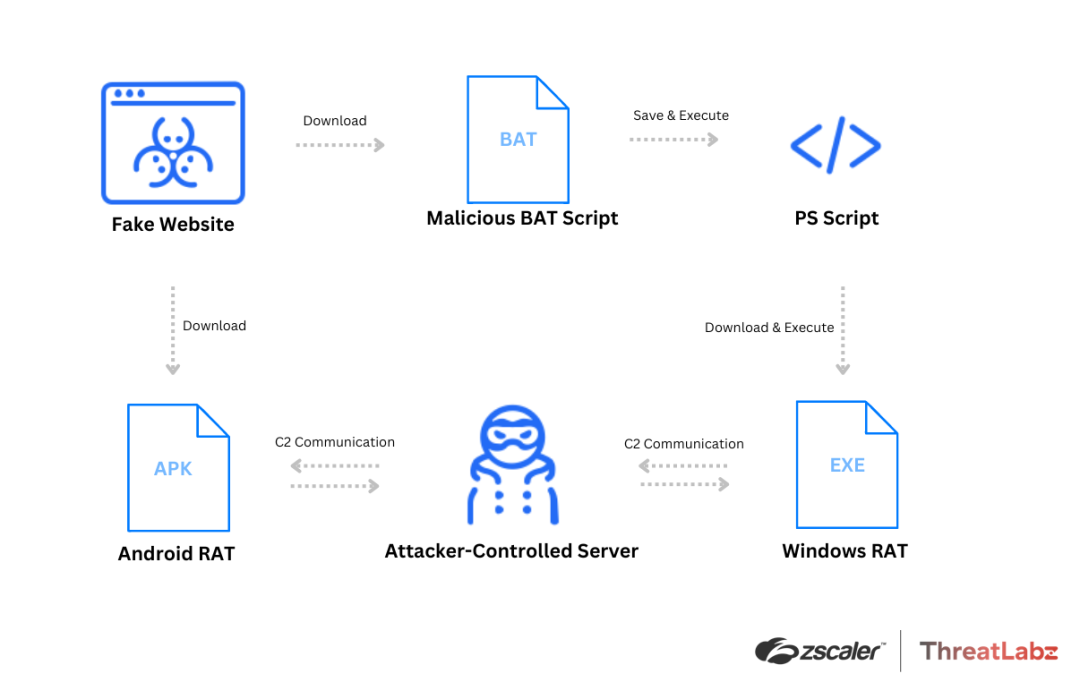
Attack chain and execution flow for Android and Windows campaigns
- Fake Websites: These sites are meticulous copies, using web addresses that look almost identical to the real thing. They even mimic the look and feel of genuine meeting applications.
- Skype Phishing: The domain
join-skype[.]infowas among the first spotted, cleverly designed to push a counterfeit Skype application. Interestingly, this scam seemed to sidestep iOS users, potentially indicating a strategic choice by the attackers to focus on what they perceive as more vulnerable targets. - Google Meet Imitation: Another domain,
online-cloudmeeting[.]pro, replicated Google Meet’s interface. Here, the subpath used to mimic a meeting link adds a layer of deceit, aiming to ensnare users looking to download the meeting app but leading them instead to malware. - Zoom Deception: Similarly, a fabricated Zoom site (
us06webzoomus[.]pro) was discovered, its URL was designed to mimic a legitimate meeting ID. The site hosted malicious files under the guise of Zoom applications, spreading SpyNote RAT through Android and DCRat through Windows.
- Skype Phishing: The domain
- Malicious Downloads: Clicking those familiar “Windows” or “Android” download buttons unleashes the RATs, cleverly disguised behind innocent-sounding file names.
- Total Control: Once the RAT gets a foothold on your system, the hackers can wreak havoc or quietly lurk in the background, siphoning your data for months.
Real-World Impact
Here’s how Zscaler uncovered the campaign:
- Skype Scam: Users thought they were getting Skype, but instead became victims of the SpyNote RAT (Android) or the NjRAT and DCRat (Windows).
- Google Meet & Zoom Mimicry: Fake Google Meet and Zoom sites, again with convincing URLs, were pushing variations of the same insidious RATs.
Protecting Yourself
Don’t let clever cybercriminals make you the next victim. Stay safe with these basic precautions:
- Check the Address: Before clicking any download, carefully examine the web address. Is it misspelled or using a strange domain name (like .info instead of .com)?
- Use Official Sources Only: Download meeting apps directly from the official Microsoft Store, Apple AppStore, or Google Play Store.
- Trust Your Gut: If something feels “off” about a website, even if you can’t pinpoint why, avoid it.
- Security Software: Keep your antivirus and anti-malware software up-to-date.





