The Stealthy Rise of Python Scripted Ransomware Attacks
In the Internet age, where cyber threats continually evolve, the rise of scripted ransomware marks a new era of digital extortion. This sophisticated form of malware, often written in common programming languages like Python, has recently surged, posing a significant threat to both organizations and individuals.
Researchers at K7 Labs uncovered an intriguing instance of ransomware coded in Python. This particular ransomware, compiled with Microsoft Visual C++, disguises itself with a PDF icon, deceiving users into executing it. Once activated, it performs various malicious activities, including making itself persistent in the startup folder and encrypting user data with the Fernet symmetric key encryption algorithm.
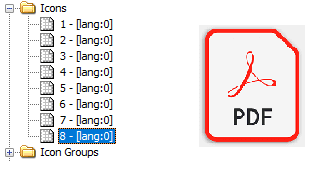
File icon as PDFicon | Image: K7 Labs
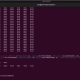
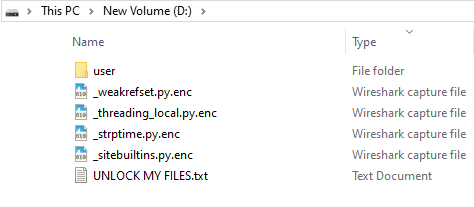
The ransomware operates by self-replicating to the startup folder, ensuring its activation with each system reboot. It then proceeds to encrypt files across the victim’s machine, appending a “.enc” extension to the encrypted files. Additionally, it drops a ransom note, “UNLOCK MY FILES.txt,” in each directory, detailing the attackers’ demands.

Encrypted files with .enc extension | Image: K7 Labs
Upon completion of the encryption process, a popup message informs the victim of the encryption, adding to the psychological impact of the attack. The ransomware then enters a sleep mode, possibly awaiting further instructions or updates from its creators.
This type of ransomware often infiltrates systems through phishing emails, malicious attachments, or compromised websites. Users, unaware of the lurking danger, inadvertently download and execute the ransomware payload, leading to the encryption of their data.
The emergence of scripted ransomware like this showcases the need for heightened cybersecurity measures. It’s not just the sophistication of the attack but also the ease with which it can be deployed that makes it particularly dangerous. As cybercriminals continue to evolve their tactics, staying informed and vigilant is more critical than ever.