threatspec
Threatspec is an open-source project that aims to close the gap between development and security by bringing the threat modeling process further into the development process. This is achieved by having developers and security engineers write threat modeling annotations as comments inside source code, then dynamically generating reports and data-flow diagrams from the code. This allows engineers to capture the security context of the code they write, as they write it. In a world of everything-as-code, this can include infrastructure-as-code, CI/CD pipelines, and serverless, etc. in addition to traditional application code.
Supported file types
At the heart of threatspec, there is a parser that reads source code files and processes any annotations found in those files. It uses a Python library called comment_parser to extract those comments. The comment_parser library determines the file’s MIME type in order to know which type of comments need to be parsed. The supported file MIME types are:
| Language | Mime String |
|---|---|
| C | text/x-c |
| C++/C# | text/x-c++ |
| Go | text/x-go |
| HTML | text/html |
| Java | text/x-java-source |
| Javascript | application/javascript |
| Shell | text/x-shellscript |
| XML | text/xml |
An unknown MIME type will result in a warning and the file will be skipped.
Summary of annotations
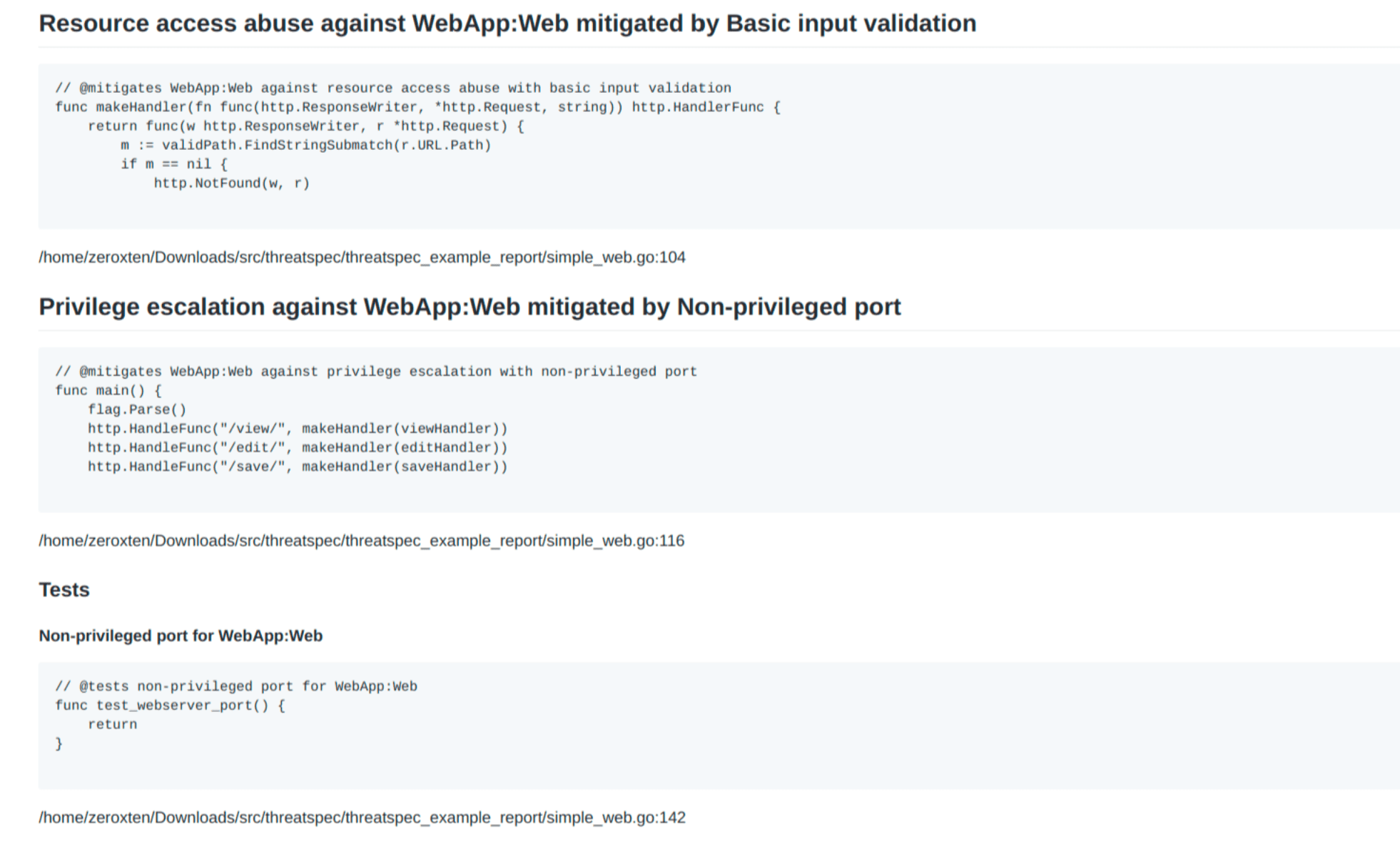
Here is a quick summary of each supported annotation type. For a full description, see the Annotations section below.
| Annotation | Example |
|---|---|
| @component – a hierarchy of components within the application or service. | @component MyApp:Web:Login |
| @threat – a threat | @threat SQL Injection (#sqli) |
| @control – a mitigating control | @control Web Application Firewall (#waf) |
| @mitigates – a mitigation against a particular threat for a component, using a control | @mitigates MyApp:Web:Login against Cross-site Request Forgery with CSRF token generated provided by framework |
| @exposes – a component is exposed to a particular threat | @exposes MyApp:CICD:Deployment to rogue code changes with lack of separation of duty |
| @accepts – the acceptance of a threat against a component as unmitigated | @accepts #api_info_diclosure to MyService:/api with version information isn't sensitive |
| @transfers – a threat is transferred from one component to another | @transfers auth token exposed from MyService:Auth:#server to MyService:Auth:#client with user must protect the auth token |
| @connects – a logical, data or even physical connection from one component to another | @connects MyService:Product:Search to MyService:Product:Basket with Add selected product to basket |
| @tests – the test of a control for a component | @tests CSRF Token for MyService:Web:Form |
| @review – a note for a component to be reviewed later | @review Web:Form Shouldn't this mask passwords? |
Install
Copyright (c) 2019 ThreatSpec