Trend Micro Report: Uncovering Lazarus APT Organizations for Malicious Software and Tools Used to against financial institutions
Foreign media on January 25, Trend Micro’s security experts recently released about the Lazarus APT organizations in the recent attacks on financial institutions, malware, and tools used.
Lazarus (transliteration “Lazarus”) is the number one threat to global financial institutions. The organization has been active since 2009 and it is assumed that as early as 2007, it has been involved in cyber espionage that destroyed data and undermined the system. According to the survey, Lazarus, a hacker group, has been linked to hacking events at Sony Pictures in 2014 and data bank leaks in Bangladesh in 2016.
In 2014 and 2015, Lazarus organized an upsurge of activity, with its members primarily using customized malware attacks, which some experts consider the organization’s attacks are complex.
In the last activity for financial companies, cyber espionage used a variant of the RATANKBA Trojan linked to Lazarus to launch a “puddle attack.”

It is reported that the virus known as RATANKBA is just one of the weapons in the arsenal of Lazarus. The malware has been active since the end of 2016, the most recent of which is targeting attacks on financial institutions.
Variants used in these attacks (TROJ_RATANKBA.A) provide a variety of payloads, including hacking tools and software for the banking system. Another new variant of RATANKBA (BKDR_RATANKBA.ZAEL – A) was discovered in June 2017, mainly using PowerShell scripts instead of the more traditional PE executables.
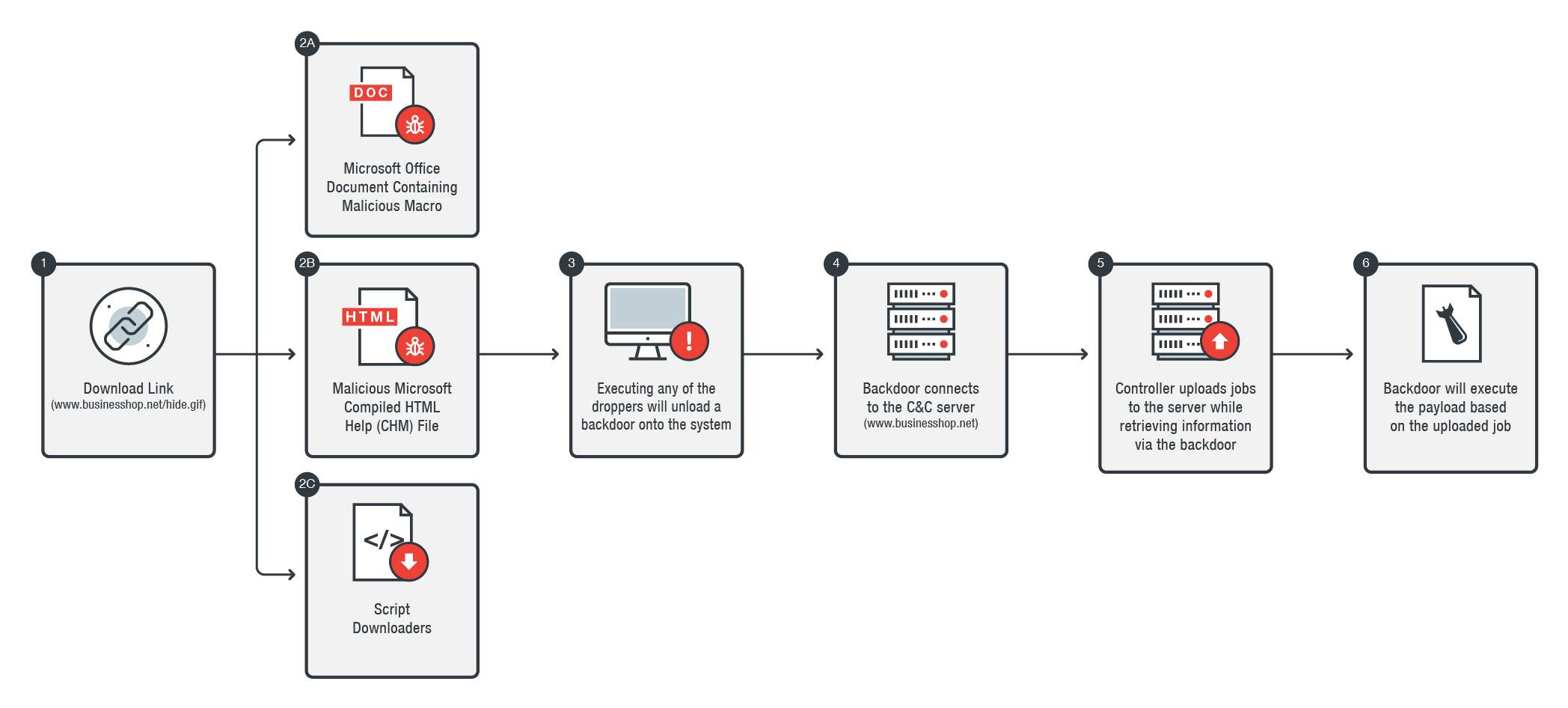
Experts note that the RATANKBA Trojans are delivered through weaponized Office documents that include topics related to cryptocurrency and software development, CHM files and script download. The attacker did not conduct real-time communication with the malware, and once the target machine fell, the attacker would use the remote controller tool to send the job to the system and the job queue was processed by RATANKBA to retrieve the collected information.
Malicious software RATANKBA infection process
The controller tools used by Lazarus APT have implemented a graphical UI that allows hackers to push code to servers and download victim profiles from them, the researchers said.
In this financial attack, researchers identified and invaded servers used by cyberspies to temporarily store stolen data and found that about 55% of the victims were in India and neighboring countries, most of whom did not use Microsoft software Business version. It is reported that the victim’s IP address does not belong to a large bank or financial institutions, Trend Micro may think that India is one of the three network software development companies or employees of a company in South Korea.
According to the profile of Lazarus APT members, Trend Micro speculates that hackers may be Korean natives. Now that Lazarus is adept at using a wide range of tools and technologies in its operations, it is likely that the organization will continue to update its attack strategy to optimize malicious activity.
Read more:
Source: SecurityAffairs





