TrendMicro Exposes Phishing Scheme Via DRACOON Links
In the shadowy realms of cyberspace, a sophisticated phishing campaign has been unearthed by vigilant security researchers from TrendMicro. This campaign cleverly leverages DRACOON.team, a reputed file-sharing platform, to ensnare unsuspecting victims with socially engineered emails. The emails, crafted with deceptive finesse, contain links that appear benign but serve a nefarious purpose: to lure the recipients into a trap set by the attackers.
Once an individual is beguiled into clicking the link, they are presented with a seemingly innocuous PDF document on DRACOON. However, embedded within this document is a secondary link, a digital Trojan horse leading to an attacker-controlled server. This imposter server, a facade of the Microsoft 365 login portal, operates as a reverse proxy. Its role is sinister – to pilfer login credentials and session cookies from the victims. Such stolen information is a cyber criminal’s key to bypassing even the robust multi-factor authentication, leaving personal and corporate data at their mercy.

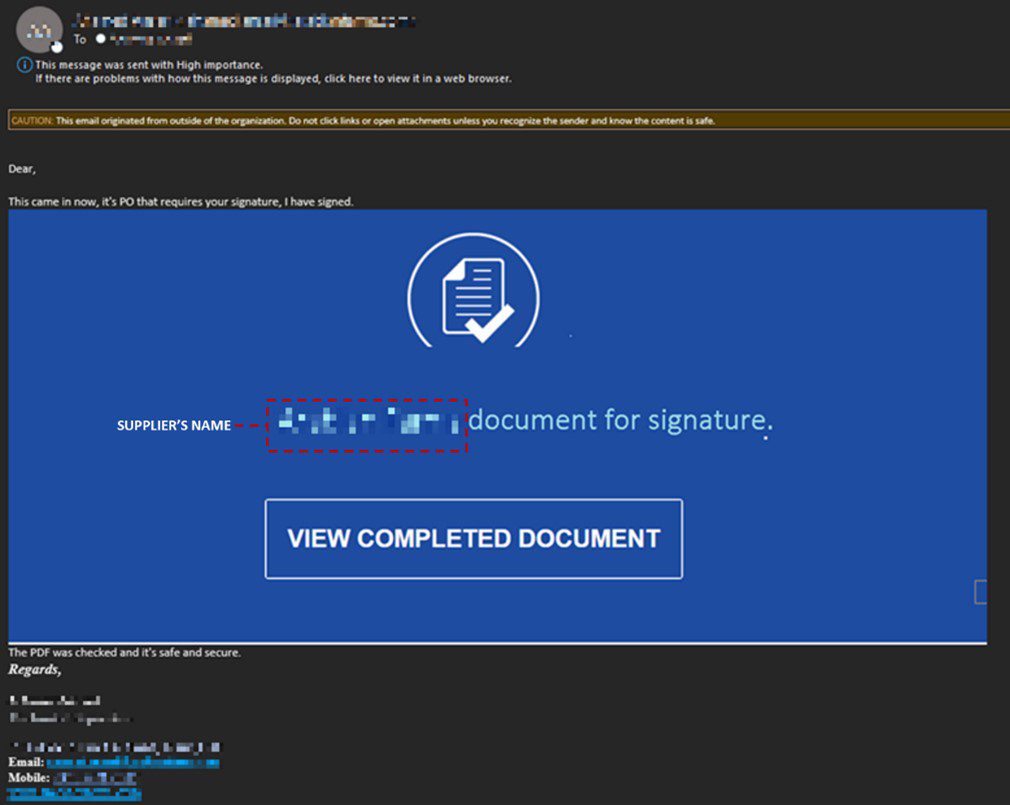
Screenshot of the phishing email | Image: Trendmicro
The ruse is intricate: the attacker-controlled reverse proxies act as cunning intermediaries. They provide the victims with genuine login forms and convey interactions to the actual Microsoft 365 login page. The tragedy unfolds swiftly; as soon as the victims enter their details, the attackers gain immediate and automated access to the user’s mailbox. The nefarious cycle perpetuates itself as the same phishing emails that snared the original victim are then dispatched to their contacts.
This technique’s audacity lies in its ability to subvert conventional email security measures. The initial link’s facade of legitimacy, stemming from a trusted file-sharing server, allows it to evade detection. The TrendMicro team, acting on this discovery, swiftly alerted the DRACOON team, who responded by purging the malicious attachments and sanctioning the culpable accounts.
The phishing email, masquerading as a purchase order, showcases the supplier’s name, adding to its veneer of credibility. The PDF file, hosted on DRACOON and accessible without download, redirects the user to a falsified Microsoft 365 login page. Here, a reverse proxy lies in wait to execute the credential theft. A closer inspection of the login page’s source code exposes a JavaScript file responsible for credential harvesting.
The vigilance of TrendMicro’s Trend Managed Extended Detection and Response (MxDR) played a pivotal role in tracing the attack’s sequence. It identified the phishing email’s journey to the Outlook inbox, the victim’s interaction with the Dracoon-hosted PDF, and their unwitting step into the credential harvesting site. This thorough investigation by the MxDR team, combined with an assessment of the phishing attack’s impact, is critical in containing the breach and securing the digital perimeter.





