tumblerf: unified fuzzing framework for low-level RF and HW protocol/PHY/MAC analysis
TumbleRF: RF Fuzzing Framework
TumbleRF is a framework that orchestrates the application of fuzzing techniques to RF systems. While fuzzing has always been a powerful mechanism for fingerprinting and enumerating bugs within software systems, the application of these techniques to wireless and hardware systems has historically been nontrivial due to fragmented and siloed tools. TumbleRF aims to enable RF fuzzing by providing an API to unify these techniques across protocols, radios, and drivers.
Install
Create a Python 2.7 virtaulenv and activate it:
virtualenv -p $(which python2.7) py2-virtualenv
source py2-virtualenv/bin/activate
Clone the repo:
git clone https://github.com/riverloopsec/tumblerf.git pip install -r tumblerf/requirements.txt
Use
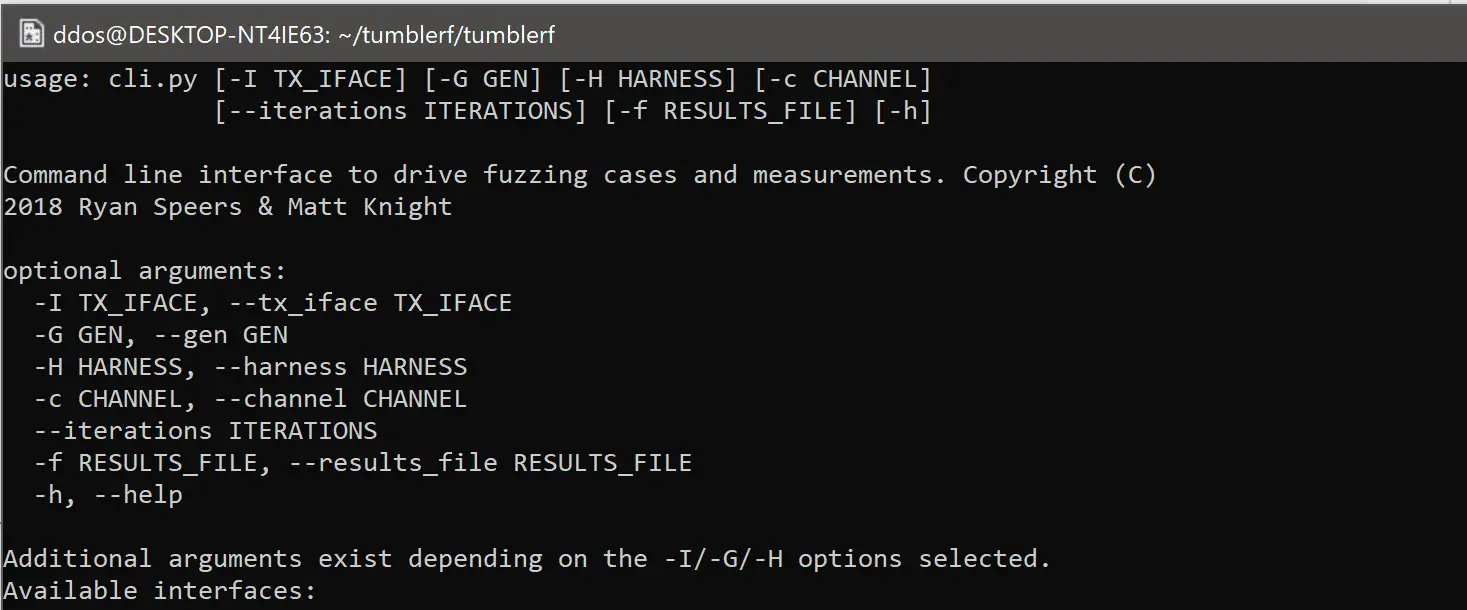
Running ./tumblerf/cli.py will tell you what interfaces, generators, and harnesses are available so you can define each.
A very simple run case can be done based on something like the following. This just transmits random frames from one device to another which looks to see if it got them, and is thus uninteresting. However, it demonstrates how we pick the second interface to use for TX.
NOTE: If you see errors such as the below, you may have a permission issue accessing your USB devices. You may correct this via your OS and permissions, or you may run with sudo (not recommended…).
Source: https://github.com/riverloopsec/





