TunnelCrack: Unearthing the Hidden Flaws in VPN Security

Virtual Private Networks (VPNs) have become synonymous with online privacy and security, providing an encrypted tunnel for your data as it travels across the internet. They’re designed to keep your online activities secure and inaccessible to prying eyes. But what happens when the very tool designed to protect your privacy becomes a conduit for attacks? Meet “TunnelCrack,” a shocking revelation that has sent shockwaves through the cybersecurity world.
A research team led by Nian Xue from New York University has unearthed two significant vulnerabilities in VPNs that have been lurking undetected since 1996. These flaws, present in virtually every VPN product across platforms, can be exploited to leak and read user traffic, steal information, or even launch attacks on user devices.

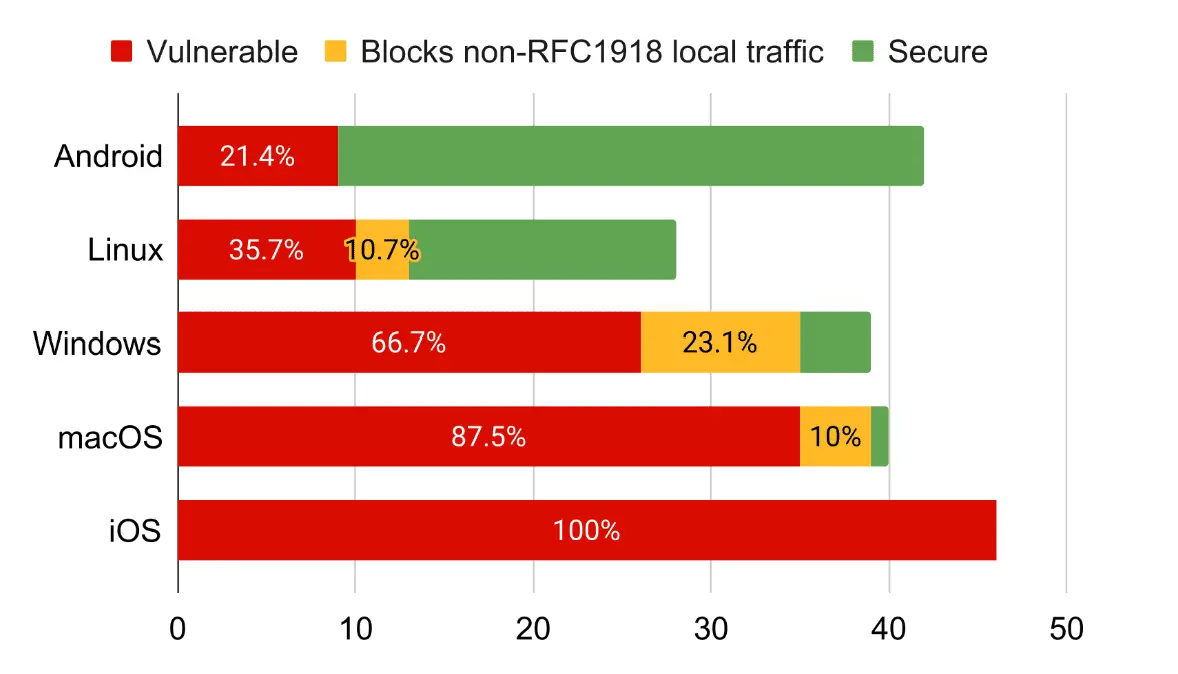
The vulnerabilities have been dubbed “LocalNet” and “ServerIP” attacks. While iOS, iPads, MacBooks, and macOS are most likely to be affected, Windows and Linux aren’t entirely immune. Android seems to be the safest, with only about one-fourth of VPN apps being vulnerable.
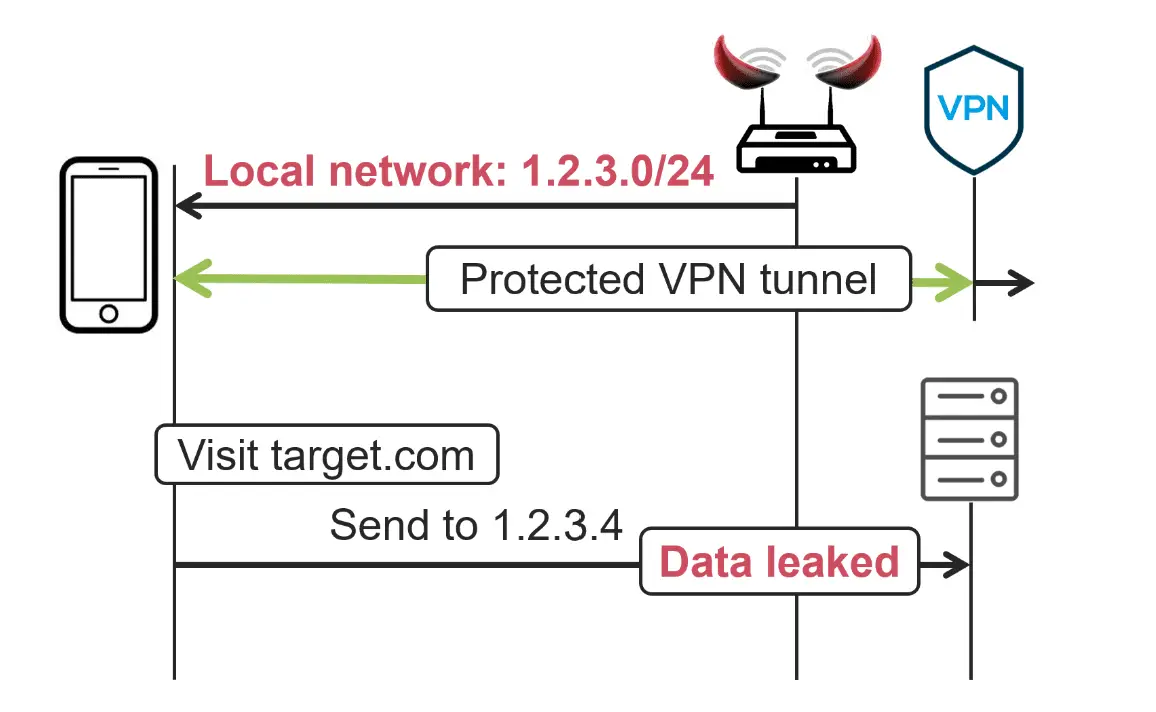
LocalNet attacks exploit the routing exceptions in VPNs, specifically the rules that allow traffic to and from local networks and the VPN server. An attacker can trick the VPN client into sending traffic outside the secure tunnel by manipulating these exceptions.
An example is the adversary setting up a malicious Wi-Fi network (e.g., “starbucks”) and assigning a public IP address and subnet to the victim. The victim’s traffic, instead of passing through the secure tunnel, is sent outside, making it easy prey for interception.
Most shockingly, all VPN apps on iOS and almost all on macOS were found to be vulnerable. Windows, Linux, and Android also showed varying degrees of vulnerability.
ServerIP attacks take a different but equally effective approach. Here, the attacker spoofs the IP address of the VPN server. By altering the DNS response, the adversary redirects the victim’s traffic to the wrong IP address. The victim’s requests to specific websites are then sent outside the protected VPN tunnel, leaking the web request.
Cybersecurity researchers have released guides and scripts to help users assess whether their VPN service is affected by the TunnelCrack vulnerability.
Built-in VPN clients of Windows, macOS, and iOS were found to be most vulnerable to this type of attack, with Android 12 and higher remaining unaffected.
Some VPN providers have already patched these vulnerabilities, including Mozilla VPN, Surfshark, Malwarebytes, and Cloudflare’s WARP. Users can also take measures such as disabling local network access or ensuring the use of HTTPS to mitigate these attacks.