Turla APT Unmasked: New Tools and Tactics in Latest Attacks
Researchers at Talos and CERT.NGO have pulled back the curtain on new malicious components deployed by the notorious Turla APT group, exposing a sophisticated web of tools engineered for stealthy intrusion. This in-depth analysis underscores Turla’s evolving methods to infiltrate targets and pilfer sensitive data.
The Command and Control (C2) server
Turla APT C2 servers | Image: Cisco Talos
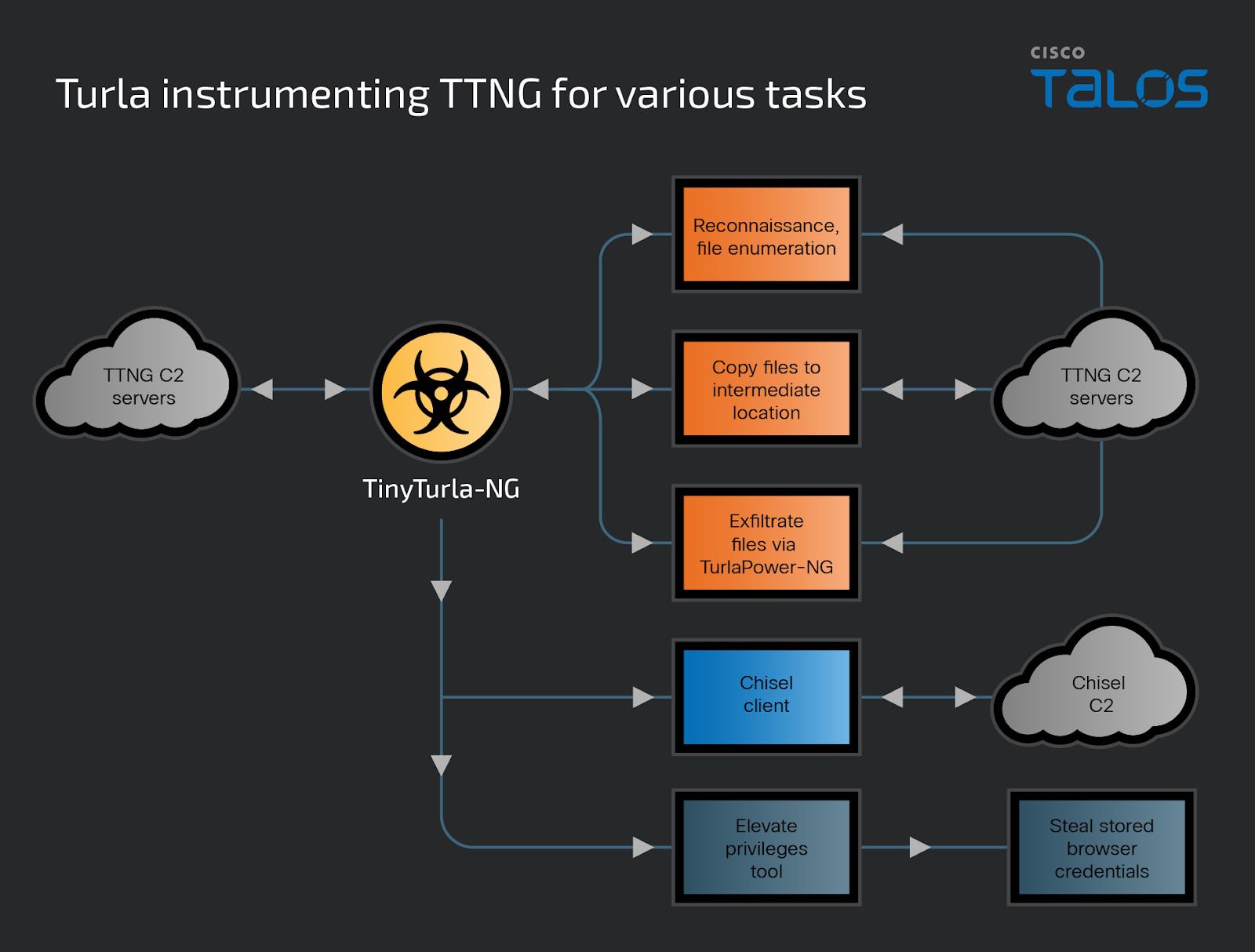
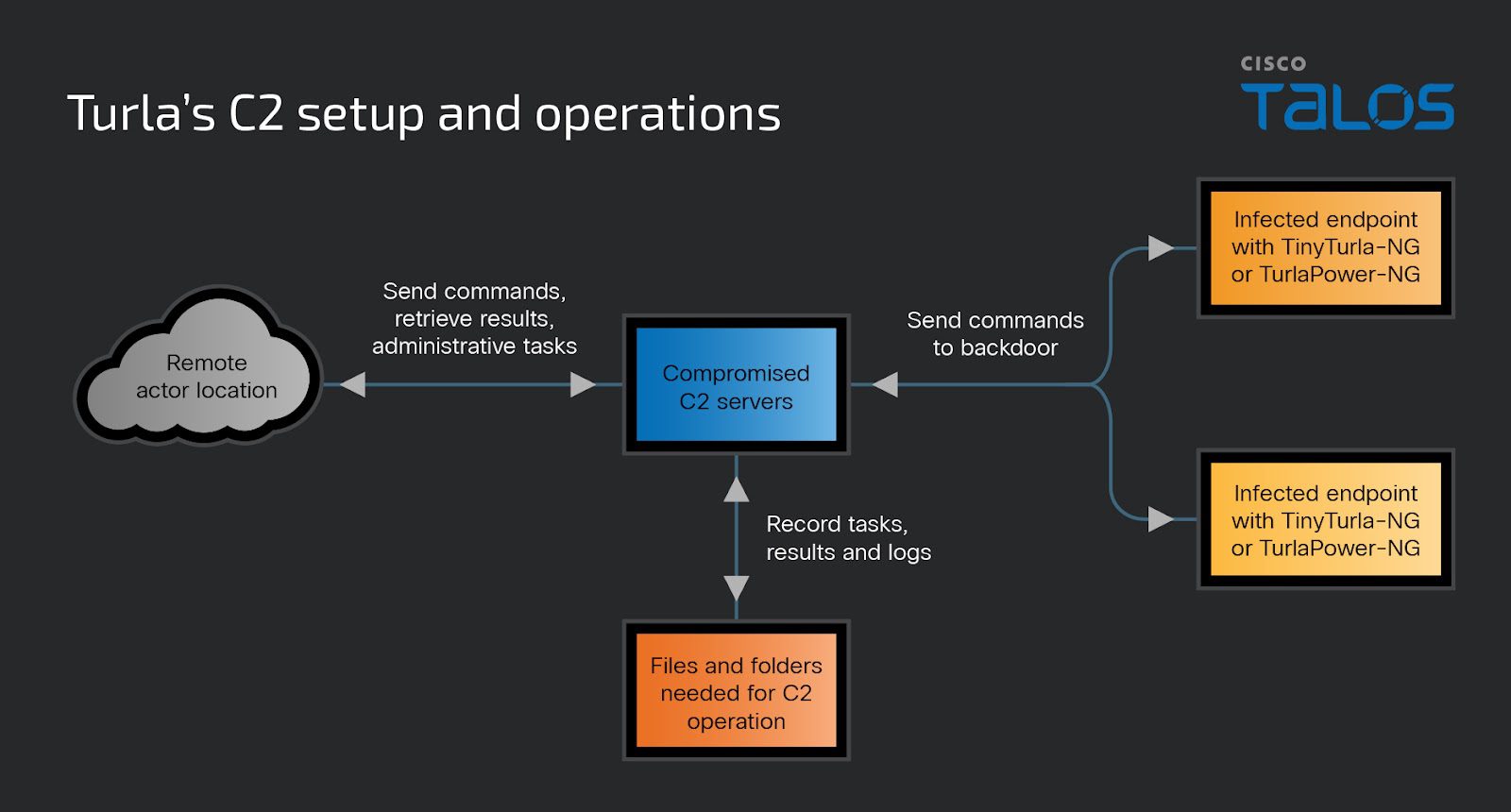
At the heart of Turla’s latest cyber offensive are the command and control (C2) servers, running PHP-based scripts with dual functionalities. These servers not only act as puppeteers for the TinyTurla-NG (TTNG) and TurlaPower-NG implants but also serve as a web shell, enabling the remote execution of commands directly on the compromised servers. This dual capability illustrates Turla’s strategic pivot towards versatility and stealth in cyber operations.
Upon activation, the C2 script meticulously constructs a file structure to support the TTNG backdoor operations. It demonstrates an acute awareness of operational security, checking for the existence of a logging directory and validating COOKIE IDs to authenticate commands. This intricate setup allows Turla operators to remotely administer a slew of commands, from data exfiltration to task allocation for their malicious payloads.

Turla APT Tasks | Image: Cisco Talos
Technical Breakdown
-
C2 Communication
- Turla operators issue commands and tasks to infected machines via the C2 script. TTNG or TurlaPower-NG implants parse HTTP requests containing parameters like “task,” “rm_file” and “get_result” to determine actions. This layered approach minimizes direct interaction with compromised C2 servers.
-
Precision Reconnaissance:
- Modular PowerShell scripts are delivered to TTNG-infected systems, enabling attackers to map out and identify specific files of interest. This focused approach allows for selective exfiltration.
-
Persistence & Evasion:
- The modified Chisel client establishes a reverse SOCKS proxy. This provides Turla with covert persistence on compromised networks. Further, embedded TLS certificates offer insight into the campaign’s timeline, suggesting a likely start date in December 2023.
-
Auxiliary Tooling:
- For privileged command execution, Turla uses a binary designed to impersonate other active processes. This obscures malicious activities within legitimate system operations.
- Targeted PowerShell scripts maximize credential theft by extracting saved login data from the victims’ Chrome and Edge browsers.
Implications
This in-depth analysis highlights the adaptability and increasing sophistication of state-sponsored threat actors like Turla. Their evolving toolset and stealth-first approach necessitate proactive defense measures.