UAT-5647 Unleashes RomCom Malware in Attacks on Ukraine and Poland
In a sophisticated and persistent cyber campaign, the UAT-5647 threat actor group, known for its ties to Russian-speaking adversaries, has launched a series of targeted attacks against Ukrainian government and Polish entities, deploying variants of the notorious RomCom malware. Researchers Dmytro Korzhevin, Asheer Malhotra, Vanja Svajcer, and Vitor Ventura from Cisco Talos have been tracking this group’s activities since late 2023, detailing a campaign that leverages a broad range of malicious tools to infiltrate critical systems.
UAT-5647 has long been recognized for its multi-motivational attacks, ranging from espionage to ransomware deployment. However, the current wave of attacks shows an increased focus on establishing long-term access to exfiltrate sensitive data before potentially pivoting to ransomware operations. Cisco Talos assesses that “this specific series of attacks… is likely meant to serve UAT-5647’s two-pronged strategy”: first, to exfiltrate valuable data and, second, to use ransomware as a disruptive and financially motivated follow-up.
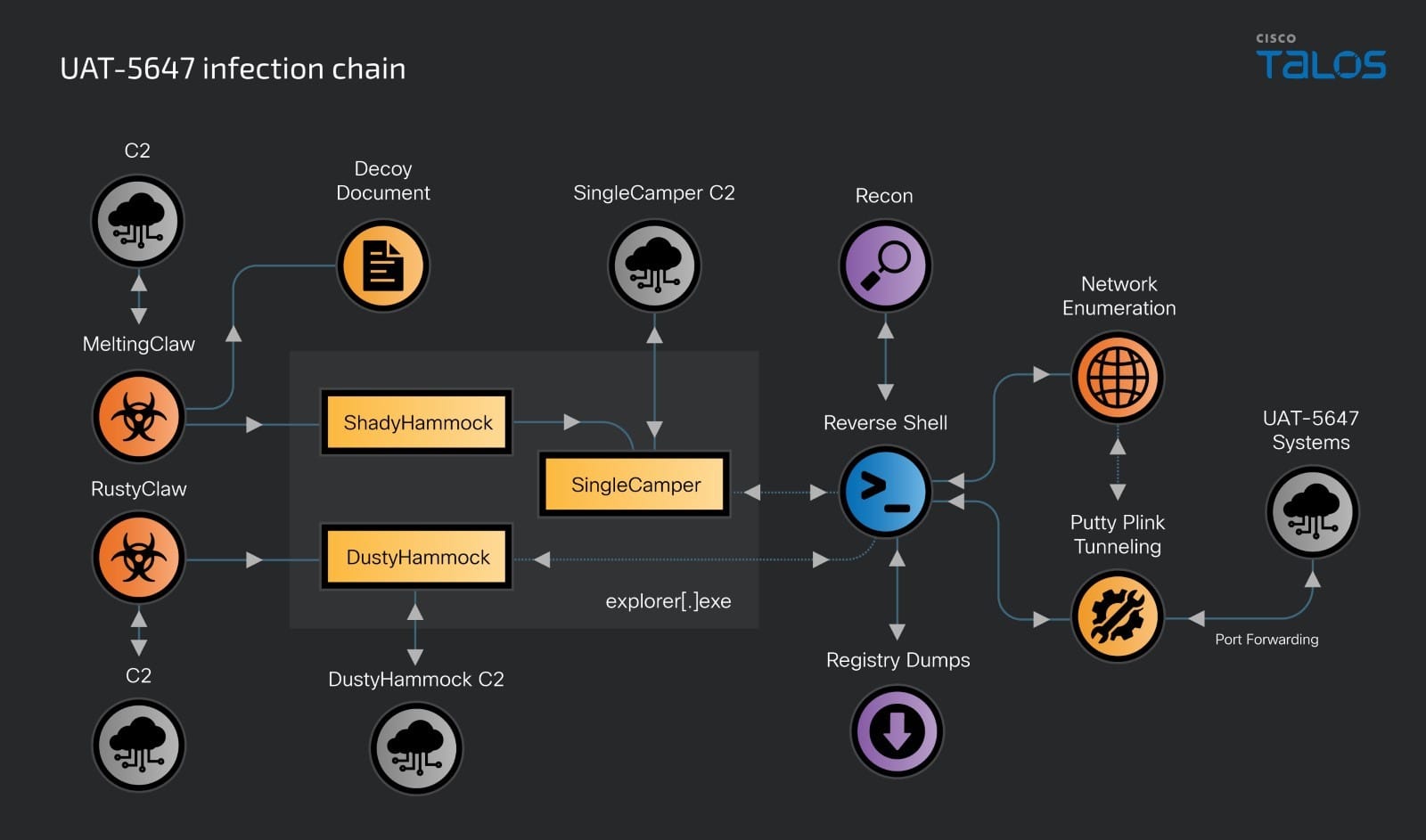
At the center of this campaign are RomCom malware variants, deployed through an updated infection chain. UAT-5647 has significantly upgraded its tooling, deploying four distinct malware families: RustClaw, MeltingClaw (downloaders), and two backdoors known as DustyHammock (written in Rust) and ShadyHammock (written in C++). These malicious components allow the group to infiltrate systems, perform lateral movement, and establish persistent access.
According to the report, the RomCom malware, also referred to as SingleCamper, is delivered via ShadyHammock, a backdoor responsible for loading and executing payloads directly from the Windows registry. This stealthy delivery mechanism makes detection difficult, as the malware “is loaded directly from registry into memory and uses a loopback address to communicate with its loader.”
The campaign’s focus on Ukrainian and Polish entities is clear, with a particular interest in government agencies and infrastructure. The use of keyboard layout checks further supports this, with the malware verifying whether the system uses Polish, Ukrainian, or Russian language settings before initiating its malicious activities. This deliberate targeting indicates that the group is carefully selecting its victims based on strategic and geopolitical interests.
UAT-5647’s infection chain typically begins with a spear-phishing attack, which delivers a downloader such as RustClaw or MeltingClaw. These downloaders establish persistence and then deploy the backdoors, allowing UAT-5647 to conduct detailed network reconnaissance, compromise systems, and exfiltrate valuable data. “DustyHammock is a more straightforward backdoor,” the report explains, used for “communicating with its command and control (C2) and performing malicious actions”, while ShadyHammock carries out more complex tasks, such as managing payloads like SingleCamper.
Once inside a network, UAT-5647 performs a series of activities to maintain access and evade detection. The group is particularly adept at using legitimate tools like PuTTY’s Plink to establish remote tunnels, a technique that allows them to “tunnel internal interfaces to external, remote hosts”, effectively bypassing standard security measures.
In one documented case, the attackers leveraged a compromised TP-LINK Wireless G Router to forward traffic from an infected network to their remote server. This enabled them to brute force or spray passwords, exfiltrate configuration data, and further compromise the targeted system.
As UAT-5647 continues to evolve its malware and attack techniques, organizations in Ukraine, Poland, and other regions at risk must remain vigilant.
“UAT-5647 has accelerated their attacks in recent months,” the report concludes, urging defensive teams to prioritize proactive detection and rapid response measures.





