Unfading Sea Haze: A New Cyber Espionage Threat in the South China Sea
Bitdefender Labs has uncovered a previously unknown cyberespionage group, dubbed “Unfading Sea Haze,” responsible for a string of attacks targeting high-level government and military organizations in the South China Sea region. This revelation comes after an extensive investigation that delved into the group’s historical activities, uncovering a trove of advanced tools and tactics dating back to 2018.
The researchers likened the analysis of Unfading Sea Haze’s malware arsenal to a “museum exposition of cyberespionage relics,” revealing a fascinating evolution of tools and techniques. The group primarily relied on variants of the infamous Gh0st RAT malware, alongside custom .NET payloads and a tool called Ps2dllLoader, designed for fileless attacks that evade traditional security measures.
In recent years, Unfading Sea Haze has shifted towards even more sophisticated tactics, incorporating dynamic elements, in-memory execution, and even the use of commercially available Remote Monitoring and Management (RMM) tools. This approach, uncommon for nation-state actors, demonstrates the group’s adaptability and determination to remain undetected.
Anatomy of Unfading Sea Haze Attacks

Initial Compromise
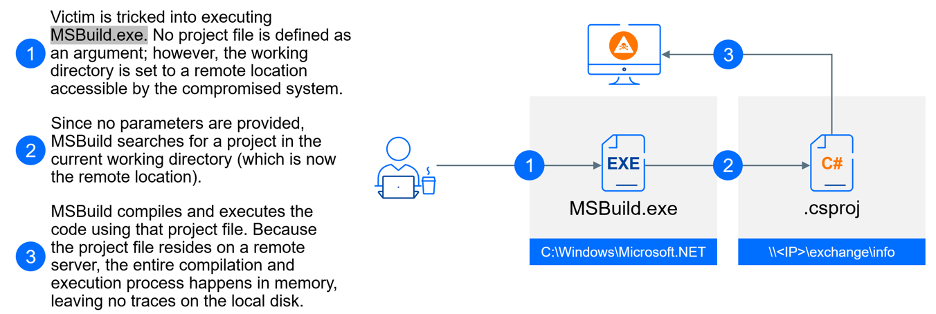
The exact method of initial compromise remains unknown due to the historical nature of the attacks. However, recent activities indicate the use of spear-phishing emails with malicious LNK files hidden within ZIP archives. These files executed commands designed to evade detection and establish a foothold in victim systems.
Persistence
Unfading Sea Haze employed scheduled tasks and DLL sideloading techniques to maintain persistence. They mimicked legitimate Windows files and used common programs to execute malicious payloads, demonstrating a sophisticated understanding of the Windows environment.
Data Collection
The primary objective of these attacks was espionage. The attackers used custom tools such as the xkeylog keylogger and a browser data stealer to gather sensitive information from compromised systems. They also employed manual techniques, using compression tools like rar.exe to archive and exfiltrate data.
Data Exfiltration
Initially, data exfiltration was performed using a custom tool named DustyExfilTool. However, since January 2022, the attackers shifted to using the curl utility and FTP protocol, with dynamically generated credentials to enhance operational security.
Attribution Challenges and Geopolitical Implications
While definitive attribution remains elusive, several factors point towards a potential link between Unfading Sea Haze and Chinese interests. The targeted victims, the use of tools popular among Chinese actors, and similarities to techniques employed by known Chinese APT groups all contribute to this assessment.





