Unmasking “Marko Polo”: The Infostealer Gang Targeting Thousands
Researchers at Recorded Future have uncovered a large-scale cyberattack affecting tens of thousands of devices worldwide. It was later revealed that the campaign was orchestrated by the hacker group Marko Polo, specializing in cryptocurrency fraud and online gaming scams.
Experts from the Insikt Group, a division of Recorded Future, discovered that the primary targets of the attackers were prominent gamers, cryptocurrency influencers, and IT professionals. The hackers likely select their targets based on the victim’s capacity to suffer substantial financial losses in the event of a successful attack.
Marko Polo operates through a well-practiced scheme: members of the group contact potential victims via social media, posing as HR personnel or recruiters. They offer enticing job opportunities and direct the victims to malicious websites where they unknowingly download infected software.
Researchers characterize Marko Polo as a “traffer team” driven by financial motivation. The group consists of Russian, Ukrainian, and English-speaking members, with leadership and key operators likely based in post-Soviet countries.
During the investigation, the Insikt Group uncovered more than 30 different fraudulent schemes on social media connected to Marko Polo. Additionally, the hackers compromised over 20 software builds used for Zoom video conferencing. These malicious versions are distributed via targeted phishing on social networks, disguised as legitimate clients but contain the Atomic macOS Stealer (AMOS) trojan.
In addition to attacks through fake Zoom versions, Marko Polo engages in hacking commercial software and injecting malicious code into files distributed via the BitTorrent protocol. The group disguises itself as various blockchain projects, online games, office applications, and video conferencing tools.
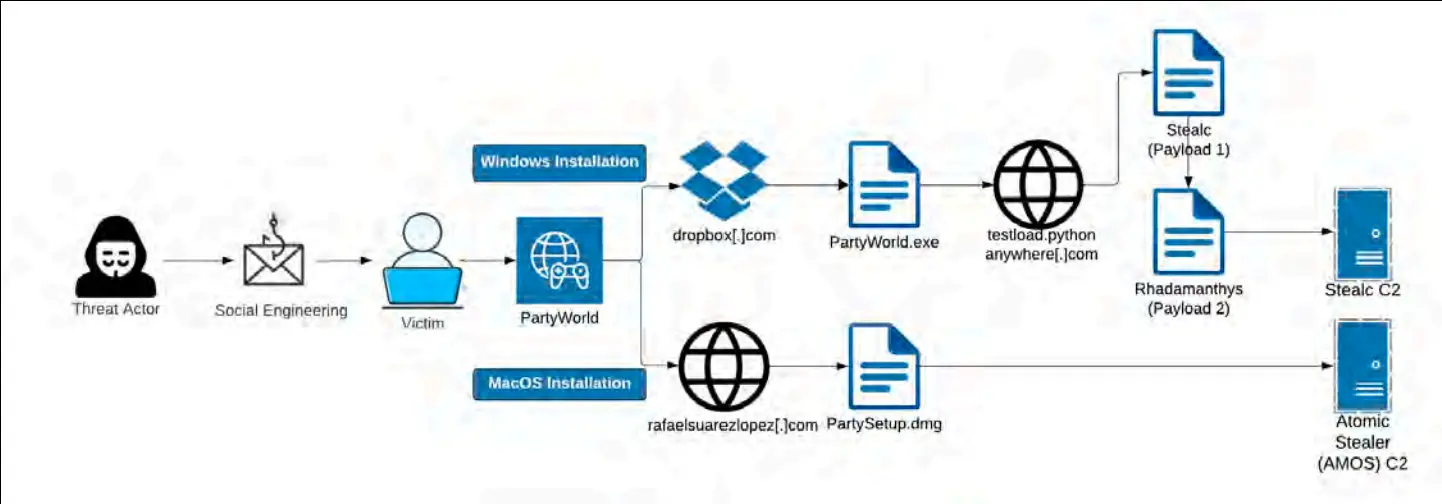
One of the most extensive fraudulent campaigns was dubbed PartyWorld. In this scheme, the attackers mimic popular games such as Fortnite and Party Icon, promoting them through social media. Users visiting the PartyWorld site are prompted to download a game client for Windows or macOS. In reality, instead of a game, an infostealer is installed on the device.
Another campaign, known as Nortex, uses a messenger, office application, and social network as a cover. The hackers created a fake version of the Web3 project SendingMe, through which, instead of the promised functionality, victims receive the HijackLoader and Stealc trojans.
According to researchers, the Marko Polo attacks have already led to the leakage of confidential personal and corporate data from numerous users. It is estimated that the group’s illicit gains amount to millions of dollars. The Insikt Group discovered reports from victims who had lost all their savings due to the hackers’ activities.
Marko Polo is particularly dangerous due to its ability to quickly adapt to detection efforts. The group regularly changes the names of its fraudulent schemes, updates its infrastructure, and modifies its tactics to bypass security measures. Experts note that this flexibility not only makes Marko Polo a persistent threat but also suggests that the group will continue to refine its methods to stay one step ahead of cybersecurity systems.




