Unmasking Meltdown: Alarming CPU Flaws Revealed
In an age where computer security is of paramount importance, few vulnerabilities have sent ripples through the tech industry as much as Meltdown and its variants. While measures have been taken to address these vulnerabilities, a team of astute researchers from the CISPA Helmholtz Center for Information Security in Saarbrücken, Germany, have uncovered new alarming facets of these CPU flaws. The revelations come from two deep-diving studies, with results that may change the way we perceive our computer’s safety.
Peering Deeper into Meltdown
Daniel Weber, Fabian Thomas, Lukas Gerlach, Ruiyi Zhang, and Michael Schwarz undertook a detailed analysis of the lingering remnants of the original Meltdown attack (Meltdown-US) and its variant, Meltdown 3a.
1. The “Original” Meltdown-US Vulnerability:

The groundbreaking paper titled “Indirect Meltdown: Building Novel Side-Channel Attacks from Transient-Execution Attacks” unveiled a twist to the Meltdown narrative. By adding an indirect layer to the attack, Meltdown shifts from being a transient execution attack to a stealthier side-channel attack. Instead of leaking actual data, this new approach divulges metadata.
Key Findings:
– Despite software mitigation efforts, attackers can still glean metadata from separate security domains by observing non-secret data through Meltdown.
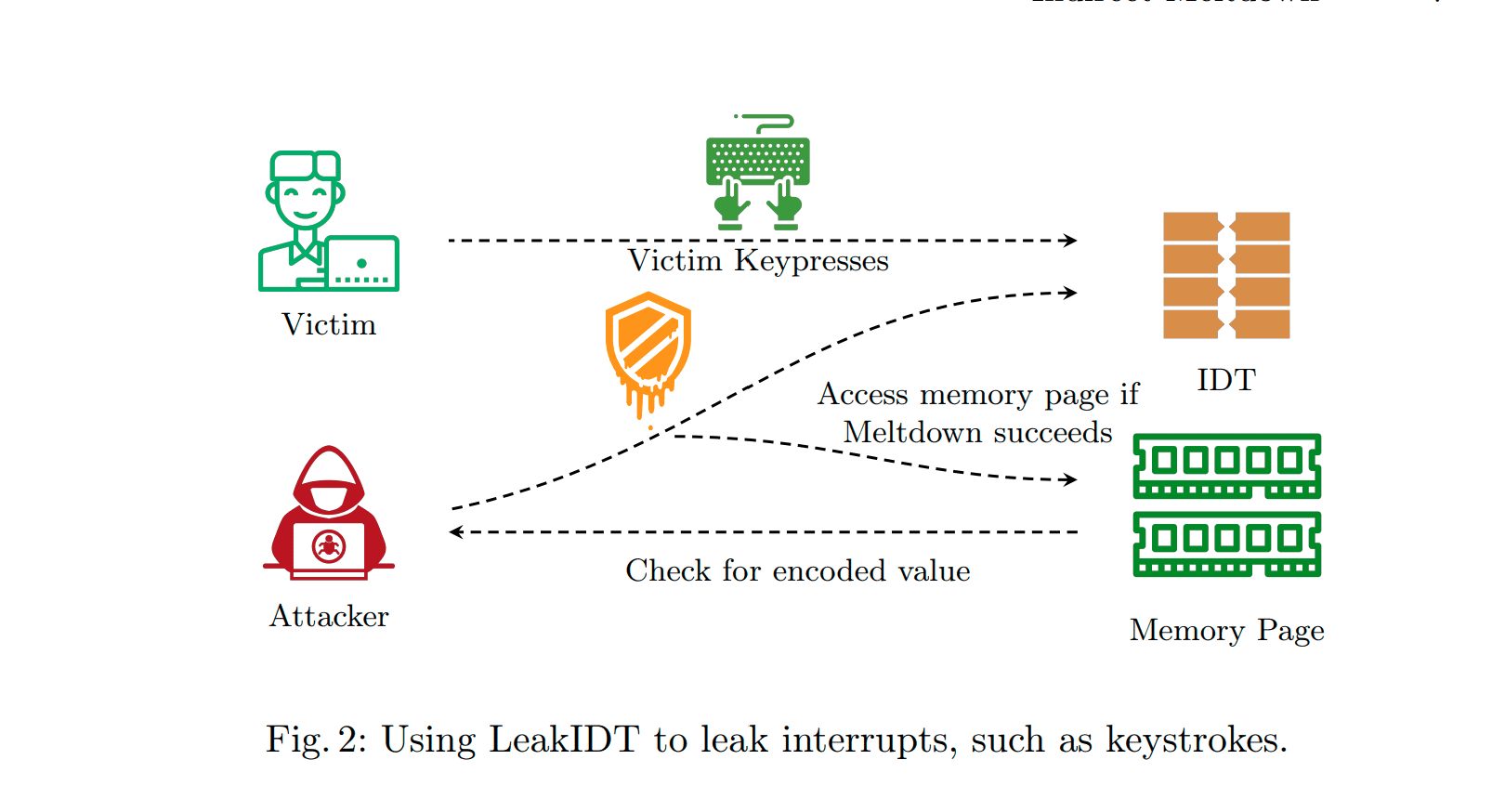
– Their technique, dubbed LeakIDT, offers a unique way to monitor kernel addresses at cache-line granularity, allowing the tracking of interrupt activities like keystrokes and web visits.
Impact:
This discovery magnifies the potential of Meltdown to intrude into users’ daily activities, even when merely using regular apps. Moreover, with Kernel-page-table isolation (KPTI) not unmasking all memory pages, Meltdown reveals the cache state, enabling attackers to infer interrupt activities.
Proof-of-concept implementation for the paper “Indirect Meltdown: Building Novel Side-Channel Attacks from Transient Execution Attacks” is available on Github.
Mitigation:
While neither Intel nor AMD have announced mitigation strategies, the research suggests marking the vulnerable memory pages, such as IDT, as non-cacheable. Achieving this requires the use of memory-type range registers (MTRR) or tweaking the corresponding page-table entries.
2. The Mysterious Meltdown 3a:
Diving into Meltdown 3a through their study “Reviving Meltdown 3a“, the researchers unveiled surprising inconsistencies across different CPUs.
Key Findings:
– A thorough analysis across 19 distinct CPUs revealed diverse impacts. Surprisingly, the latest AMD CPUs (Zen3+) still fall prey to the vulnerability, while recent Intel models appeared unaffected.
– Beyond the known patches, Meltdown-CPL-REG remains exploitable, endangering cryptographic algorithms and breaching kernel-level security measures.
Impact:
Local unprivileged users can still access certain system registers. The main security concern currently centers around unauthorized access to performance counters, opening doors to potential side-channel attacks.
Proof-of-concept implementation for the paper “Reviving Meltdown 3a” is available on Github.
Mitigation:
Again, neither of the tech giants—Intel nor AMD—have publicized any mitigation plans. The onus now falls on developers to be vigilant about potential unauthorized access and take preventive measures, especially during context switches.
Conclusion
Meltdown and Meltdown 3a are two serious security vulnerabilities that affect CPUs from Intel, AMD, and other vendors. Users should be aware of these vulnerabilities and take steps to protect themselves.





