Unpatched Gogs Vulnerabilities: A Ticking Time Bomb for Source Code
SonarSource, a leading code security firm, has uncovered four unpatched vulnerabilities in Gogs, a popular open-source self-hosted Git service. With over 44,000 stars on GitHub and more than 90 million Docker image downloads, Gogs is widely used by developers worldwide. These vulnerabilities, which remain unaddressed by the Gogs maintainers, could allow attackers to steal source code, plant backdoors, wipe entire code repositories, and compromise server security.
image: Sonarsource
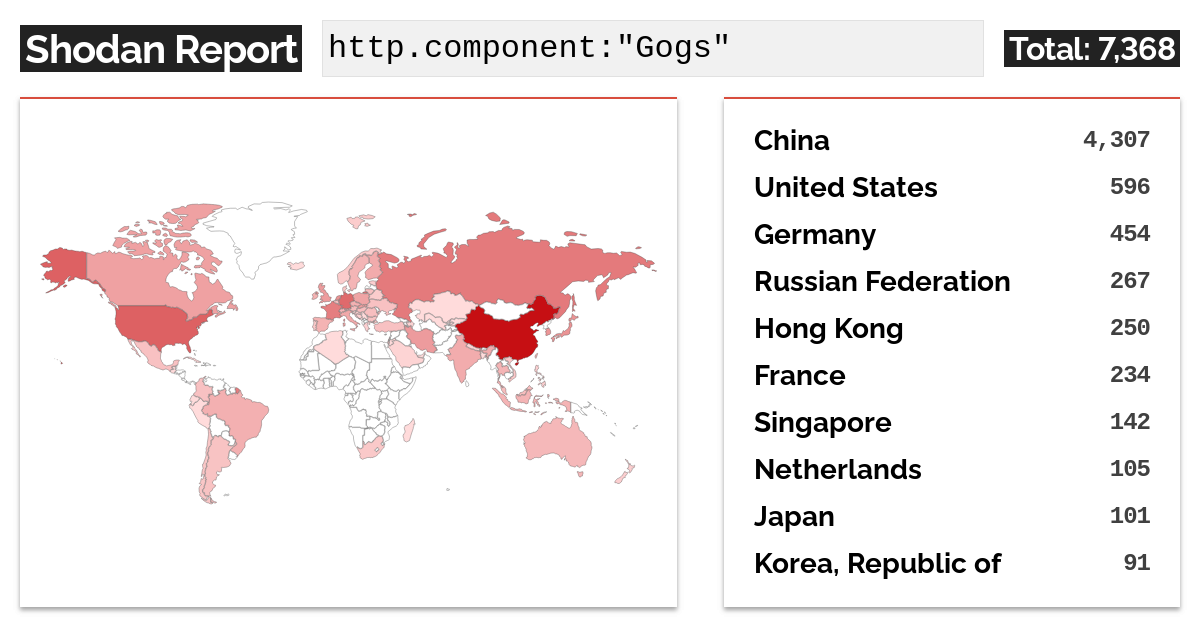
The vulnerabilities affect all current versions of Gogs (up to 0.13.0) and pose a significant risk to the estimated 7,300 open Gogs instances online. While there is no confirmed evidence of active exploitation, the potential impact is severe, potentially affecting thousands of organizations relying on Gogs for code management. The vulnerabilities reported to the maintainers of Gogs but unfortunately left unpatched, allow attackers to compromise vulnerable instances in several devastating ways.
The vulnerabilities, ranging from argument injection to file deletion, enable attackers to execute arbitrary commands on the Gogs server, gain unauthorized access to sensitive data, and manipulate code repositories. This could lead to data breaches, intellectual property theft, and significant disruptions to development operations.
SonarSource has released mitigation recommendations and patches for affected users. Key actions include disabling the built-in SSH server, turning off user registration, and applying the patches provided by SonarSource. However, the most effective solution is to migrate to Gitea, a more actively maintained fork of Gogs that has already addressed these vulnerabilities.
SonarSource has published a detailed analysis of the vulnerabilities, including technical details, exploit scenarios, and mitigation steps. Users are encouraged to review this information and take appropriate action to safeguard their systems.





