Urgent Chrome Update: Active Zero-Day Exploit Detected (CVE-2024-7971)

Google has released an urgent Chrome update (version 128.0.6613.84/85) in response to an actively exploited zero-day vulnerability (CVE-2024-7971). This vulnerability, categorized as a type confusion issue in the V8 JavaScript engine, poses a significant risk to users.
Type confusion vulnerabilities can allow attackers to execute malicious code on a victim’s machine, potentially leading to data theft, unauthorized access, or installation of malware. The fact that an exploit for CVE-2024-7971 is already being used in the wild underscores the urgency of this update.
The Chrome 128 update not only patches CVE-2024-7971 but also fixes several other high-severity vulnerabilities, including CVE-2024-7964 (Use after free in Passwords) and CVE-2024-7965 (Inappropriate implementation in V8). Including these fixes in both the stable and extended stable channels underscores the urgency with which Google addresses these security concerns.
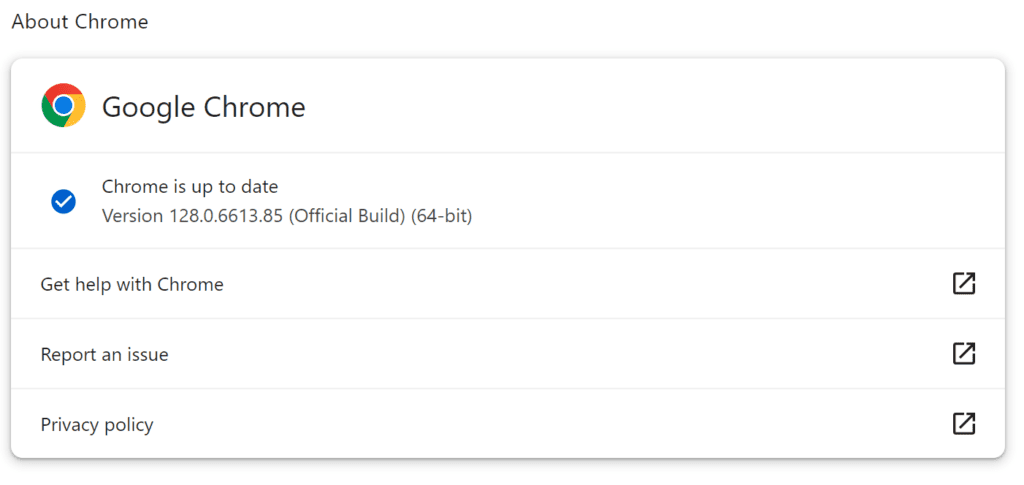
Given the active exploitation of CVE-2024-7971, all Chrome users must update their browsers immediately to version 128.0.6613.84 or higher. Users can manually check for updates by navigating to Chrome’s settings menu, selecting “Help,” and then “About Google Chrome.” The browser will automatically check for updates and prompt a restart once the latest version is installed.
Organizations should also prioritize patching their systems, especially those relying on Chrome in environments where sensitive data is handled. Implementing additional security measures, such as sandboxing and network segmentation, can help mitigate the risks posed by this and other vulnerabilities.