Venator: A Kubernetes-Native Threat Detection Platform for Enhanced Security Posture
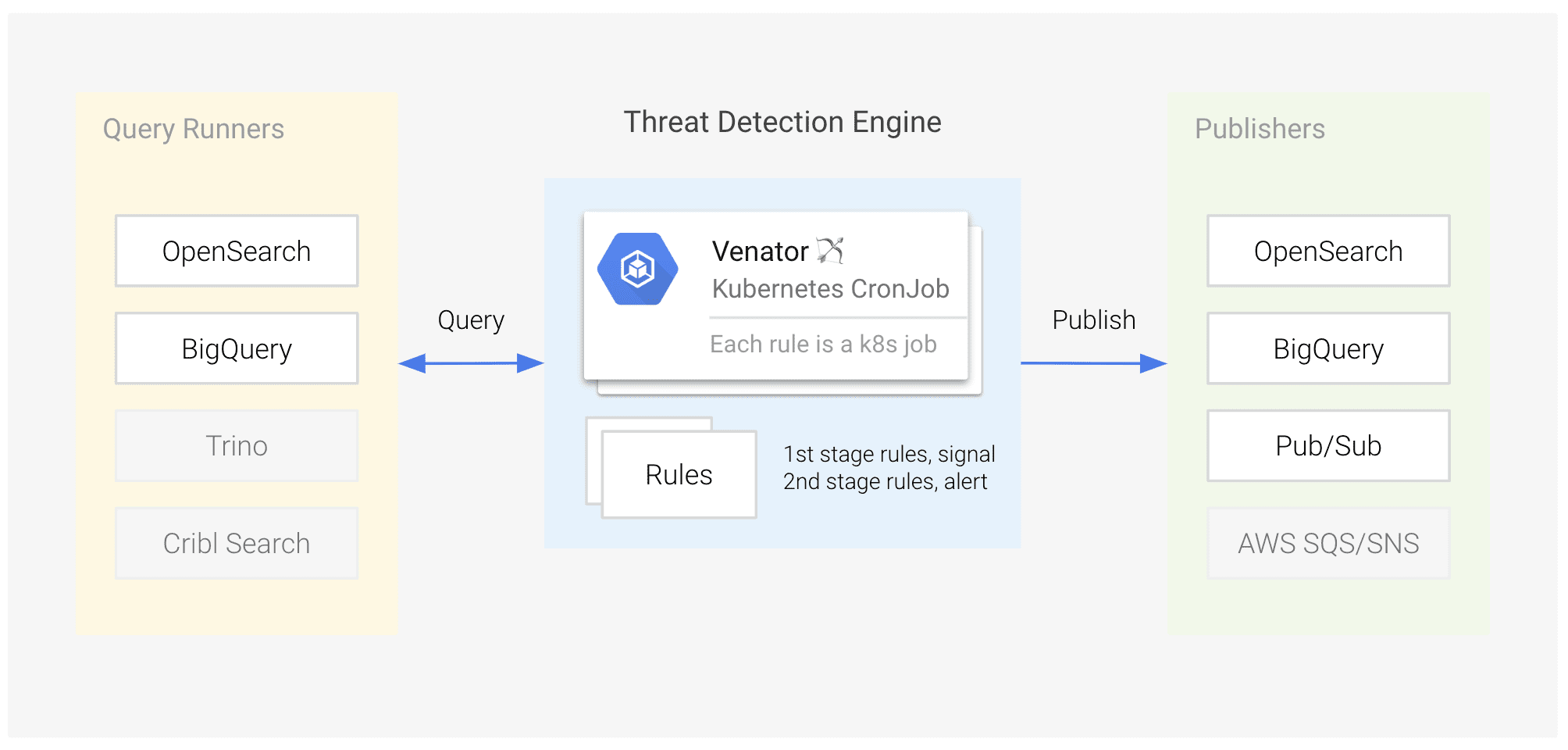
In today’s increasingly complex threat landscape, organizations require agile and scalable security solutions to effectively identify and respond to evolving attack vectors. Venator, an open-source threat detection platform, offers a compelling approach by leveraging the power and flexibility of Kubernetes.
Addressing the Limitations of Traditional Threat Detection
Traditional threat detection solutions often present challenges for security teams, including:
- Cumbersome Rule Management: Updating, testing, and deploying new detection rules can be complex and time-consuming, hindering rapid response to emerging threats.
- Opaque Job Execution: Limited visibility into the execution of detection jobs and troubleshooting failures can impede operational efficiency.
- Vendor Lock-in: Reliance on specific Security Information and Event Management (SIEM) platforms or data sources can restrict flexibility and increase costs.
Venator: A Modern Approach to Threat Detection
Venator introduces a novel paradigm for threat detection, prioritizing simplicity, extensibility, and maintainability. Its core functionalities include:
-
Modular Detection Rules: Detection logic is defined in YAML files, promoting easy creation, modification, and version control. Each rule functions independently, specifying its own query engine (e.g., OpenSearch, Google BigQuery) and publishing destinations (e.g., Slack, Google Cloud Pub/Sub). This modular design ensures fault isolation and facilitates granular control over detection processes.
-
Kubernetes-Native Orchestration: Venator leverages Kubernetes CronJobs for scheduling and executing detection rules. This ensures reliable job execution, seamless scalability, and simplified management. Kubernetes handles resource allocation, failure recovery, and scaling, optimizing resource utilization and operational efficiency.
-
Flexible Querying and Publishing: Venator supports multiple query engines, enabling security teams to analyze data from diverse sources, including OpenSearch, Google BigQuery, and other compatible data lakes. Similarly, it supports various publishing destinations, allowing for flexible dissemination of alerts to Slack, storage of security signals in BigQuery, or triggering automated responses via Google Cloud Pub/Sub.
-
Integrated Exclusion Management: Venator enables the definition of exclusion lists to filter known benign events, minimizing false positives and enhancing the precision of threat detection. This functionality improves the signal-to-noise ratio and reduces alert fatigue for security analysts.
Large Language Model (LLM) Integration: By integrating with LLMs, Venator facilitates advanced signal analysis and correlation. This capability is particularly valuable for analyzing lower-confidence signals and identifying potential threats that may not trigger immediate alerts, enhancing proactive threat hunting and investigation.
-
Automated Deployment with Helm: Venator utilizes Helm charts for automated deployment and configuration management. This streamlines the deployment process, simplifies updates, and ensures consistency across environments.
Advantages of Adopting Venator
- Enhanced Agility: Seamlessly switch between data sources and publishing destinations, mitigating vendor lock-in and adapting to evolving security requirements.
- Streamlined Rule Management: Efficiently create, update, and deploy detection rules with YAML files and automated deployments, accelerating response times to new threats.
- Improved Scalability and Resilience: Leverage Kubernetes for robust job scheduling, execution, and resource management, ensuring high availability and fault tolerance.
- Reduced False Positives: Utilize exclusion lists to filter benign events, optimize detection accuracy, and improve the efficiency of security operations.
- Advanced Threat Analysis: Integrate with LLMs to gain deeper insights into security events, correlate signals, and proactively identify potential threats.
Venator Use Cases
Venator is well-suited for organizations that:
- Utilize Kubernetes for infrastructure deployment and management.
- Require a flexible and extensible threat detection platform to adapt to evolving security needs.
- Seek to avoid vendor lock-in and maintain control over their security data and processes.
- Prioritize simplified rule management, automated deployments, and operational efficiency.
Conclusion
Venator represents a modern, Kubernetes-native approach to threat detection, offering a modular and extensible architecture for enhanced security posture. By streamlining rule management, supporting diverse data sources and publishing destinations, and integrating with LLMs, Venator empowers security teams to effectively detect, analyze, and respond to threats in today’s dynamic threat landscape.
For detailed steps on deploying Venator using Helm and Kubernetes, see the Deployment Guide.



