Vultur Android Malware Spreads Its Wings, Poses Serious Threat to Mobile Users
Security researchers at Fox-IT have uncovered a significantly enhanced version of the Vultur Android banking malware. This updated strain features substantial new capabilities, enabling attackers to exercise greater remote control over compromised devices. Additionally, the malware incorporates improved evasion tactics and encryption, making detection more difficult.
Evolving Infection Vector
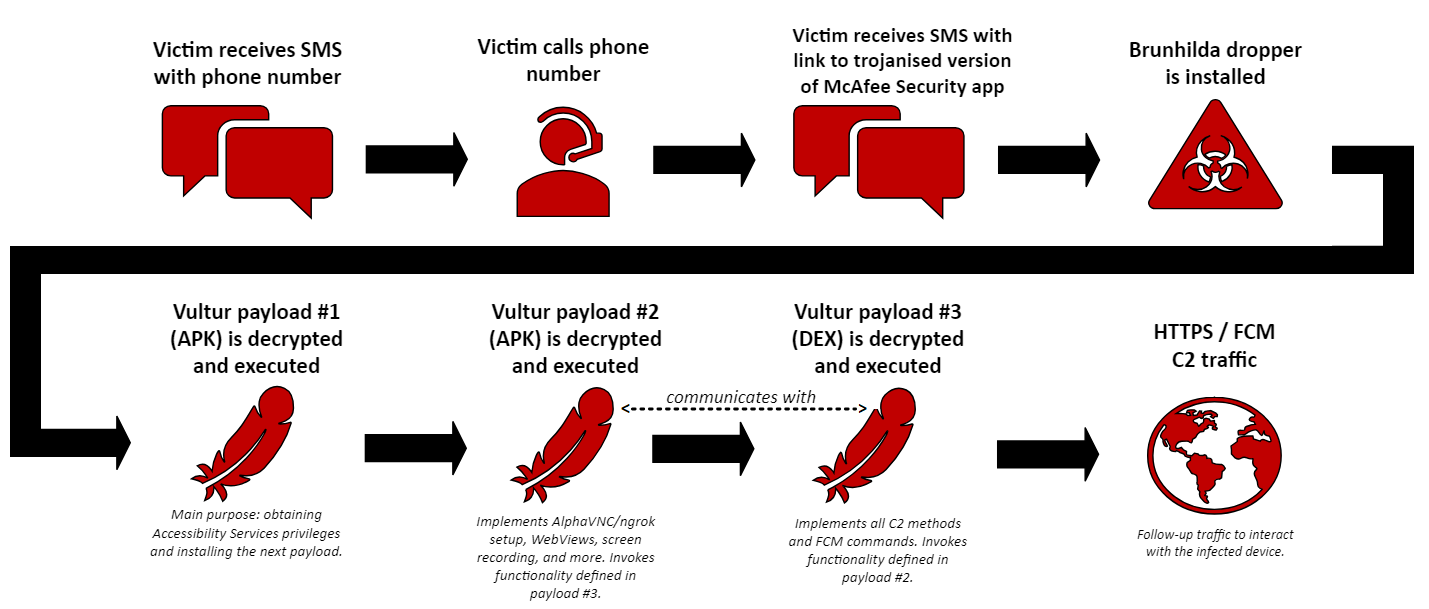
Visualisation of the complete infection chain
Vultur’s distribution now relies on a sophisticated hybrid attack leveraging both SMS and phone calls. Victims receive an alarming SMS message concerning a fraudulent transaction, prompting them to call a provided number. During this call, the attacker directs the victim to install a trojanized version of the McAfee Security app from a link sent via a second SMS. This multi-step approach exploits trust and urgency to lower the victim’s guard.
Upon successful infiltration, Android banking malware employs a three-stage payload delivery system, gradually escalating its control over the device. Each stage introduces additional functionalities, from basic device manipulation to full remote control capabilities, including the innovative use of Firebase Cloud Messaging (FCM) for command execution without maintaining a constant connection to the device.
New Features & Expanded Control
First spotted in March 2021, Vultur has since evolved from its original form. Initially recognized for its screen recording and keylogging prowess, primarily targeting banking applications, Vultur has expanded its toolkit to include functionalities that allow for comprehensive remote interactions with the infected device. These capabilities include downloading, uploading, and managing files, controlling the device using Android Accessibility Services, and even manipulating the device’s volume—all orchestrated remotely, showcasing the malware’s increased flexibility and control.
One of the most alarming updates is Vultur’s ability to disguise itself more effectively. By encrypting its command and control (C2) communication and distributing its malicious payload across multiple stages, Vultur has become a more elusive predator. Its use of AES encryption coupled with Base64 encoding for its C2 interactions further complicates detection efforts.
The updated Vultur now includes:
- Remote Interaction: Through the abuse of Android’s Accessibility Services, attackers can remotely execute taps, swipes, gestures, volume controls, and more, effectively taking over the device.
- File Management: The inclusion of file management functions provides attackers unfettered access to upload, download, delete, and install files on the victim’s device.
- App Blocking: Malware operators can selectively block the victim from using specific apps, often displaying custom error messages to maintain the facade of legitimacy.
These features, alongside Vultur’s existing remote access (via AlphaVNC and ngrok) and keylogging, grant attackers extensive power over compromised devices.
Obfuscation and Evasion
Vultur’s developers have made significant strides in evading detection, from masquerading as legitimate applications to leveraging native code for payload decryption. The strategic use of legitimate package names and the distribution of malicious code across multiple payloads make Vultur a challenging adversary for cybersecurity defenses.
Moreover, the malware’s intricate execution flow, from the initial dropper masquerading as a McAfee app to the final payload unleashing the full spectrum of its malicious functionalities, showcases the advanced tactics employed by cybercriminals to maintain stealth and persistence.
Vultur now demonstrates more advanced obfuscation and anti-analysis measures:
- Traffic Encryption: AES encryption and Base64 encoding of network communications hinder network-based detection mechanisms.
- App Masquerading: The use of modified legitimate apps and well-known package names increases the likelihood of successful infection.
- Native Code Payload Decryption: This complicates reverse engineering efforts.
- Code Fragmentation: The malware’s core functionality is strategically distributed across multiple payloads, making analysis more time-consuming.
The Bottom Line
The Vultur malware’s evolution reminds us that the mobile threat landscape is constantly shifting. By understanding how these attacks work and taking proactive steps, you can significantly lower your risk of infection and help safeguard your online life.
To learn more about Vultur’s capabilities, access indicators of compromise (IOCs), and explore further protective measures, refer to the full Fox-IT report.






