In today’s complex and ever-evolving threat landscape, safeguarding diverse IT infrastructures demands a robust, adaptable security solution. Wazuh, a free and open-source platform, emerges as a powerful tool, delivering end-to-end threat prevention, detection, and response capabilities across on-premises, virtualized, containerized, and cloud-based environments.
What is Wazuh?
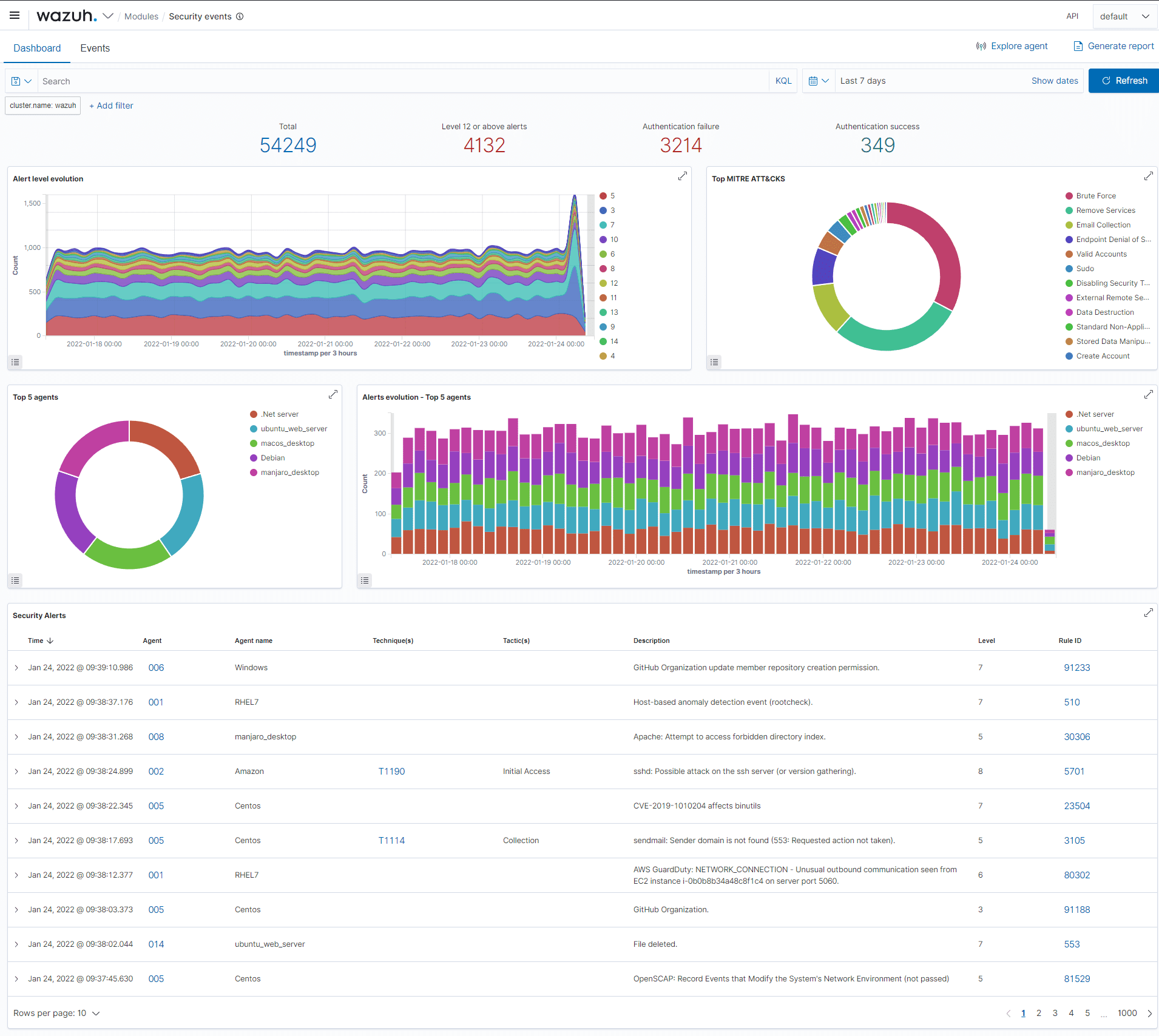
Wazuh is a free, open-source security platform that provides organizations with the tools needed to monitor and protect their IT infrastructure. It combines an endpoint security agent, deployed on monitored systems, with a centralized management server that collects and analyzes data. This setup allows Wazuh to detect threats, monitor system integrity, analyze logs, and ensure compliance with security policies.
One of Wazuh’s strengths is its full integration with the Elastic Stack, a powerful search engine and data visualization tool. This integration enables users to navigate through their security alerts with ease, gaining insights and taking action swiftly.
Core Functionalities and Advantages
-
Multi-Layered Threat Detection: Wazuh deploys lightweight agents to monitored systems, collecting and analyzing a vast array of security data. These agents, working in tandem with a central management server, employ a multi-pronged approach to identify threats:
- Intrusion Detection: Proactive scanning for malware, rootkits, and suspicious anomalies, coupled with signature-based log analysis, enables early detection of compromise.
- Log Data Analysis: Rule-based analysis of operating system and application logs, along with syslog data from network devices, provides deep visibility into security events and operational issues.
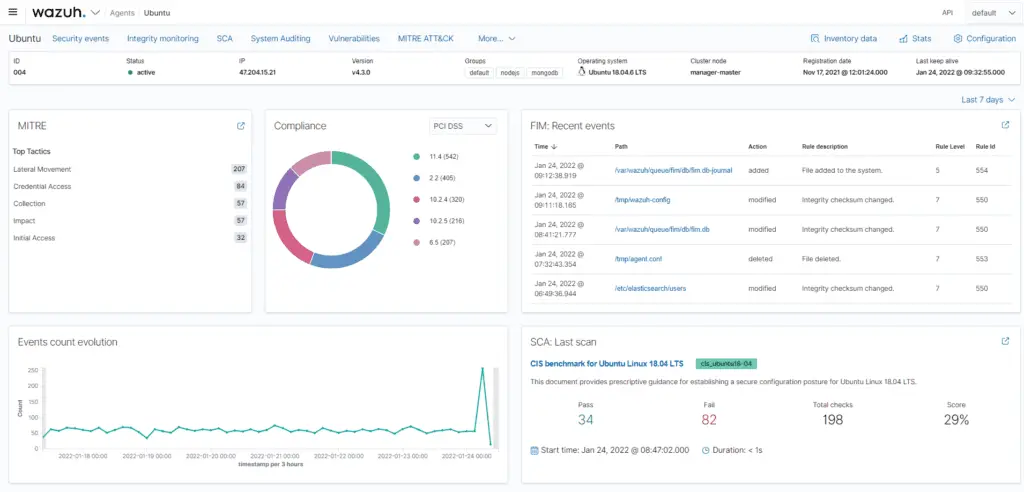
- File Integrity Monitoring: Real-time monitoring of file system changes safeguards critical assets from unauthorized modifications.
- Vulnerability Detection: Continuous correlation of software inventory data with CVE databases allows for prompt identification and mitigation of known vulnerabilities.
- Configuration Assessment: Automated configuration checks ensure compliance with security policies and industry benchmarks, hardening systems against potential exploits.
-
Incident Response and Compliance:
- Active Responses: Pre-defined or custom responses empower automatic countermeasures to threats, minimizing damage and downtime.
- Remote Command Execution: Facilitates real-time investigation and incident response actions.
- Regulatory Compliance: Out-of-the-box security controls and reporting capabilities support adherence to industry standards like PCI DSS and GDPR.
-
Cloud and Container Security:
- Cloud Infrastructure Monitoring: Integration modules for major cloud providers offer API-level visibility into security data.
- Cloud Configuration Assessment: Rules for assessing cloud environment configurations help identify and address weaknesses.
- Container Security: Native Docker engine integration enables continuous monitoring and analysis of container behavior, image integrity, and potential vulnerabilities.
Wazuh Architecture:
- Agent-Based Deployment: Scalable endpoint agents collect data from diverse operating systems and environments.
- Centralized Management: A central server aggregates, analyzes, and correlates data, presenting a unified security view.
- Elastic Stack Integration: Leverages Elasticsearch for powerful search, Kibana for visualization, and other Elastic Stack components for log management and security analytics.
Conclusion
Wazuh represents a powerful and versatile open-source solution for organizations seeking to elevate their security posture. Its extensive capabilities, flexible deployment options, and robust integration capabilities make it a formidable ally in combating cyber threats. By leveraging Wazuh’s multi-layered protection, organizations can achieve comprehensive visibility, proactive threat detection, and streamlined incident response, ensuring the confidentiality, integrity, and availability of their critical assets.
To learn more about Wazuh, including installation guides and usage tutorials, visit wazuh.com.