WezRat: The Modular Infostealer Weaponized by Iranian Cyber Group Emennet Pasargad
In a comprehensive analysis released by Check Point Research (CPR), the WezRat infostealer has been identified as a sophisticated tool in the arsenal of the Iranian cyber group Emennet Pasargad, linked to the Iranian Islamic Revolutionary Guard Corps (IRGC). This malware has been actively deployed in cyber campaigns across the United States, Europe, and Israel, with its most recent operation targeting Israeli organizations through phishing campaigns impersonating the Israeli National Cyber Directorate (INCD).
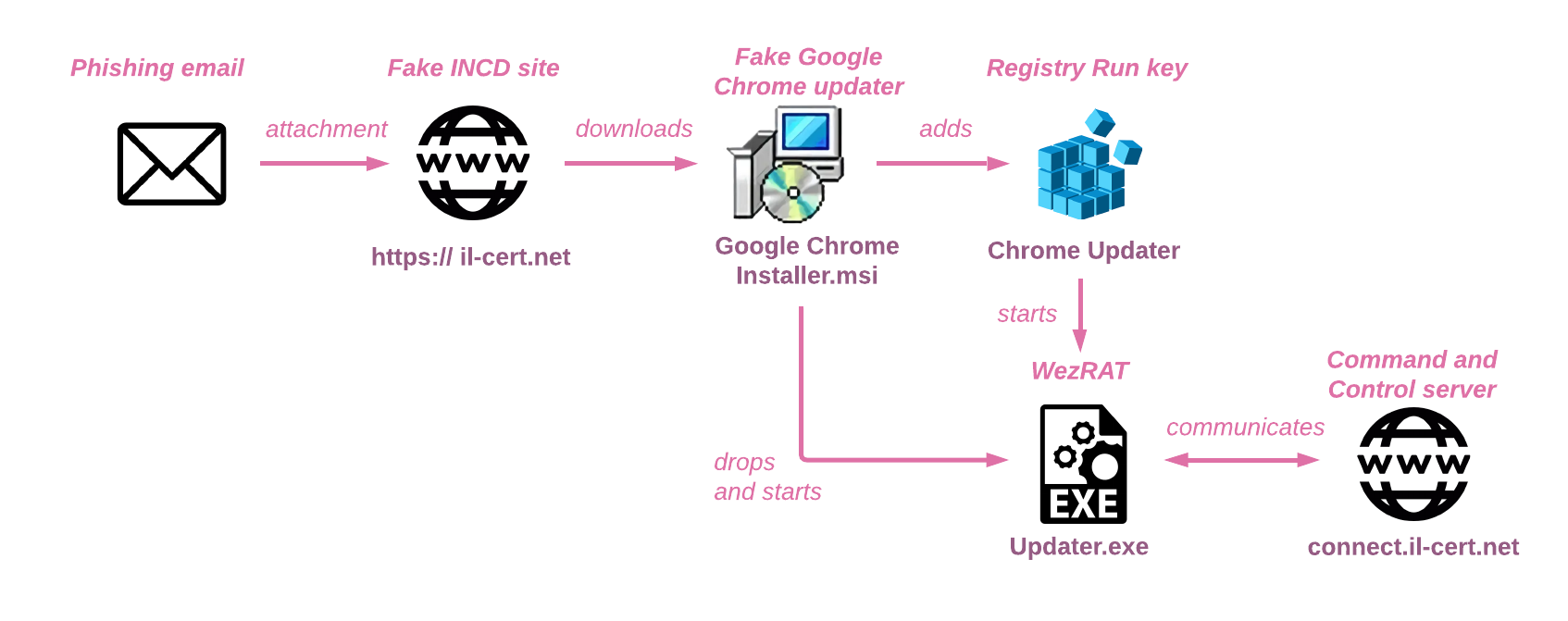
On October 21, 2024, multiple phishing emails disguised as official INCD alerts urged recipients to update their Google Chrome browsers. These emails originated from the fraudulent domain alert@il-cert[.]net, which mimicked legitimate INCD websites. Victims were tricked into downloading a malicious file, Google Chrome Installer.msi, which not only contained the legitimate Chrome installer but also executed WezRat’s payload.
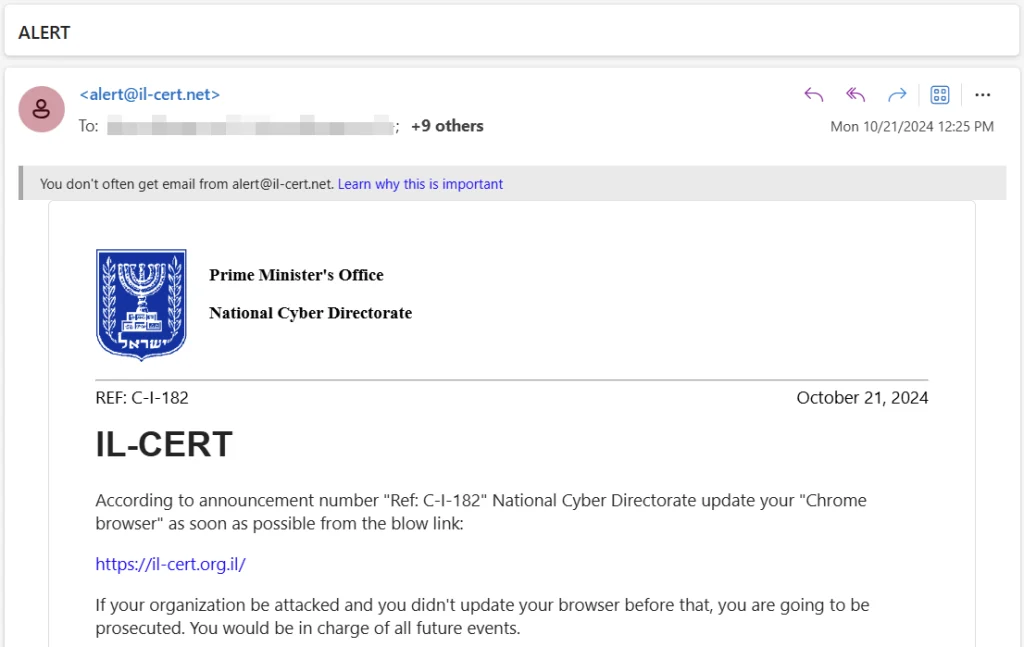
Phishing email sent to Israeli recipients | Image: Check Point
The infection chain was designed to avoid suspicion. According to CPR, “The downloaded MSI contains the legitimate Google Chrome installer and related files, but it also drops a backdoor named Updater.exe and executes it.” This clever masquerade enabled attackers to compromise targets while maintaining an illusion of legitimacy.
WezRat is a modular infostealer with extensive functionalities, including:
- Command Execution: Enables attackers to remotely execute commands on infected systems.
- Screenshot Capture: Uses a custom DLL module to take screenshots and upload them to the command and control (C2) server.
- Keylogging: Employs a specialized DLL to log keystrokes, which are stored locally before being exfiltrated.
- Clipboard and Cookie Theft: Targets sensitive clipboard data and cookies from Chromium-based browsers.
- File Upload and Download: Facilitates data exfiltration and payload delivery via the C2 server.
CPR highlights the malware’s evolution: “WezRat initially functioned more as a simple Remote Access Trojan with basic commands. Over time, additional features such as screenshot capabilities and a keylogger were incorporated and handled as separate commands.”
The malware’s backend infrastructure reflects significant technical investment. Its C2 servers use obfuscated communication protocols and dynamically adjust functionality to avoid detection. Early versions of WezRat relied on hardcoded C2 addresses, while newer iterations use more advanced techniques, including obfuscated DLLs and encrypted string handling.
CPR notes, “The backdoor collects system information such as user profile path, IP address, and computer name, which it combines into a bot ID using a hashing algorithm.” This bot ID is then registered with the C2 server.
The FBI, US Department of Treasury, and INCD have attributed WezRat to Emennet Pasargad, a group known for its cyber and disinformation campaigns. The group has carried out operations under various aliases, including Anzu Team and For-Humanity, and has a history of blending political messaging with cyberattacks.





