wifite2 v2.7 releases: new version of the popular wireless network auditor, “wifite”

Wifite 2
A complete re-write of wifite, a Python script for auditing wireless networks.
Wifite runs existing wireless-auditing tools for you. Stop memorizing command arguments & switches!
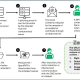
Wifite is designed to use all known methods for retrieving the password of a wireless access point (router). These methods include:
- WPS: The Offline Pixie-Dust attack
- WPS: The Online Brute-Force PIN attack
WPS: The Offline NULL PIN attack - WPA: The WPA Handshake Capture + offline crack.
- WPA: The PMKID Hash Capture + offline crack.
- WEP: Various known attacks against WEP, including fragmentation, chop-chop, aireplay, etc.
- WIFI Signal jammer, block specific accesspoints or multiple. signal jamming only works for specific Atheros WiFi chipsets.
Run wifite, select your targets, and Wifite will automatically start trying to capture or crack the password.
Brief Feature List
- PMKID hash capture (enabled by-default, force with:
--pmkid) - WPS Offline Brute-Force Attack aka “Pixie-Dust”. (enabled by-default, force with:
--wps-only --pixie) - WPS Online Brute-Force Attack aka “PIN attack”. (enabled by-default, force with:
--wps-only --no-pixie) - WPA/2 Offline Brute-Force Attack via 4-Way Handshake capture (enabled by-default, force with:
--no-wps) - Validates handshakes against
tshark,cowpatty, andaircrack-ng(when available) - Various WEP attacks (replay, chopchop, fragment, hirte, p0841, caffe-latte)
- Automatically decloaks hidden access points while scanning or attacking.
- Note: Only works when channel is fixed. Use
-c <channel> - Disable this using
--no-deauths
- Note: Only works when channel is fixed. Use
- 5Ghz support for some wireless cards (via
-5switch).- Note: Some tools don’t play well on 5GHz channels (e.g.
aireplay-ng)
- Note: Some tools don’t play well on 5GHz channels (e.g.
- Stores cracked passwords and handshakes to the current directory (
--cracked)- Includes information about the cracked access point (Name, BSSID, Date, etc).
- Easy to try to crack handshakes or PMKID hashes against a wordlist (
--crack)
Support
Wifite is designed specifically for the latest version of Kali Linux. ParrotSec is also supported.
NetHunter (Android) is also widely supported by wifite, but it will require a custom kernel with modules support and various patches for injection in order to work. Tested working like a charm on Android 10 (Q), Android 11 (R) and Android 12 (S).
Changelog v2.7
- Fix coWPatty support. Finally working again.
- Allow airodump-ng to exit & get reaped
- Supports latest hcxdumptool (v6.3.0) instead of older
- Updated Dockerfile to use Debian Bookworm.
- Updated the README.md
Installing & Running
$ git clone https://github.com/kimocoder/wifite2.git
$ cd wifite2
$ pip3 install -r requirements.txt
$ sudo ./wifite.py
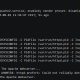
Decloaking & cracking a hidden access point (via the WPA Handshake attack):
Cracking a weak WEP password (using the WEP Replay attack):
Various cracking options (using --crack option):
Copyright (C) 2017 derv82
Source: https://github.com/derv82/