WikiKit Phishing Kit Targets Major Industries with Evasive Techniques

TRAC Labs recently unveiled a new phishing kit, named WikiKit, which is targeting industries across automotive, manufacturing, medical, and more. This sophisticated attack employs unique techniques to evade detection and gain user trust.
WikiKit derives its name from an unusual feature: if JavaScript is disabled or the phishing link is invalid, the user is redirected to legitimate Wikipedia pages. This clever fallback mechanism reduces suspicion and demonstrates the kit’s innovation. The campaign began in October 2024, and it has targeted various industries, including automotive, manufacturing, medical, construction, consulting, and entertainment.
“What is distinctive about the WikiKit phishing campaign is its use of landing pages hosted on Jimdosite, featuring the targeted company’s logo in the background,” TRAC Labs explains in their report. These landing pages prompt victims to click on a “Review Document Here” button, which redirects them to a credential-harvesting page.
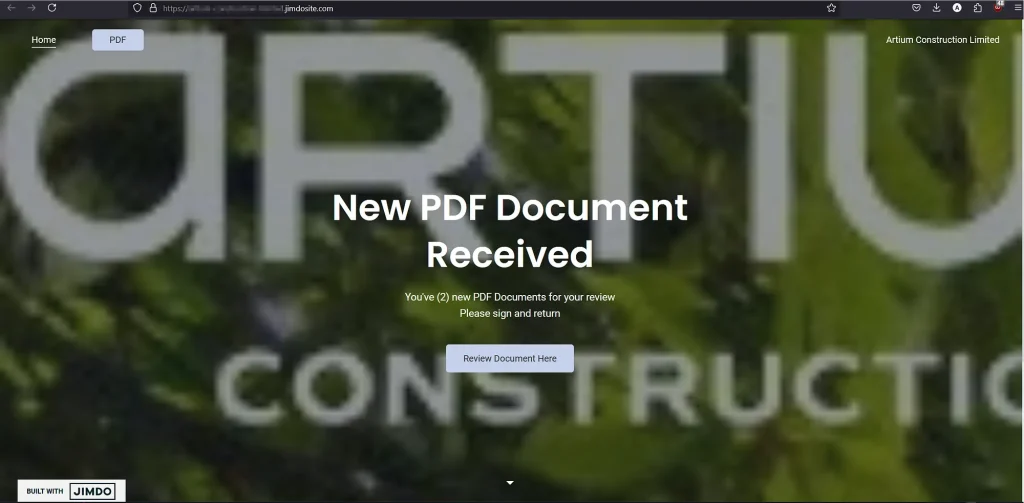
Landing page | Source: TRAC Labs
The campaign employs multiple layers of social engineering:
- Spoofed Links: Emails from compromised accounts contain links resembling legitimate Salesforce URLs, such as hxxps://app.salesforceiq[.]com/r?… This technique fosters trust among victims.
- Dynamic Branding: Upon entering an email address, the phishing page dynamically adjusts its branding based on the victim’s details, using retrieved logos and backgrounds to mimic legitimate platforms.
- CAPTCHA Validation: Victims are required to pass a Cloudflare Turnstile CAPTCHA, adding an air of legitimacy.
The phishing flow cleverly uses href.li, an anonymizing service, to redirect users to Wikipedia if tampering or debugging is detected. Examples include links like:
- https://en.wikipedia.org/wiki/Category:Office_365
- https://en.wikipedia.org/wiki/List_of_Microsoft_365_Applications
WikiKit incorporates several counter-analysis strategies:
- Debugging Deterrence: The phishing code includes regex-based checks and obfuscated JavaScript to detect and disrupt analysis. For example, one regex identifies suspicious loops introduced by debugging tools, halting execution when tampering is detected.
- Console Manipulation: By overriding browser console methods like
log,warn, anderror, WikiKit prevents analysts from observing its activity through developer tools.
TRAC Labs notes, “The script ensures the user is only presented with the default authentication method,” complicating detection efforts further.
The phishing kit leverages URLs hosted on domains like jimdosite.com and yugaljeeautomotive[.]com to carry out its attacks. Organizations are advised to monitor for these and similar indicators, bolstering their defenses against evolving phishing campaigns.
Related Posts:
- Critical Zero-Day Automotive Systems Vulnerabilities Exposed
- Critical EoP Flaw in Microsoft’s Remote Registry: Researcher Publishes PoC for CVE-2024-43532
- The Rise of Fake Online Meeting Websites Spreading Android and Windows RATs
- Beware! Fake Notion Installer Spreads Data-Stealing Malware
- Doctors warn that medical implants may be the hacker’s future goals





