Winos4.0 Malware Spread Through Game Apps Targets Education Sector
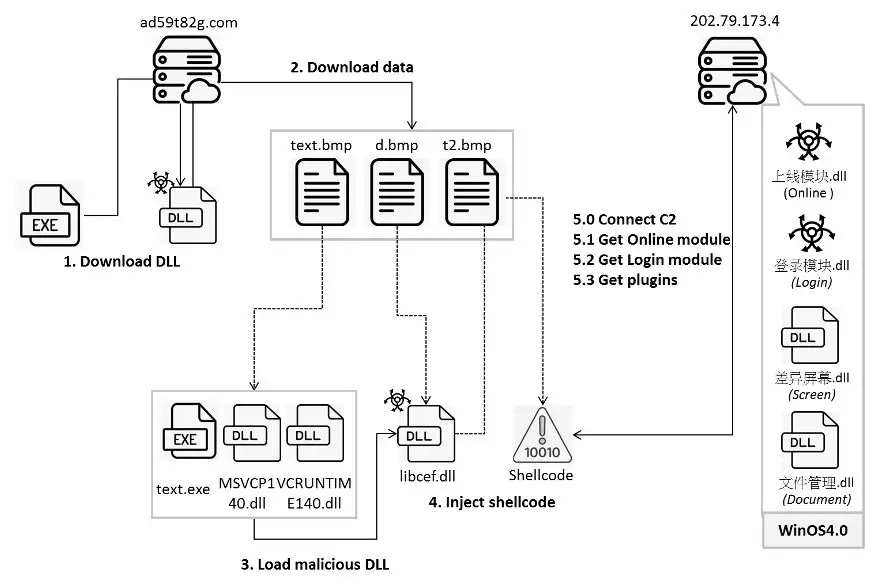
The advanced Winos4.0 malware framework has been found targeting unsuspecting users through game-related applications, according to a report by FortiGuard Labs. Disguised as innocuous software like installation tools and performance boosters, this malware exhibits a highly modular design, enabling it to carry out extensive actions on infected systems.
Winos4.0 is a powerful evolution of the Gh0strat malware, now with enhanced functionality and a more stable architecture for executing remote commands. The malware has already been linked to previous campaigns, such as the Silver Fox operation, and was discovered hidden within various game applications. These apps, once installed, retrieve and decode a fake BMP file to install malicious components. FortiGuard Labs explained, “Winos4.0 is an advanced malicious framework that offers comprehensive functionality, a stable architecture, and efficient control over numerous online endpoints to execute further actions.”
Malicious game-related applications | Image: FortiGuard Labs
In this particular campaign, the threat actor used the domain ad59t82g[.]com to download malicious BMP files and DLLs, which enable Winos4.0’s advanced actions. The malware’s DLL, aptly named “you.dll,” initiates its installation by creating a random directory in the Program Files folder. This DLL downloads multiple files using encryption and encoding, disguising its presence and evading detection. The file descriptions, such as “校园政务” (Campus Administration), suggest a focus on education-related targets.
Once installed, Winos4.0 establishes persistence through registry modifications, ensuring it relaunches on system reboot. This involves adding an executable to the “SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN” registry key under the name “WINDOWS.” The report further noted that “the malicious DLL ‘libcef.dll’ decodes ‘t5d.tmp’ using an XOR key” and injects shellcode to execute additional actions, including loading other malicious modules from its command-and-control (C2) server.
The sophistication of Winos4.0 extends to its ability to check for system monitoring software, clipboard data logging, and crypto wallet detection. It can capture information from MetaMask and OKX Wallet, allowing attackers to access sensitive user data. This malware also collects comprehensive system information, including IP addresses, computer names, and even CPU details, and transmits it to the C2 server.
The Winos4.0 campaign showcases the adaptability of modern malware frameworks and serves as a reminder of the risks associated with downloading software from unverified sources.
Related Posts:
- Beware of Search Results: Hackers Using Fake Websites to Spread Malware
- Hackers Exploit Google Ads to Target Admins with Fake Software Downloads
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Hackers Fake ChatGPT App to Spread Windows, and Android Malware
- Zoom Phishing Alert: Researcher Identifies New Threat Targeting Microsoft Accounts





