wireless ids: etect suspicious activity such as (WEP/WPA/WPS) attack
Wireless IDS [Intrusion Detection System]
Wireless IDS is an open source tool written in Python and work on Linux environment. This tool will sniff your surrounding air traffic for suspicious activities such as WEP/WPA/WPS attacking packets. It does the following
- Detect mass deauthentication sent to client/access point which unreasonable amount indicate possible WPA attack for handshakes.
- Continual sending data to access point using broadcast MAC address which indicates a possibility of WEP attacks
- Unreasonable amount of communication between wireless client and access point using EAP authentication which indicates the possibility of WPS bruteforce attack by Reaver / WPSCrack
- Detection of changes in connection to another access point which may have the possibility of connection to Rogue AP (User needs to assess the situation whether similar AP name)
- Detects possible Rogue Access Point responding to probe by wireless devices in the surrounding.
Newly Added !!!!
- Display similar Access Point’s name (SSID) which could have the possibility of WiFi ‘Evil Twins’.
- Display of probing SSID by wireless devices
- Detection of Korek Chopchop packets sent by Aircrack-NG (WEP attacks)
- Detection of Fragmentation PRGA packets sent by Aircrack-NG (WEP attacks)
- Detection of possible WPA Downgrade attack by MDK3
- Detection of possible Michael Shutdown exploitation (TKIP) by MDK3
- Detection of Beacon flooding by MDK3
- Detection of possible Authentication DoS by MDK3
- Detection of possible association flooding
- Detection of WPA Migration Attack by Aircrack-NG (WPA Attack)
- Allow logging of events to file.
- Allow disabling of displaying of probing devices
- Setting of scanning count..
Installation
Requirements
Before installing the script, please make sure you have the following done.
- root access (admin)
- wireless interface which is capable of monitoring
- Python 2.7 < installed
- Aircrack-NG suite installed
- TShark installed
Download/Installation
- Save the file ‘wids.py‘ to your Linux Desktop or any directory you like. For my case, i saved it on my desktop and enter the following in the terminal console.
- cd Desktop/
- chmod +x wids.py or sudo chmod +x wids.py (if you not running as root)
- ./wids.py
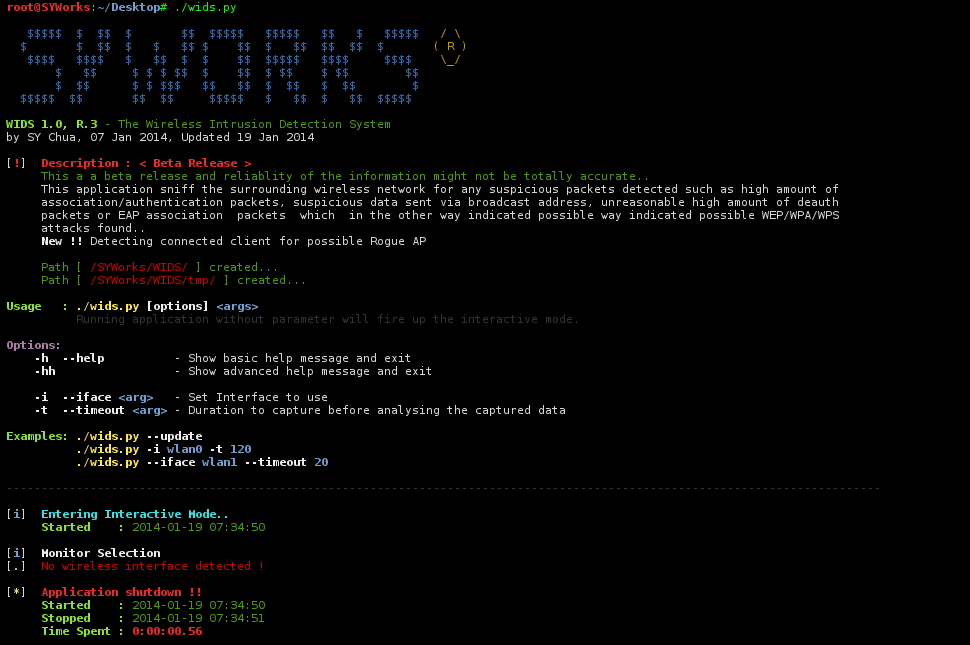
Once installed, you may wish to delete the file where you have initially saved as the following had be created:
- Directory – ~/SYWorks/
- Directory – ~/SYWorks/WIDS/
- Directory – ~/SYWorks/WIDS/tmp
- File – ~/SYWorks/WIDS/wids.py
- File – ~/usr/sbin/wids.py
You can also download the MAC OUI Database at here if you want WIDS to detect the manufacturer of the wireless devices
Running The Script
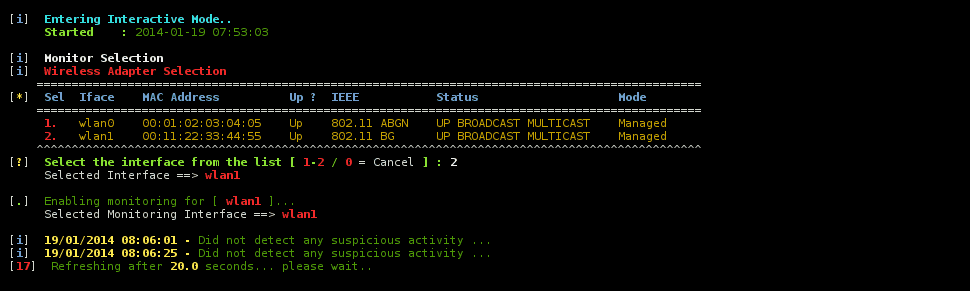
- You can run the script at any directory by entering ‘wids.py‘ (After installation).
- Once the script is running, it will detect the wireless interface that you have and if you have more than one interface, it will prompt you for the response.
- If there is no suspicious activity found, it will display ‘Did not detect any suspicious activity..‘
Note: If you want to exit the script, simply hit on ‘Ctrl+C‘ to exit the application.

Tutorial
Copyright (C) 2014 SYWorks
Source: https://github.com/SYWorks/





